Network Topology
The configuration of computer systems or network devices in relation to one another is referred to as a computer network topology. These topologies have the ability to specify a network’s logical and physical characteristics. They explain the connections and data flow between computers, switches, routers, and other network components. The performance, scalability, and security of a network are directly impacted by the configuration type selected.
Network topology types
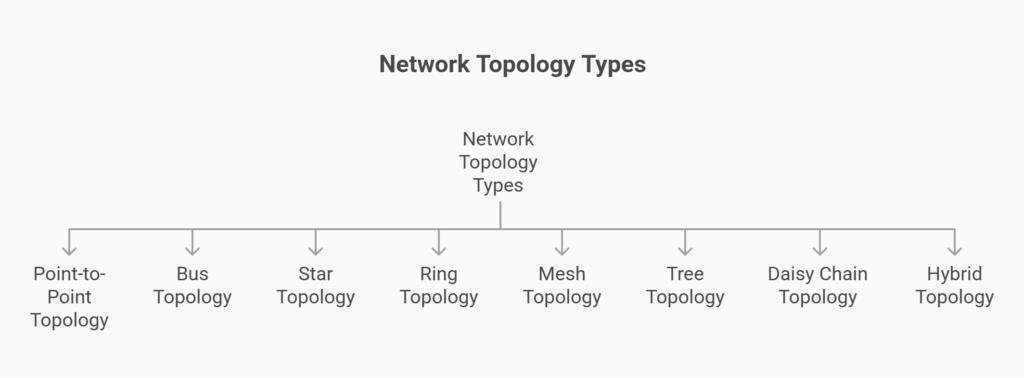
Network topology types
Also Read About CCNA Topics And What Is A CCNA Certification In Networking?
Point to Point network topology
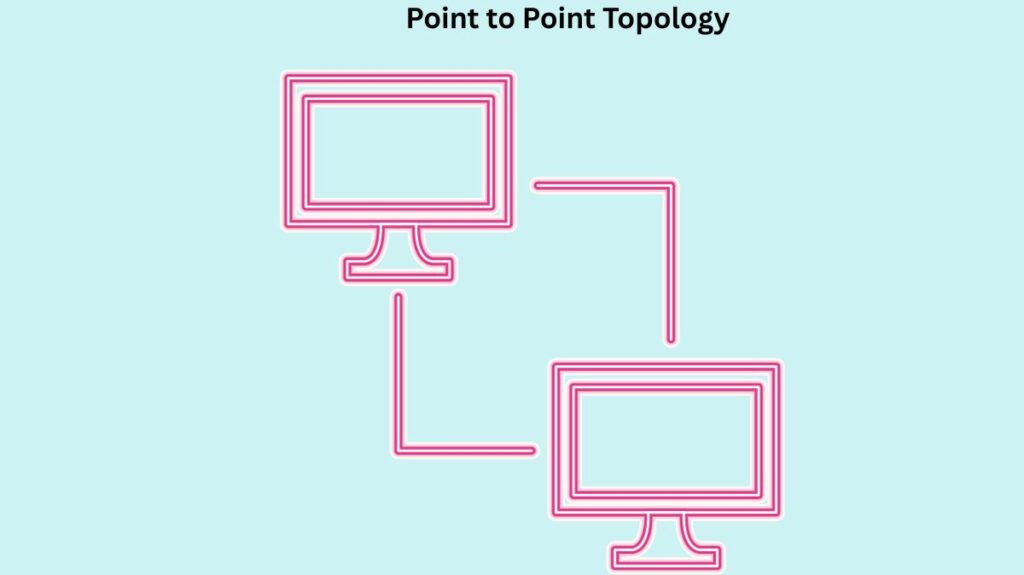
- A single cable is used to connect exactly two hosts (such as PCs, switches, routers, or servers) back-to-back in this configuration. Even with intermediary devices, hosts that are point-to-point logically appear to be directly connected.
- Benefits: Provides high bandwidth, is the simplest method of communication, and improves sender and recipient performance. For dedicated connections, it is frequently utilised.
- Drawbacks: Limited capacity to scale.
- Direct connections between two particular devices are an example of use.
