This page provides a thorough explanation of smishing, often known as SMS phishing: what it is, how it works, the following factors are contributing to the rise of smishing, common smishing examples (pretexting), SMS phishing detection, SMS phishing defence.
What is SMS Phishing?

Scammers use smishing, also known as SMS phishing, as a hacking technique to deceive victims into divulging personal information such as passwords or bank account information. These messages frequently pose as trustworthy companies, include harmful links to phoney websites or malware, and try to take advantage of people’s faith in text messaging to get them to act quickly. Typical strategies include demands to validate account details, prize frauds, and phoney delivery alerts.
How Smishing Works
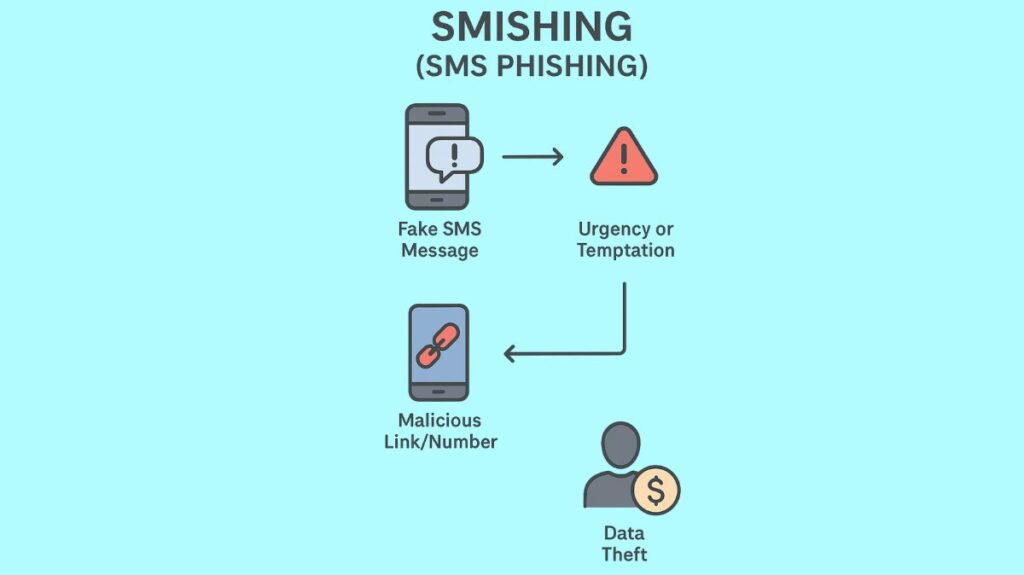
Because individuals tend to trust text messages more than emails, smishing attacks are successful. In a text message, they are more likely to click on a link if it seems to be from a reliable source. Usually, the attacks have a pattern:
Also Read About What Are Spoofing Attack Types? How It Works, And Advantages
Deceptive Message
The con artist sends a text message that looks like it comes from a reputable corporation, bank, package delivery service, government organisation (like the IRS), or well-known retailer.
Sense of Urgency
In order to coerce the victim into behaving hastily and without thinking, the message frequently incites feelings of urgency, fear, or excitement. Typical pretexts consist of:
- An urgent notification that your account has been charged fraudulently.
- A notification that a package delivery was not made or that a new date needs to be set.
- A notification indicating your account has been compromised or locked.
- A guarantee that you are qualified for a special discount or have won a prize.
Malicious Link or Number
The text message contains a phone number to call or a malicious link.
- Links: When a user clicks on a link, they are taken to a phoney website that looks exactly like the real one. The website is made to steal credit card numbers, login credentials, and other personal information that the victim enters.
- Phone Numbers: By dialling the number, the victim is connected to either a human scammer (also known as a vishing attack) or an automated system that will attempt to obtain personal information.
Information Theft
The scammer utilises the victim’s sensitive information for identity theft, financial fraud, or black market sales since the victim thinks they are dealing with a trustworthy organisation.
Factors Contributing to the Rise of Smishing
In 2023, smishing attacks will affect 75% of organisations, making it a growingly common type of cybercrime. Its effectiveness is influenced by multiple factors:
- Increased open-Through Rates: Studies reveal that individuals are more inclined to open links in text messages; the average click-through rate for emails is 2%, while SMS click-through rates range from 8.9% to 14.5%.
- Difficulty Identifying Scams: By using phone number spoofing or email texting, scammers can conceal the source of the communications. Additionally, although the STIR/SHAKEN protocol has made it simpler to identify fraudulent calls, scammers were able to change their focus because this restriction did not have the same impact on text messages.
- Bring Your Own Device (BYOD) and Remote Work: As more workers use mobile devices for work, hackers may find it simpler to get access to company networks via workers’ cell phones.
Also Read About Advanced Phishing Techniques, Prevention And Mitigation
Common Smishing Examples (Pretexting)
The majority of smishing attacks, like other types of social engineering, are based on pretexting, which is the use of false narratives to influence the victim’s feelings.
