Firewall Logs
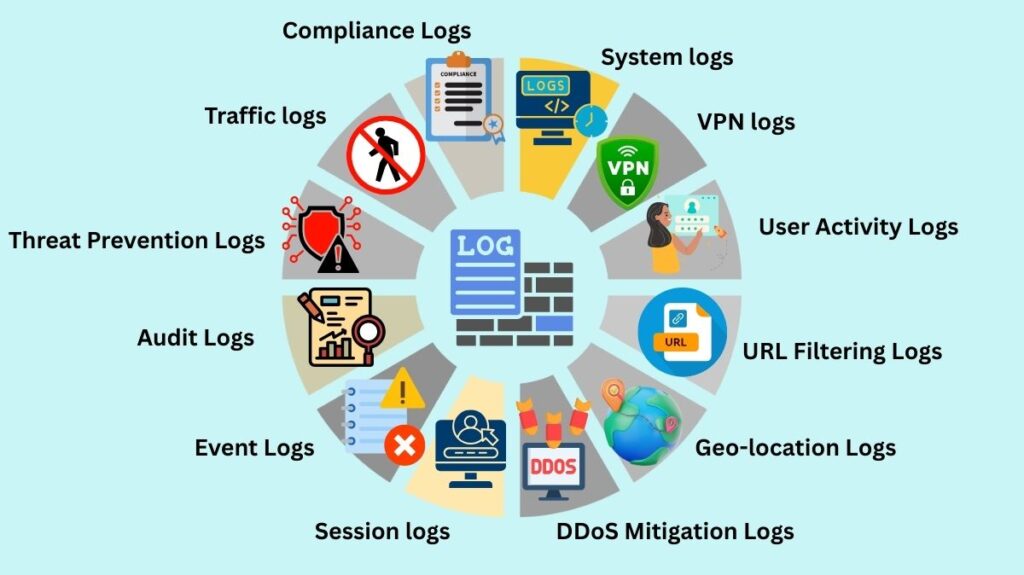
Firewalls log activities and events for auditing, monitoring, and troubleshooting:
Traffic logs
- Description: Network traffic logs detail data flow. Origin and destination This covers IP addresses, port numbers, protocols, and firewall action (accept, drop, refuse).
- Important: To diagnose and enhance network performance, network managers must understand device communication patterns.
Threat Prevention Logs
- Description: Logs created especially to record data on security risks.IPS, antivirus, anti-bot, and other threat data are included.
- Detects and responds to security breaches to help security teams defend the network.
Also Read About Advantages And Disadvantages Of Personal Area Network PAN
Audit Logs
- Description: Logs that document firewall configuration modifications and administration actions. Administrator change monitoring requires these logs for security and regulation.
- Significance: Provides a complete administrative history to aid investigations, security compliance, and audits and compliance.
Event Logs
- General event logs let administrators monitor and fix firewall occurrences by documenting a variety of events.
- Significance: Provides a complete view of firewall operations, making it easier to identify and fix network infrastructure performance issues.
Session logs
- Description: Logs of network sessions, including data transfer rates, user or device information, and start and end times.
- Effective for real-time network session monitoring, anomaly detection, and performance optimization.
DDoS Mitigation Logs
- Logs and firewall mitigation to protect the network from DDoS attacks.
- Importance: DDoS detection, network resource protection, and service availability.
Geo-location Logs
- Description: Records that document the precise locations of network connections. Monitoring and regulating access according to geographic areas may benefit from this.
- Significance: Contributes to a stronger defense against possible threats by identifying and stopping suspicious activity coming from particular geographic places.
URL Filtering Logs
- Description: Stores information about URL filtering and web traffic. This includes user-visited websites and allowed and prohibited URLs.
- Significance: Monitoring and managing online behavior helps organizations regulate internet access, set acceptable use standards, and improve network security.
User Activity Logs
- Description: Logs that record user-specific login/logout, authentication, and traffic trends.
- Significance: Monitors user activity, guarantees responsibility, and alerts users to potential security occurrences.
VPN logs
- Description: VPN connection and disconnection events, tunnel information, and VPN-specific difficulties.
- Importance: Monitors VPN connections’ performance and integrity to ensure safe remote user-company network communication.
System logs
- Description: Firewall system status, configuration, and configuration logs. These could include software update, HA, and other system-level logs.
- Significance: Essential for firewall infrastructure maintenance, trouble detection, and system performance.
Compliance Logs
- Definition: Logs designed to record regulatory compliance events. This could include legal or industry standard compliance.
- Two Significance: Helps organizations subject to particular legislation demonstrate compliance requirements and streamline audit procedures.