Network bus topology
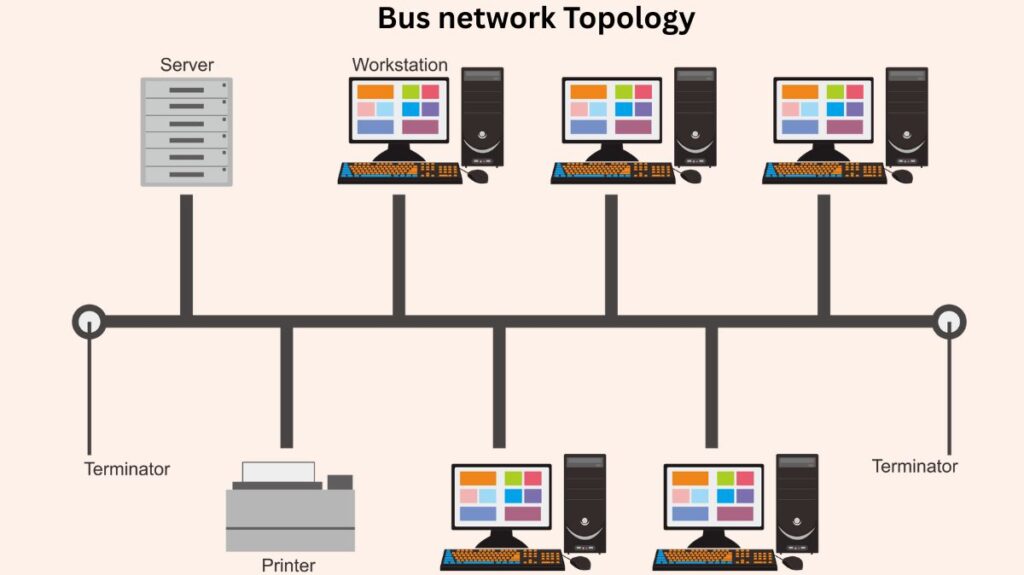
- Structure: The backbone is a single communication line or cable that is shared by all devices. Data is transmitted in a single direction, and when it reaches the far end, it is removed by a line terminator at each end. It is a multi-point, bi-directional connection.
- Benefits: Requires less wiring than other topologies, is economical for small networks, and is simple to deploy. easy to administer and put into practice.
- The network as a whole goes down if the main cable fails, making it a single point of failure. challenging to troubleshoot. Due to data collisions, performance deteriorates with more traffic and devices, frequently necessitating the use of technologies like CSMA/CD or a Bus Master. The network may get slower when more devices are added. There is very little security.
- Examples of applications include cable television networks, Ethernet LANs, and early LANs that used coaxial cable. Perfect for short-term setups or small networks with low data transport requirements.
Also Read About What A Network Is And What Are Benefits Of Networking
Star Topology
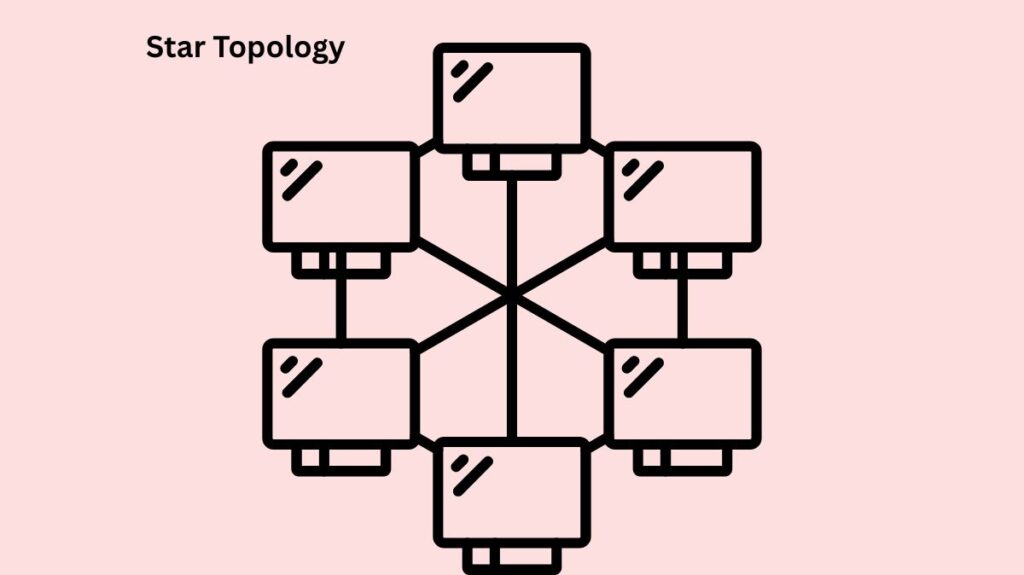
- Structure: Every host has a point-to-point connection to a hub, switch, or router in the middle. This primary hub is where all host-to-host communication takes place.
