Network controllers
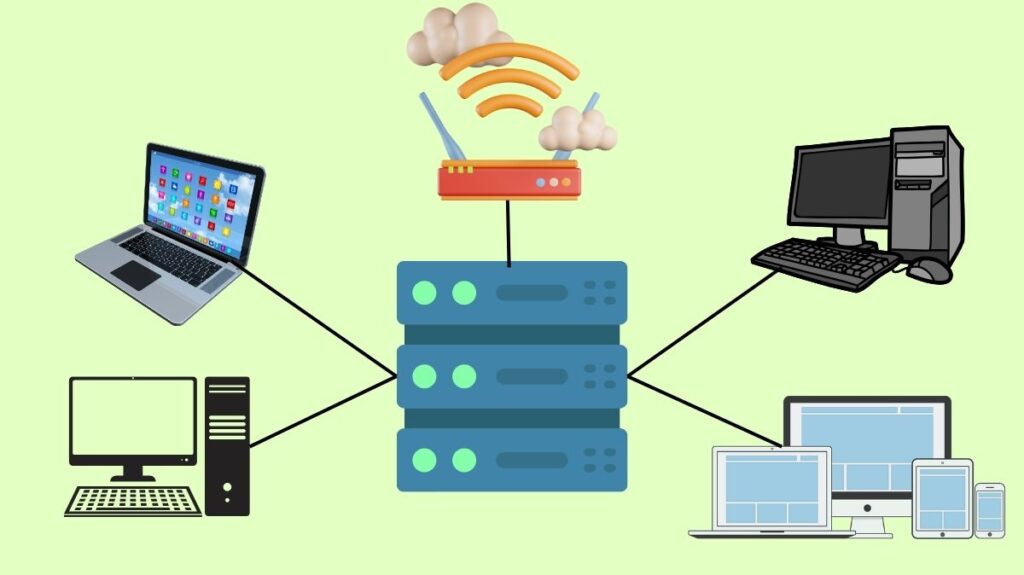
The control plane activities in networking are housed in network controllers, which are centralized applications or administrative organizations. They serve as the network’s brain, deciding how traffic should flow and managing and coordinating all of the many components, including storage, software-defined, wired, and wireless networks. Their centralization sets them apart from conventional networks, which disperse control functions among many devices.
Role and Function of Controllers
In the past, the operating system of each device included the control plane, which handles functions like computing and managing Layer 2 and Layer 3 data structures (such as ARP and routing tables). These control plane functions are transferred to a centralized controller, usually software operating on a server (physical or virtual), with Software-Defined Networking (SDN) and controller-based architectures.
Also Read About What Are Layer 2 Switches And How Does Layer 2 Switch Work
Devices’ dispersed control plane functions can be fully replaced by controllers, or they can simply be aware of the devices’ continuous activities without making any changes. The degree and kind of control they exert over networking devices are centralised. Through programmatic access, this architecture facilitates network programmability, allowing for faster development and management.
How Network Controllers Work
A network controller centralizes this decision-making process, as opposed to traditional networks where each device bases its forwarding choices on its local routing table (a distributed control plane). After acquiring a comprehensive, worldwide perspective of the network’s topology and traffic requirements, it programs the forwarding rules onto specific network devices, which merely carry out these directives. The fundamental idea of SDN is this centralization.
Components of Controller Architecture
Three planes are commonly used to classify network functions:
Data Plane: Manages traffic from end users moving through network equipment. The controller directly programs the data plane entries into device tables in certain SDN implementations.
Control Plane: The control plane is responsible for overseeing and managing the forwarding tables that the data plane uses. This covers protocols such as switch MAC address learning, OSPF, EIGRP, RIP, BGP, IPv4 ARP, IPv6 NDP, and STP. This plane is logically centralized in networks that rely on controllers.
