Storage Controller

In networking, a storage controller is an essential piece of hardware or software that controls data flow between storage devices and servers (or host systems). It serves as an interface, converting operating system commands into storage device-specific instructions and managing a number of activities to guarantee effective data storage, retrieval, and protection over a network. In settings such as Network Attached Storage (NAS) and Storage Area Networks (SANs), these controllers are essential. They are sometimes referred to as storage processors or disc controllers.
The following describes the main functions of storage controllers in networking:
How Storage Controllers Work
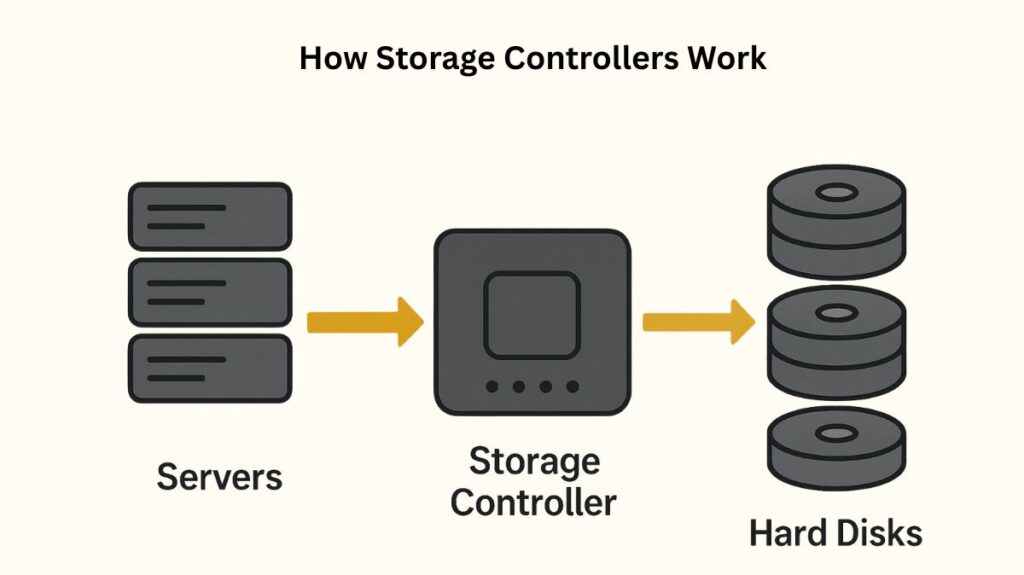
The physical storage media (such as HDDs, SSDs, and storage arrays) and the host system (such as a server) are separated by storage controllers. There are multiple steps involved in their operation in a networked environment:
- Interface and Translation: By acting as a bridge, the controller receives commands from the host’s operating system, including read, write, and format.
- Command Conversion: It transforms these general commands into a protocol and format that are compatible with the particular storage device.
- Data Management: By utilizing capabilities like Direct Memory Access (DMA), which allows I/O operations to be carried out independently of the host CPU, the controller controls the flow of data.
- Network Communication: The controller in a networked configuration helps the host and storage device communicate with each other via the network.
Also Read About Importance Of Computer Network Security Protect Your Data
What is the function of a storage controller?
Storage controllers carry out a number of tasks to guarantee data integrity and maximise performance:
Redundancy (RAID) role
- To reduce data loss, RAID (Redundant Array of Inexpensive Discs) was created.
- A single disc controller card connects to two identical drives in RAID 1 (disc mirroring), which provides redundancy by writing data to both drives at the same time. This one controller, though, might be a single point of failure.
- By adding a second controller, RAID 1 (duplexing) enhances mirroring. Faster parallel data writing is made possible by this fault tolerance for both the data and the disc controllers, albeit at a higher cost.
Data Transfer Management
In order to guarantee prompt and effective data reading and writing, they optimize transfer rates as they manage the data movement between the computer’s memory and storage devices.
I/O Scheduling
Controls the input/output processes’ priority and order.
Data Protection and Redundancy
By managing intricate computations for data striping, mirroring, and parity, technologies like RAID (Redundant Array of Independent Discs) enhance performance and guard against data loss. Another data protection technique that provides comparable levels of security to RAID but in a data-centric manner is erasure coding.
Caching
This technique greatly increases read and write speeds by temporarily storing frequently accessed data in a quick, built-in memory (cache). Certain controllers dynamically manage cache without requiring user input.
Volume Management
Organising storage into logical volumes or units that are network-shareable is known as volume management. These can be “thin” (using space as data is written) or “thick” (reserved capacity). Although volume sets don’t provide data redundancy on their own, they can combine physical units to create larger storage spaces.
Hardware Offload
This technique lessens the load on the host CPU and lowers latency by using specialized hardware to perform specific requests.
Interface compatibility
Guarantees smooth communication between various storage device types (such as SATA, SAS, and NVMe) and the host system.
Protocol Handling
Facilitates networking and storage technologies such NVMe over Fabrics, Fibre Channel, and iSCSI.
Performance optimization
To speed up data access, caching, load balancing, and tiering are used.
Virtualization
This enables servers to view several physical discs as a single logical storage pool.