- Benefits: Simple to add, uninstall, and manage additional devices. The network as a whole is unaffected if one cable or device breaks. Troubleshooting is made simpler by centralised administration. able to transmit data at rapid speeds, particularly when using a switch. sturdy.
- Cons: Single point of failure: the network as a whole stops working if the hub, the central device, malfunctions. costs more since it requires more cabling than bus topology. The cost of installation may be substantial.
- Examples of Use: The majority of contemporary Ethernet networks, home networks, and local area networks (LANs) in workplaces.
Ring network topology
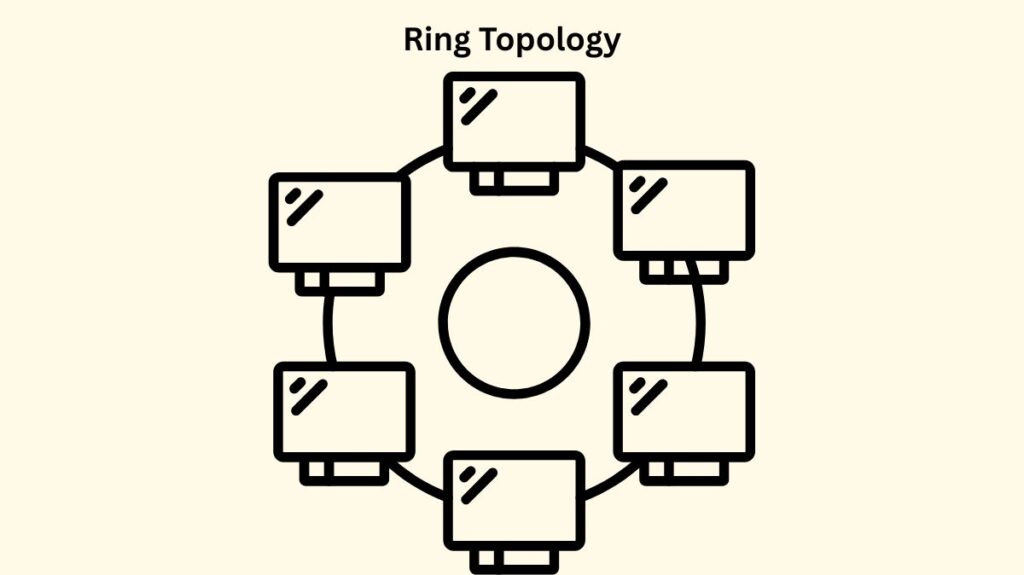
- Structure: A circular network structure is created by each host system connecting to exactly two other machines. Dual-ring topologies provide bidirectional flow with two links between nodes, although data normally flows in one way (unidirectional). In the event that the destination is not nearby, data passes through intermediary hosts. uses repeaters when there are a lot of nodes.
- Benefits include fewer collisions because data only flows in one direction. able to effectively manage large data loads. Information can be transmitted from any hub. There is no need for a central server for administration. inexpensive to extend and install.
- Drawbacks: Single point of failure: if one host, gadget, or cable fails, the entire ring fails. In order to add or remove devices, the network must be shut down. It can be challenging to troubleshoot. less safe.
- Old Token Ring networks are an example of use. Applications like video conferencing, where dependable bandwidth is crucial, and small LANs that need regular network management. metro systems that use SONET technology.