Management Plane: Network engineers can manage, configure, and keep an eye on network devices using the protocols and techniques that make up the management plane. This plane includes protocols such as Syslog, SNMP, SSH, and Telnet. It carries out overhead operations that have no direct impact on the data plane.
Controllers use northbound interfaces (NBIs) to engage with applications and southbound interfaces (SBIs) to connect with the network infrastructure.
Southbound Interfaces (SBIs): Often logically “below” the controller in network diagrams, these interfaces enable the controller to interact with and program networking devices. OpenFlow, OpFlex, CLI (Telnet/SSH), SNMP, NETCONF, and RESTCONF are a few examples.
Northbound Interfaces (NBIs): Usually APIs (Application Programming Interfaces), these interfaces allow applications to communicate with the controller by retrieving data and configuring network operations. For this, REST-based APIs and data formats like XML and JSON are frequently utilized.
Also Read About What Is A Layer 3 Switch? And Advantages Of Layer 3 Switch
Types of Controllers
WLCs, or wireless LAN controllers
- WLCs use the Control and Provisioning of Wireless Access Points (CAPWAP) or Lightweight Access Point Protocol (LWAPP) to manage lightweight APs (LAPs). Central configuration and control are handled by the WLC, while 802.11 wireless operations are handled by LAPs.
- This is referred to as a split-MAC architecture, in which the WLC does central administration tasks and the LAP handles client-level MAC duties.
- WLCs interact with RADIUS servers utilising 802.1X to act as an intermediary for client authentication.
- They facilitate management access through console, RADIUS, TACACS+, HTTP, HTTPS, SSH, and Telnet.
- WLCs have redundancy ports, distribution system ports (which can create a Link Aggregation Group (LAG) for load balancing and redundancy, much like EtherChannel), and physical service ports. Management, redundancy management, virtual, service port, and dynamic interfaces are examples of logical interfaces.
- WLCs usually prohibit management traffic coming from a WLAN for security reasons; wired interfaces are preferable.
SDN Controllers
- OpenDaylight Controller: Linked to the Open Networking Foundation (ONF) paradigm of SDN, it centralizes the majority of control plane operations and employs OpenFlow as its SBI.
- Cisco Open SDN Controller (OSC): The OpenDaylight controller’s commercial version from Cisco.
- Cisco’s data centre SDN solution is called Cisco Application Centric Infrastructure (ACI). Instead of using conventional device-by-device configuration, it operates with notions like endpoint groups and policies using the Application Policy Infrastructure Controller (APIC) as its central controller. ACI implements a somewhat centralized control plane and uses OpFlex as its SBI.
- An older Cisco enterprise SDN controller is the Cisco APIC Enterprise Module (APIC-EM). It communicates with the administration plane (via Telnet, SSH, and SNMP) to indirectly affect device operations rather than directly programming the data or control planes. It doesn’t centralize the control plane or alter the way control planes of devices function. Cisco DNA Centre now incorporates many of its features.
- Cisco Software-Defined Access (SDA) architectures are controlled by the Cisco DNA Centre (DNAC). For conventional devices, it also serves as a complete network administration platform. SBIs such Telnet/SSH, SNMP, NETCONF, and RESTCONF are supported by DNA Centre. By serving as a network activity controller, it makes strong functionality possible and streamlines policy management, such as ACLs.
Storage Controllers
Control the flow of data between network servers and storage devices to guarantee effective access and data transmission in storage area networks (SANs).
Domain Controllers
They manage user logins, group policies, and security rights in Microsoft Windows networks, authenticating and authorizing people and devices.
Industrial & IoT Network Controllers
Used in industrial automation and Internet of Things networks to manage sensors, devices, and actuators through specialist protocols, allowing for centralized data gathering and monitoring.