Typical methods include of:
Banking Scams: Notifications of “suspicious activity” or that an account has been locked are examples of banking scams. At 10% of all smishing messages, bank impersonation is the most prevalent text message scam.
Example: “Your account has been locked. Click here to unlock: [malicious link]”.
Delivery scams: False messages or updates from couriers stating that a package delivery was unsuccessful or that a modest payment or login is needed to reschedule.
Example: “We couldn’t deliver your package. Pay ₹50 here to reschedule: [fake link]”.
Government/tax scams: impersonating law enforcement or the IRS and insisting that the victim take immediate action because they are owed a fine or qualify for a benefit.
Prize/Lottery Scams: Offering prizes or gift cards and telling the victim to click a link to collect the prize are examples of prize/lottery scams.
MFA Fraud: Multi-factor authentication (MFA) fraud is when an attacker, who already knows the victim’s login and password, pretends to be a buddy who has been locked out of the victim’s social media account and deceives the victim into giving up their own MFA code.
Wrong Number Scams: The scammer sends a text that looks like it was meant for someone else, then starts a discussion with the victim over the course of months or years to gain their trust before stealing money through phoney investment proposals or loan requests.
SMS phishing detection
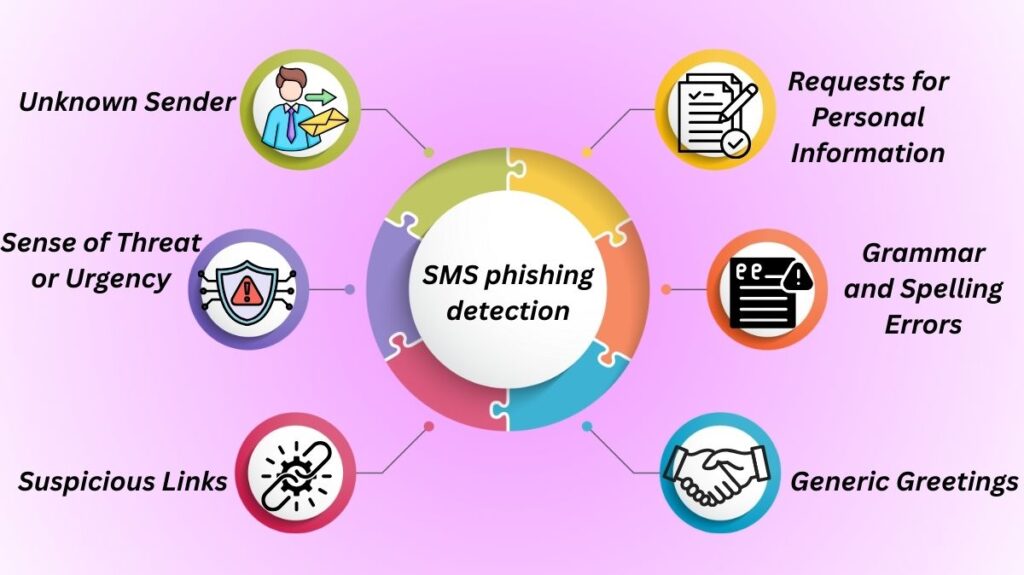
Unknown Sender: An unknown phone number, particularly a 10-digit number that is not typical, is the source of the message. For official texts, businesses frequently use a short code, which is a five- or six-digit number.
Sense of Threat or Urgency: The message urges you to take quick action to prevent a bad outcome (for example, “your account will be closed”) or to take advantage of a brief window of opportunity.
Suspicious Links: The communication includes a link that doesn’t match the name of the firm it purports to be from, particularly if it is abbreviated or generic (bit.ly/1234, for example). Generic link shorteners are rarely used for official business by legitimate companies.
Requests for Personal Information: The text asks for private information such as your Social Security number, account number, or password. Reputable businesses won’t text you for this kind of information.
Grammar and Spelling Errors: Even while AI is reducing the frequency of these mistakes, bad language, misspellings, or strange wording can still be a warning sign.
Generic Greetings: In place of your name, the message utilises a generic welcome such as “Dear Customer”.
SMS phishing defense
Verifying messages and remaining vigilant are crucial smishing defences. Important preventative advice consists of:
- Links in unwanted or dubious SMS messages should never be clicked.
- Independent Verification: If a message purports to be from a business, get in touch with that business directly using their official contact details (not the phone number or URL in the text) to confirm the claim.
- Avoid responding to dubious texts since doing so verifies that the number is live.
- Use only official app stores and refrain from downloading apps from SMS links.
- Turn on multi-factor authentication (MFA), which provides an additional degree of protection.
- Block the sender’s number and notify the mobile carrier of any suspicious texts.
Also Read About Advanced Phishing Techniques, Prevention And Mitigation