Mesh network topology
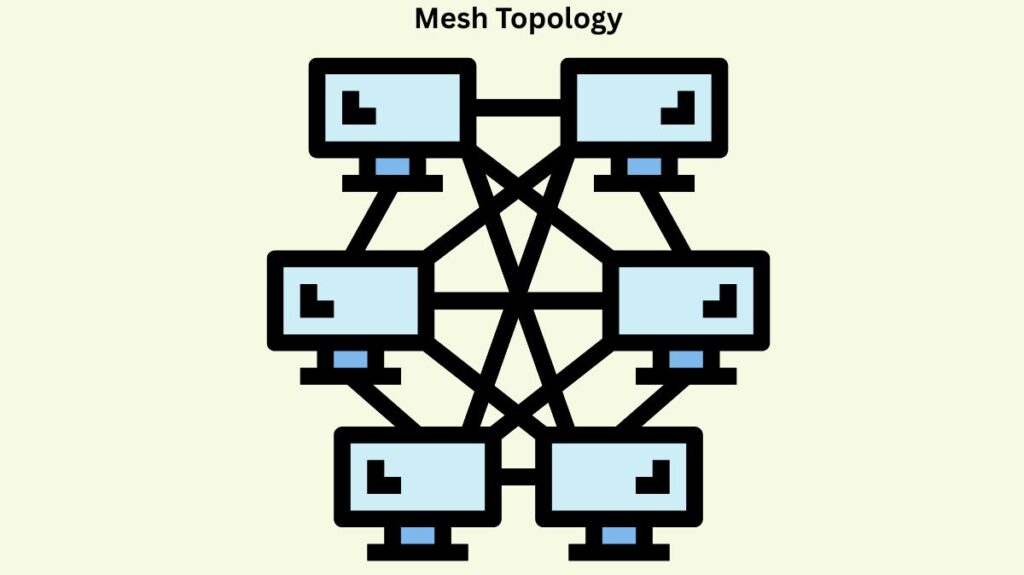
- Structure: One or more hosts are connected to a host. Without direct connections, hosts can also serve as relays for other people.
- Types:
- Full Mesh: All of the devices in the network are directly connected to each other. N(N-1)/2 connections are needed for ‘N’ hosts.
- Partially Mesh: Some hosts connect arbitrarily to other hosts, rather than all of them having point-to-point connections.
- Benefits: Several redundant pathways make it extremely dependable and fault-tolerant. Another route can be taken in case one link fails. Enhanced security and privacy because of point-to-point, direct connections. is able to handle high traffic.
- Drawbacks: costly and difficult to administer and implement. needs a large number of cables. Because additional nodes require dedicated connections, it is rigid and not very extensible in a full mesh.
- Examples of Use: Wireless local area networks (WLANs), the Internet backbone, and critical systems such as financial or military networks.
Also Read About Security Protocols In IoT: Protecting Data And Devices
Network tree topology
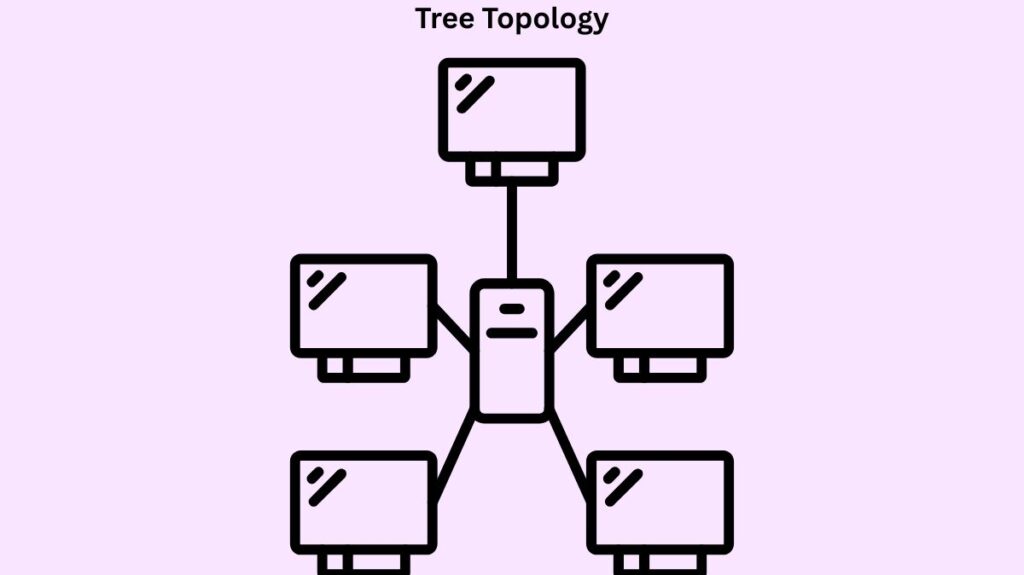
- Another name for structure is hierarchical topology. Combines star and bus topologies. Several star networks are connected to its central backbone, which resembles a bus, creating a hierarchical structure with branches and a root node. separates the network into several layers or tiers (core, distribution, and access). Every nearby host is connected point-to-point.
