What is HIDS?
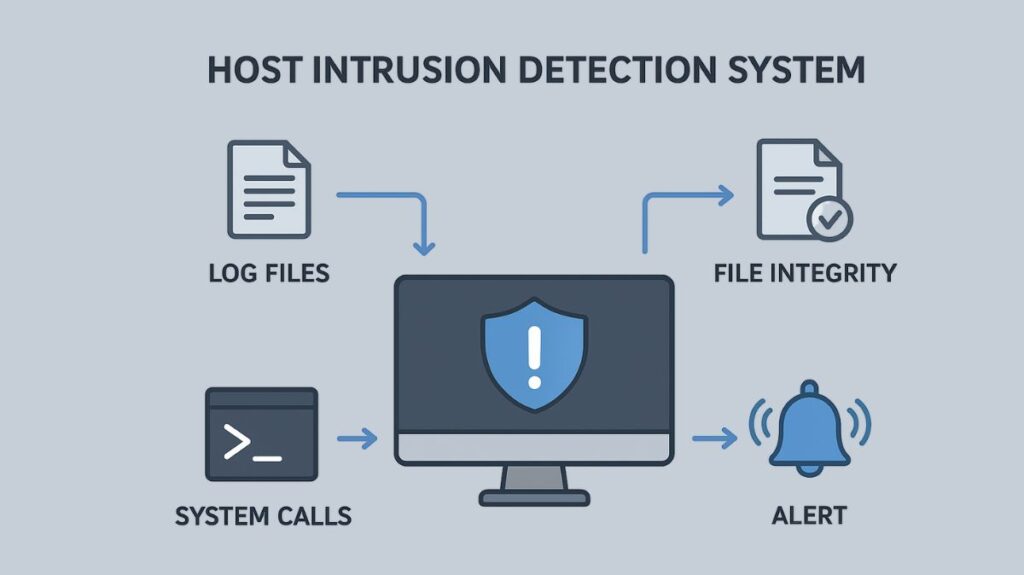
Installed on individual devices, such as servers and PCs, a host intrusion detection system (HIDS) is a security tool that keeps an eye on and examines activities on that particular host for questionable activity. It finds dangers that network-level monitoring could overlook by examining system logs, file integrity, and other host-based data. By comparing current states to a baseline or a database of known assaults, HIDS can notify administrators of anomalies, illegal access attempts, or modifications to important files.
By keeping an eye on host activity rather than network traffic as a whole, HIDS concentrates on more specific and internal attacks. The first kind of intrusion detection software to be created was called HIDS.
You can also read What is RADIUS Components, Architecture and Applications
Key Functions and Monitoring Capabilities
A HIDS offers fine-grained, in-depth insight into a particular host’s internal activities. A HIDS keeps an eye on the following important activities:
- File Integrity Monitoring (FIM): This feature keeps track of important registry settings, operating system, application, and configuration files. It compares the present state of files to a known, secure baseline in order to identify any illegal changes, deletions, or revisions.
- Log File Analysis: HIDS keeps an eye out for questionable trends, irregularities, policy infractions, unsuccessful login attempts, or privilege escalation in system, application, and security logs (including authentication logs).
- System Call Monitoring: It keeps an eye on system-level operations like file access and process execution. It keeps track of the running programs, the resources they use, and their actions. For example, it could identify if a typical application tries to access a system file that is protected or sends out strange network data.
- User Activity Tracking: In order to identify unauthorized activity or compromised accounts, HIDS monitors user logins, privilege usage, and other user-specific actions. It frequently helps identify insider threats.
- Rootkit Detection: Detecting malicious or hidden processes that try to obtain privileged access is known as rootkit detection.
- Host Network Activity: Although its primary focus is internal, HIDS can also keep an eye on network packets on its own network interfaces. By tracking the particular network traffic linked to that host, it can identify any efforts at data exfiltration or unauthorized connections.