Benefits of Firewalls
Firewalls are the first line of cybersecurity defense and essential to network security.
Key benefits include
- Firewalls act as a secured door that only trusted parties can enter, preventing illegal access.
- Blocking Malicious Traffic: Like spam filters, they block viruses, phishing emails, DoS attacks, and backdoors from reaching PCs.
- Private Data Protection: Firewalls protect private and business data from hackers.
- Preventing Cyberattacks: Firewalls examine packets and apply rules to block APTs and hostile actors from entering networks.
- Managing Network Usage: Firewall owners can filter material (parental controls, workplace surfing limits, private intranets).
- Improved Security and Network Integrity: They block harmful traffic.
- Compliance: Firewalls help companies follow industry standards.
- VPNs and firewalls provide secure remote network access.
Drawbacks and Vulnerabilities of Firewalls
Firewalls are essential, however they are not infallible and have various drawbacks:
Incapacity to detect exploits of normal networking processes: Firewalls are unable to detect harmful intent in “legitimate” connections, such as IP spoofing, because they are unable to predict human intent.
Don’t stop connections from going via them: Malicious internal activity cannot be stopped by network-level firewalls alone; host-based internal firewalls are required to divide the network and contain internal threats.
Limited protection against malware: If a connection is deemed acceptable or the firewall is misconfigured or exploited, they may not provide enough protection against malware, even though they can stop connections containing malicious code if they are not permitted. Software for antivirus protection is still required.
Advanced attack susceptibility: Because they lack DPI, less sophisticated firewalls (such as packet-filtering) are susceptible to more sophisticated attacks. NGFWs may encounter difficulties due to changing threats.
Configuration errors: A major security risk is posed by improperly configured firewalls.
Missed Updates: Unpatched software or firmware can expose firewalls to vulnerabilities, as evidenced by events such as the unpatched firewall vulnerability used by the US power grid operator.
Insider Attacks: Internal firewalls are required for segmentation in order to protect against insider threats, whilst perimeter firewalls guard against exterior threats.
Distributed DoS Attacks: DoS attacks that take advantage of existing connections can affect stateful inspection firewalls. It can be difficult to distinguish between attack and regular traffic during a DDoS.
Fileless Malware: Fileless malware that leverages genuine system tools and runs in memory may be difficult for firewalls to identify.
Zero-day Vulnerabilities: Before updates are made available, attackers can take advantage of undiscovered flaws in firewall software.
Supply Chain Attacks: Conventional firewall defenses can be circumvented by compromising reliable third-party vendors and their software distribution channels.
Also Read About Advantages And Disadvantages Of TCP IP Model & Its Functions
What are the best practices for configuring a network firewall?
Several best practices are suggested in order to maximize firewall protection:
Maintain Firewall Operation: Rather than shutting down your firewall, modify its rules or add trustworthy devices to an allow list.
Keep Up to Date: Patch vulnerabilities and protect against emerging attacks by routinely updating operating systems or firewall software.
Combine with Other Security Tools: Since firewalls can’t stop every attack, use reliable antivirus or anti-malware software for complete protection. Another layer of encryption can be added via VPNs.
Deny Unknown Requests by Default: Put in place a “deny all” default policy and specifically allow traffic that is required. Block shady access requests right away.
Limit Accessible Ports and Hosts
Restrict Inbound/Outbound Connections to a Strict Whitelist of Trusted IP Addresses and Limit Accessible Ports and Hosts: Restrict user access privileges to those that are absolutely necessary.
Segment Your Network: To prevent breaches and hinder the lateral movement of malevolent actors, divide the network into discrete security zones (internal, external, and guest).
Conduct Regular Security Audits: To stay abreast of changing threats, conduct regular rule set updates and vulnerability assessments.
Put Change Control in Place: Monitor and manage modifications to firewall rules.
Safeguard the Firewall itself: Limit who can change the settings by using role-based access control, multi-factor authentication, and secure passwords.
Educate Users: Make users aware of security risks such as social engineering and phishing that could attempt to get past the firewall.
Maintain Network Redundancies: During an incident, data backups help keep productivity high and prevent loss.