- Benefits include scalability and ease of layer management. reduces the distance that signals can travel by enabling more devices to be connected to a single hub. Error detection and rectification are simple.
- Cons: Single point of failure: the network as a whole suffers if the root or core backbone fails. difficult to install, modify, and create. Upkeep is costly and challenging.
- Examples of Use: Businesses with hierarchical data structures, university campuses, and large organizational networks.
Daisy Chain Topology
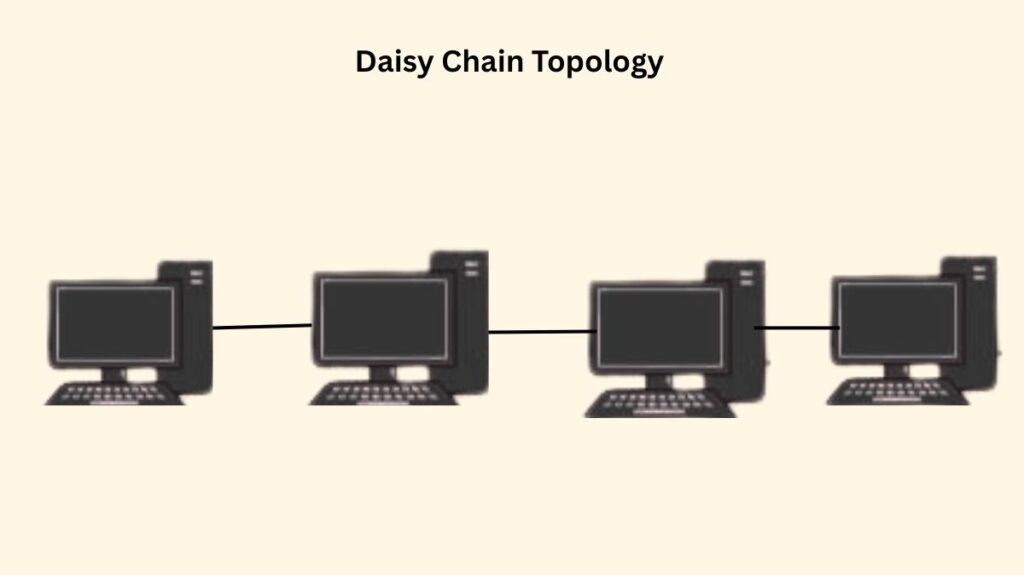
- Structure: Provides a linear connection between all hosts. With the exception of the end hosts, hosts are only connected to two other hosts, much like ring. It turns into a ring topology if end hosts are connected.
- Drawbacks: A link failure divides the network into two parts; each link is a single point of failure. All intermediate hosts function as relays.