Advantages of Controller-Based Networking
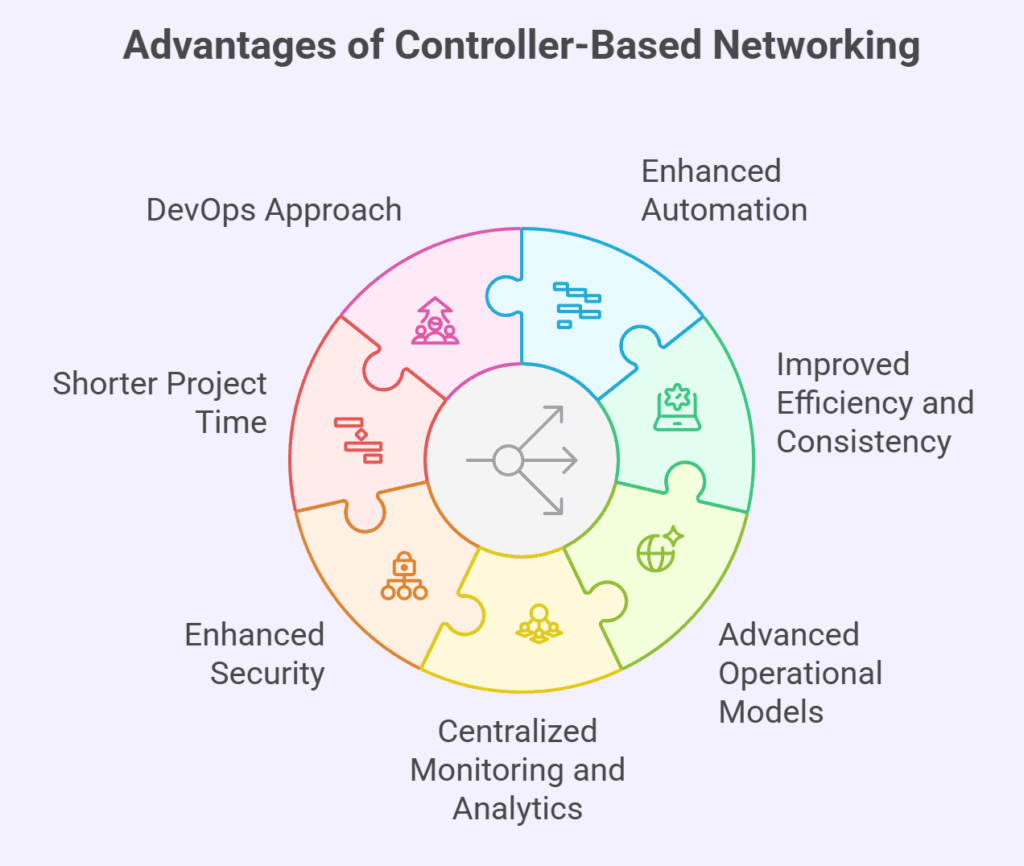
Compared to typical networks, the use of controllers has the following advantages:
Enhanced Automation
By formalizing data models for network configuration and operational data, centralized controllers greatly simplify automation using northbound APIs. This makes it possible to automate tasks that previously challenging without controllers.
Improved Efficiency and Consistency
Network engineers are able to effectively handle thousands of devices. Faster, more reliable modifications with fewer mistakes and less troubleshooting time result from the controller configuring devices with standardized and simplified settings.
Advanced Operational Models
Controllers make it possible for new operational models, such intent-based networking, in which the network is set up according to intended results (like endpoint groups and policies in ACI) as opposed to commands unique to individual devices. External inputs such as network load and time of day can be incorporated into these models.
Centralized Monitoring and Analytics
By offering a centralized repository for all network data, controllers enable contemporary data analytics and previously invisible actionable insights.
Enhanced Security
By centralizing firewall operations for wireless traffic, for example, controller-based networks can improve security.
Shorter Project Time
Network projects can be finished much faster when automation is provided by controllers.
DevOps Approach
A DevOps approach to network administration is facilitated by controllers.
Also Read About IPv4 Address Exhaustion: Simple Guide To IP Address Shortage