How HIDS Works
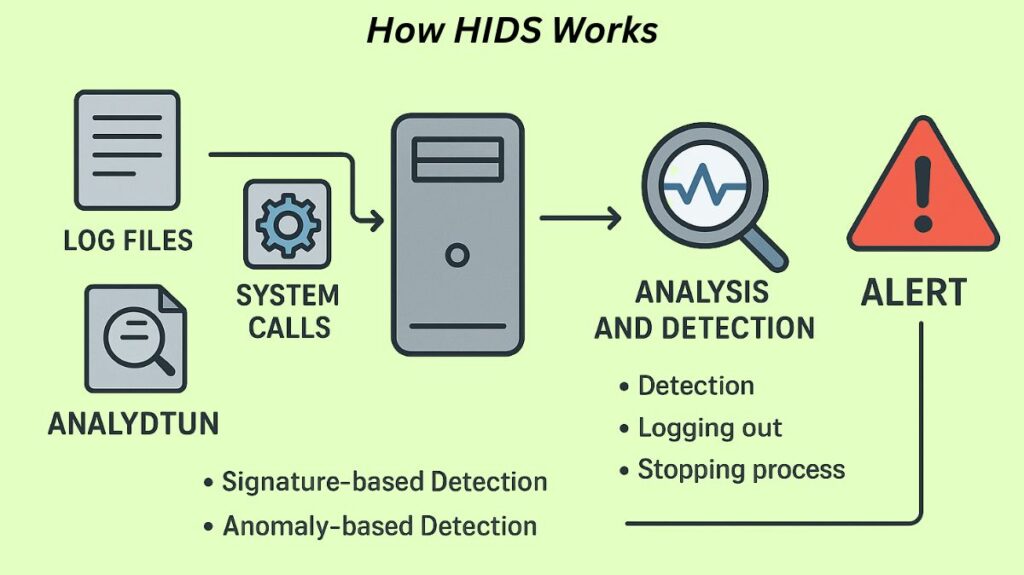
Data gathering, analysis, and reaction are all part of a HIDS’s operation:
- Data Collection: Log files, system calls, and file integrity checks are some of the sources from which the HIDS software, which is frequently deployed as an agent installed on each host, gathers data. An agentless HIDS, on the other hand, gathers data by streaming data across the network; this method uses fewer host resources, but it could be more difficult to set up.
- Analysis and Detection: After processing the collected data, the analytics engine searches for trends or anomalies. HIDS usually uses two primary detection techniques:
- Signature-based Detection: This technique works well against known threats by comparing tracked activity to a database of harmful signatures or known attack patterns.
- Anomaly-based Detection: Establishing a baseline of the host’s “normal” behavior is the goal of anomaly-based detection. Any notable departure from this baseline is noted as unusual and looked into as a possible danger. This technique works well against novel or “zero-day” attacks.
- Alerting and Response: The HIDS notifies an administrator if it notices questionable activity.
- The primary function of a HIDS is passive; it is intended to identify the existence of an attack and alert the administrator; it usually does not stop the attack from occurring.
- However, a HIDS can start reaction activities, such logging a user out, halting a process, alerting administrators, or, in some situations, creating firewall rules automatically to stop probes.
- Additionally, HIDS platforms have the ability to produce reports regarding the environment’s security status.
You can also read Types And Advantages Of Intrusion Prevention System IPS
HIDS vs. NIDS Comparison
A Network Intrusion Detection System (NIDS), which keeps an eye on network activity throughout a whole segment, is frequently contrasted with HIDS. The two systems work well together as part of a strong security plan:
| Feature | HIDS (Host Intrusion Detection System) | NIDS (Network Intrusion Detection System) |
|---|---|---|
| Monitoring Scope | Individual host (endpoint). | Entire network or network segment. |
| Data Source | System logs, files, processes, system calls. | Network packets and traffic. |
| Detection Focus | Local attacks, file tampering, internal misuse, privilege escalation. | Network-based attacks (e.g., port scanning, DoS attacks). |
| Visibility | Deep, internal visibility; can inspect encrypted data on the host. | Broad visibility of network traffic; struggles with encrypted traffic. |
| Deployment Location | On each host that requires monitoring. | At strategic points in the network (e.g., switches, gateways). |
| Examples | OSSEC, Tripwire. | Snort, Suricata. |
Advantages and Limitations
Advantages of HIDS:
- Deeper Visibility: Offers extensive inside insight into host operations, including access to the host’s encrypted data.
- Insider and Local Threat Detection: Attacks that come from within the network or that get past the network layer are detected by insider and local threat detection.
- Integrity Monitoring: Keeps an eye on the safety of important documents.
- Detailed Information: Offers comprehensive details regarding attacks on particular hosts.
Limitations and Challenges of HIDS:
- Limited Scope: It can only monitor the host on which it is installed.
- Performance Impact: Installing the HIDS agent on each host may use up system resources (CPU, RAM), which could cause performance to lag.
- Scalability Issues: Needs deployment on every host, which may be problematic for big infrastructures.
- False Positives: Alert fatigue may result from false positives caused by configuration errors.
Examples of HIDS solutions include OSSEC, Tripwire, AIDE (Advanced Intrusion Detection Environment), and Samhain.
You can also read TACACS+ Protocol Configuration And TACACS+ Vs RADIUS