Security
Provides safe data management by enforcing authentication, access control, and encryption.
Monitoring and Reporting
These frequently offer information about the condition, functionality, and health of storage devices, which is crucial for preventative maintenance.
Also Read About What A Network Is And What Are Benefits Of Networking
Types and Locations in Networking
The implementation and function of storage controllers vary, frequently based on the network architecture:
- Front-end controllers: Manage host memory access and reside on the host system or server.
- Back-end controllers: These are found inside the array or storage device and offer direct access to the actual storage media.
- RAID Controllers: These are specialized controllers made to manage several discs in RAID setups for improved fault tolerance and performance. They may be software-based solutions or hardware cards.
- Host Bus Adapters (HBAs): These devices connect a host system to storage devices, although they usually don’t have sophisticated RAID or caching features.
- Storage Array Controllers: Larger, business-class storage systems contain storage array controllers. These controllers may function in pairs for high availability and failover, and they are frequently a component of a specialized appliance (such as a SAN or NAS). In essence, they are servers that are solely responsible for overseeing a vast array of storage devices, offering redundancy and data services.
- SAN Controllers: Block-level storage in a Storage Area Network (SAN) is managed by SAN controllers, which enable servers to access it over fast networks. High-performance, specialised networks called SANs make it easier for data to flow between servers and storage resources, thereby virtualising storage.
- NAS Controllers: File-level storage is managed by NAS Controllers, which are housed inside Network Attached Storage (NAS) appliances and offer shared access via an Ethernet network. NAS stands for network-attached storage devices, which are mostly used for client data backup and storage.
- Software-Defined Storage Controllers: These can be software-based parts of cloud-native systems that provide storage services and abstract hardware.
- Hybrid/Cloud Storage Controllers: For scalability, combine cloud-based services with on-premise storage.
- SAS (Serial Attached SCSI) Controllers: Control communication with SAS-based storage devices, which are frequently utilised in business settings that require dependable and fast data transfer.
- SATA (Serial ATA) Controllers: Control communication with SATA-based storage devices, which are appropriate for small-scale server applications and general-purpose computing. These devices are frequently built into motherboards.
Benefits of Storage Controllers
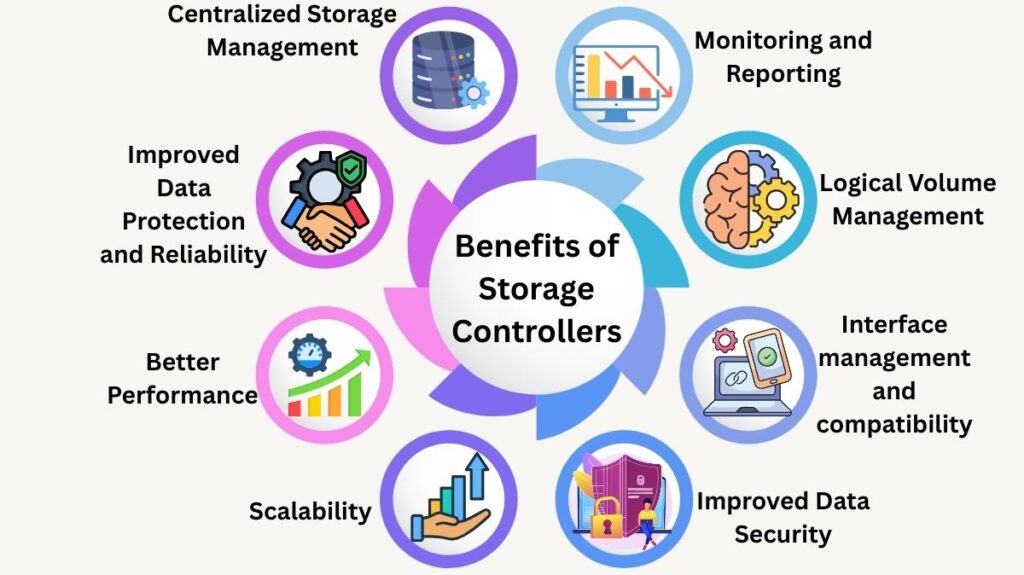
There are various benefits to using storage controllers in networked storage systems:
- Centralized Storage Management: Makes network storage resource management easier.
- Improved Data Protection and Reliability: Made possible by redundancy features like RAID and erasure coding, which offer fault tolerance and prevent data loss.
- Better Performance: Caching, load balancing, and optimisation strategies improve performance by lowering latency and speeding up data access. Additionally, controllers have the ability to optimise command processing for particular kinds of storage devices.
- Scalability: Enables the effective expansion of storage capacity and the installation of additional storage devices to meet the demands of large company data.
- Improved Data Security: By using authentication, access control, and encryption.
- Interface management and compatibility: provide the smooth integration of various storage technologies.
- Logical Volume Management: Provides flexibility in how storage space is used and partitioned.
- Monitoring and Reporting: Offers information for preventative upkeep and problem solving.
A storage controller essentially manages enterprise storage systems, making sure that information is effectively stored, safeguarded, and accessible over a network.
Also Read About Network Controllers: How It Work, Advantages, And Components