Also Read About Network Topology Types: Bus, Star, Mesh And More Topologies
Uses of Firewalls
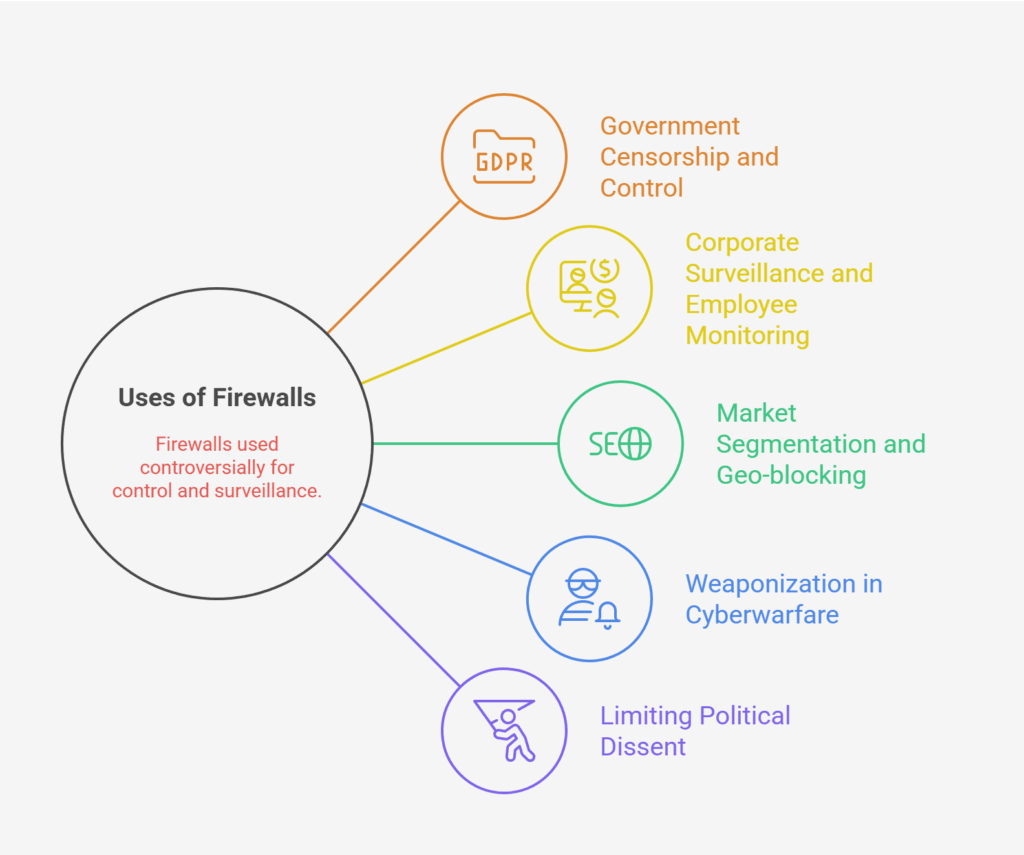
Even though firewalls are essentially security technologies, there are several uses for them that create moral, political, or societal issues:
- Government Censorship and Control: The Great Firewall of China, which censors access to sensitive content, tracks online activity, and restricts Internet services to local businesses, is an example of how firewalls might limit access to particular websites or content based on political or ideological purposes.
- Corporate Surveillance and Employee Monitoring: Businesses may utilize firewalls, especially those with DPI functions, to monitor employee online activity or limit access to legitimate websites, which raises privacy concerns.
- Market segmentation and geo-blocking: Firewalls regulate geographic access; they are employed to manage digital rights, but they also raise issues with digital equality and access.
- Weaponization in Cyberwarfare: Malevolent actors or nation-states may alter firewall configurations to open backdoors, obstruct traffic, or utilize them as command centers in a network that has been compromised.
- Limiting Political Dissent: To stifle dissent, authoritarian governments employ firewalls to ban protest sites and activist websites.
Network Security’s Future
The field of cybersecurity is always changing as new trends are developed to handle dynamic threats and increasingly sophisticated networks. Among the new trends are:
- Software-Defined Perimeter (SDP): Usually built on a zero-trust framework, SDP focuses on protecting user access as opposed to IP-based access.
- Secure Access Service Edge (SASE): Integrating networking and security features into a single cloud-delivered service, SASE is becoming more and more crucial for defending networks against emerging threats.
- Firewall as a Service (FWaaS): Cloud-based firewall solutions that provide servers and remote workers with flexibility and scalability.
- Zero-Trust Policy: Provides access only when necessary, assuming that all requests are potentially malevolent.
- AI and automation are anticipated to become more important in identifying and responding to threats.
- Creating encryption methods that are impervious to quantum attacks is known as post-quantum cryptography.
- Fifth-Generation Network Security: Powered by 5G networks, this approach emphasizes faster and lower latency for critical infrastructure and Internet of Things devices.
- Extended Detection and Response (XDR): Platforms that combine information from many security levels to centralize threat detection and response.