Hybrid network topology
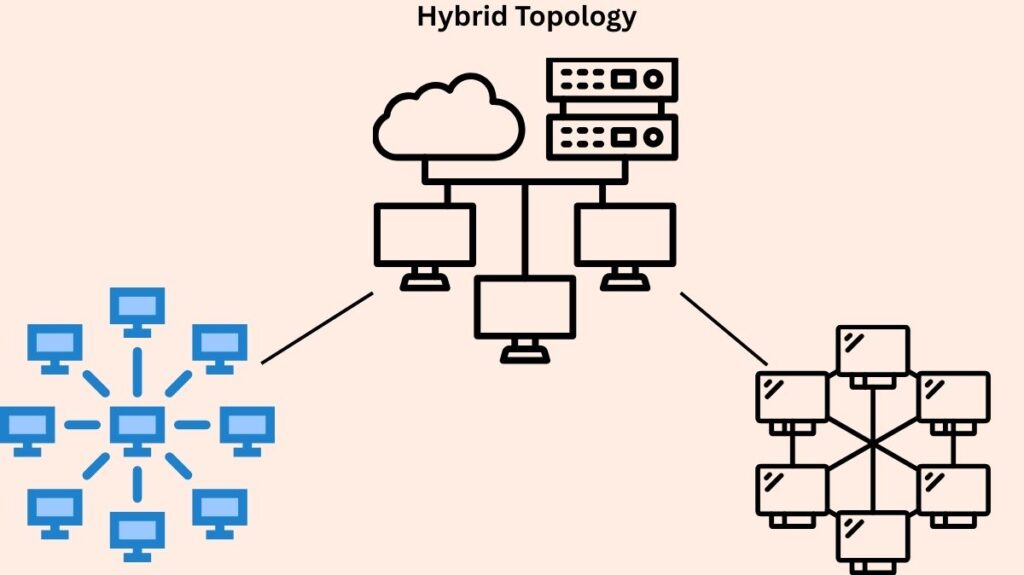
- Structure: A network structure with several topologies in its design.
- Benefits: Extremely scalable and adaptable. brings together the benefits of several integrating topologies. superior than any one topology in terms of dependability and fault tolerance.
- Drawbacks: May be costly and difficult to maintain and design. Because of the intricate architecture, troubleshooting might be challenging. need a large number of network devices and cabling.
- Examples of Use: Internet, most WANs, and corporate networks. frequently observed in big businesses with several departments or locations. networks on university campuses that combine mesh, bus, and star for various regions.
Importance of Network Topology
To ensure top-notch network administration and performance, it is essential to understand network topology. Network administrators benefit from it:
- Recognize Network Structure: Offers understanding of the complex network structure, including the connections and interactions between devices.
- Boost Performance: By optimizing data flow and minimizing bottlenecks, a well-planned topology lowers energy usage and speeds up data transfer, improving overall performance.
- Simplify Management and Troubleshooting: Facilitates the identification of errors and expedites the resolution of problems. For instance, because issues are frequently confined to a single node or central hub, star topologies make troubleshooting easier.
- Improve Flexibility and Scalability: This refers to how quickly a network can grow to accommodate additional devices or reach new locations without requiring significant redesigns.
- Influence Cost Factors: Has a direct effect on deployment and maintenance expenses, ranging from initial setup to ongoing maintenance and enhancements.
- Boost Redundancy and Reliability: Some topologies (such mesh and star) provide backup connections, which boost fault tolerance and network stability and reduce downtime.
- Strengthen Security: Shows how devices are connected to one another, which affects the network’s susceptibility to threats and the ease with which security measures may be put in place.
Also Read About IoT-Cisco Virtualized Packet Core(VPC) And Its Use Cases
Physical vs Logical Network Topology
Physical topology and logical topology are the two primary types of network topology.
Physical Topology: The actual physical configuration of network devices and the wires that connect them is referred to as the physical topology. It displays the hardware locations and obvious physical connections. Bus, star, ring, mesh, tree, and hybrid are a few examples.
Logical Topology: Regardless of the physical connections between network devices, logical topology describes how data moves through a network and how those devices appear to be connected. It illustrates how information moves through a functioning network. This may entail virtual circuits or tunnels or undetectable hops at intermediary sites.
Particularly in intricate networks, there can be significant differences between logical and physical topologies. A logical diagram illustrates the routing of signals and data, whereas a physical diagram shows the connections between wired and wireless devices. Whereas the logical layout influences the speed and transmission of data packets, the physical layout influences cost, scalability, and bandwidth.
Network Topology and Security
Because it defines the links between devices and influences the execution of security measures and vulnerabilities, the network topology has a considerable impact on network security.
Bus Topology
Because of the common communication channel, there is a high danger of data collisions and eavesdropping. The main wire is a single point of failure, which leaves it open to denial-of-service attacks. Traffic can be monitored by any device if encryption is weak.
Star Topolog
An attacker can access all linked devices if the central hub is hacked, making it a crucial security point. requires the hub to have robust security mechanisms (firewalls, IDS).
