Rule-Based Access Control RuBAC
An access control system known as Rule-Based Access Control (RuBAC) allows or prohibits a subject (user) from accessing an object (resource) in accordance with a set of predetermined, obligatory rules or criteria.
Usually established by the administrator, these rules are implemented either worldwide or to a particular collection of resources, frequently without taking into account the identity or function of the individual user. This approach is utilized in physical access systems and is most frequently linked to network-level security tools like firewalls.
How Rule-Based Access Control Works
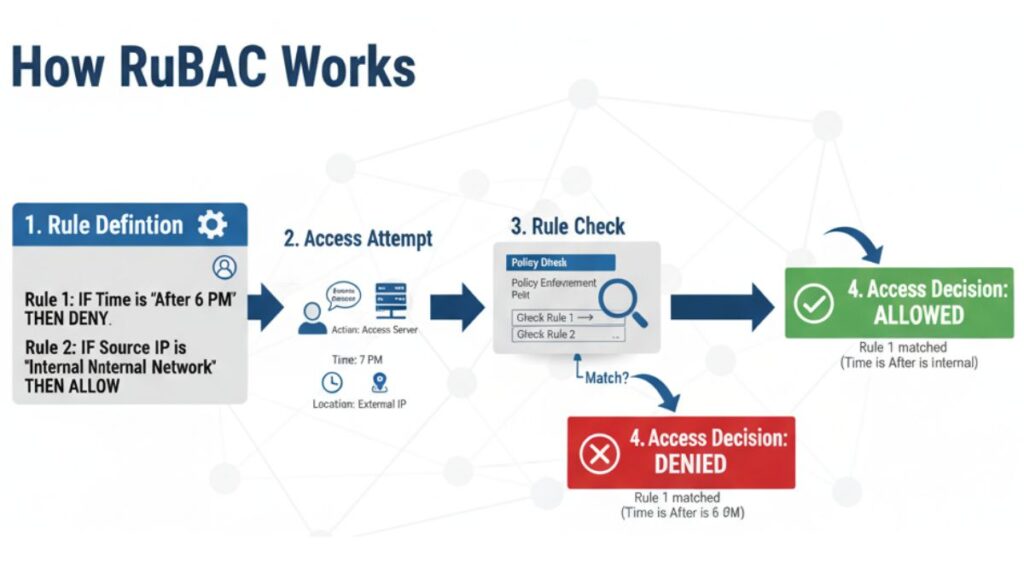
The system checks a set of criteria when someone enters a restricted area, logs in, or opens a door.
- Rule Definition: Administrators create rules like ALLOW or DENY to specify conditions and actions. The user must follow these rules.
- The system automatically checks user credentials or attributes against pre-configured rules when they request access.
- Decision: Access is given if the user’s characteristics match the regulations; otherwise, denied. Administrator authorisation or manual intervention are not needed because the rules are enacted immediately.
Administrators can set and modify access rules globally because they are often managed from a single dashboard.
Also Read About Hierarchical Network Design Benefits For Network Performance
Common Conditions Used in RuBAC
RuBAC gives access decisions more context. The rules may incorporate elements based on user, resource, or environmental attributes rather than just job titles. These conditions may include:
- Time or shift schedules: Unlocking doors only during shifts or limiting admission to 7 a.m.–7 p.m.
- Network context or location: Restricting network traffic to internal corporate IP ranges or requesting additional verification if an individual is in a restricted region after hours.
- Device type: Preventing entry from untrusted networks or granting access only to devices that satisfy certain requirements (such as encryption or latest upgrades).
- User conduct or activity patterns: Monitoring user behaviour and, in the event that a user exhibits abnormal behaviour, removing access.
- Guest or authentication status: For example, requiring simultaneous authentication actions (e.g., badge plus QR scan) or allowing access to a guest only after their host checks them in.
Examples of RAC:
- Preventing any attempts to access a system after 10:00 p.m.
- Permitting only corporate IP addresses to be used for login.
- Limiting access while the system is being maintained.
- All incoming traffic is blocked by firewalls, with the exception of port 443 (HTTPS).
Also Read About DHCP Server Conflict, DHCPv4 Operation & DHCPv6 Operation
Advantages of RuBAC
RuBAC alters the static paradigm of previous systems and lowers risk by enabling organisations to define access based on actual conditions.
- Flexible and Condition-Aware Access: Permissions don’t require human overrides and automatically adapt to the current environment (such as business hours or shift schedules).
- Granular Control: RuBAC offers extremely precise access limitations, applying the least privilege principle with reasoning that extends well beyond straightforward badge access. Access is refused if a user doesn’t fulfil even one requirement.
- Support for Zero Trust: RuBAC is designed to work with contemporary security models that require users to only access the information they require at the precise moment they need it.
- Consistency and Reliability: When administrators properly establish the rules, the system consistently enforces them, reducing the possibility of human mistake.
Disadvantages of RuBAC
RuBAC is strong, yet it has Disadvantages, particularly when used in large quantities.
- Complexity at Scale: If a clear governance model is not employed, the likelihood of overlap or conflict increases with the number of rules, which could result in administrative complexity.
- Performance Requirements: Although contemporary systems are built to execute lightweight rule logic instantaneously, checking numerous rules in real time may cause big deployments to lag.
- Reliant on Clean Data: RuBAC relies on precise information about roles, time zones, and device trust ratings. The rules will be broken if the data is incorrect.
- Setup Complexity: Compared to basic RBAC, implementing RuBAC necessitates a thorough rules database and a well-defined policy framework from the beginning, which can take a lot of time.
Common Use Cases
RuBAC is perfect for locations with lots of visitors and dynamic teams.
- Remote and Hybrid Workforces: RuBAC has the authority to impose additional security measures on remote users or to prevent logins from locations that are not authorised.
- Visitor Management: The system limits visitor time or requires host authorisation depending on type.
- For audit trails and compliance in HIPAA and ISO 27001-regulated industries, RuBAC can use role, device, time, and identity-based control.
- BYOD: RuBAC inhibits unfamiliar or risky devices by restricting access to security-compliant devices.
Also Read About What Is DNAT Destination Network Address Translation? Uses