Ring Topology
If one device fails, the network as a whole may be affected. requires sturdy nodes to withstand attacks and strong encryption for data travelling across each node to prevent eavesdropping. Since traffic passes via several devices, identifying vulnerabilities is difficult.
Mesh Topology
Offers excellent resilience, but makes security management more difficult. Since each link could be an entry point, thorough encryption and authentication are required. Its ability to reroute traffic with flexibility necessitates sophisticated security measures to guard against unwanted access across numerous channels.
Hybrid Topology
By combining several topologies, this creates a complicated security environment. calls for uniform security policies across components and a tailored security approach that tackles the risks of each integrated topology.
Security practices including segmentation, monitoring, and access limitations are essential regardless of the topology.
Scalability and Redundancy
In order to manage redundancy and scalability, network topology is essential:
Scalability
As the needs of the business evolve, a well-designed network can easily accommodate more users, devices, and applications without causing significant disruptions. Adding nodes is easier with star and tree topologies than with bus or ring topologies. Mesh and star topologies are effective at managing high traffic volumes.
Redundancy
The fault tolerance and redundancy offered by various topologies differ. Multiple data channels are provided by mesh topologies, particularly full mesh, which guarantee network stability. The possibility of downtime can be reduced by redirecting data via different paths in the event that one node or connection fails. Strong redundancy is another benefit of partial mesh topologies. Single points of failure may be more likely to occur in bus and star topologies.
IoT and Edge Computing Impact on Network Topology Design
Network topology design is changing as a result of IoT devices and edge computing by:
- Decentralizing Data Processing: By moving data processing away from central cloud data center’s and closer to the source (or “edge”), latency and bandwidth consumption are decreased.
- Growing Network Complexity: Millions of Internet of Things endpoints build complex topologies and frequently communicate with gateways or other peripheral nodes before the main network.
- Facilitating Real-Time Data Processing: In applications such as autonomous vehicles and smart cities, edge computing enables local data processing for real-time analytics and decision-making.
- Raising Security Requirements: Because IoT devices are susceptible, features like network segmentation and Zero Trust Architecture (ZTNA) are being included to separate devices and stop the spread of intrusions.
- Optimizing Bandwidth: Because of the enormous amounts of data generated by IoT, local processing at the edge minimizes data transfer to the cloud.
- Building Dynamic and Scalable Networks: With edge computing nodes offering scalable processing, modern networks are made to be dynamic, enabling the installation of additional IoT devices without requiring significant reconfiguration.
- Including Emerging Technologies: 5G, AI, and machine learning all have an impact on designs; for example, 5G offers crucial high-speed, low-latency connections for edge and Internet of Things devices.
- Improving Fault Tolerance: Peripheral distributed processing increases the fault tolerance of networks by allowing other peripheral nodes to take over in the event of a failure, guaranteeing continuity.
Common Network Design Mistakes to Avoid
When creating network topologies, system administrators should steer clear of these typical errors:
Absence of Redundancy
Network collapse may result from relying on a single point of failure, such as a server, router, switch, or cable. Always use backup sources, pathways, or devices while building.
Inadequate Security
The network is vulnerable to attacks when weak passwords, unsecured ports, unencrypted data, or out-of-date software are used. Make robust security procedures a top priority.
Inadequate Documentation
Administration, debugging, and growth are made more difficult and errors are increased when network diagrams, device labels, and change logs are not created or updated.
Absence of Testing
Failure to simulate scenarios or validate functionality, performance, or security may result in issues that go undetected and affect network efficiency. Thorough testing on a regular basis is crucial.
Lack of Communication
Network alignment may be impacted and misunderstanding may result from a failure to communicate with users, stakeholders, or IT personnel. Effective and proactive communication is essential.
Also Read About What Is A Metropolitan Area Network Architecture & Benefits
Network Topologies in LANs and WANs
- Local Area Networks (LANs): LANs, particularly tiny home networks where devices link to a central device, are where star topologies are most frequently utilized. Although bus topologies save cable costs, they might result in delayed transactions. Ring topologies are also utilized.
- Wide Area Networks (WANs): WANs can employ one or more topologies, contingent on cost-benefit analysis, available space, and business needs. For WANs, ring, star, and mesh topologies are all appropriate. There are two types of WAN topologies: logical (the way data moves) and physical (the actual arrangement of components).
