AAA framework
A fundamental security framework for computer networks and systems, the Authentication, Authorization, and Accounting (AAA) framework often called “triple-A” is used to manage user access, enforce rules, and audit usage.
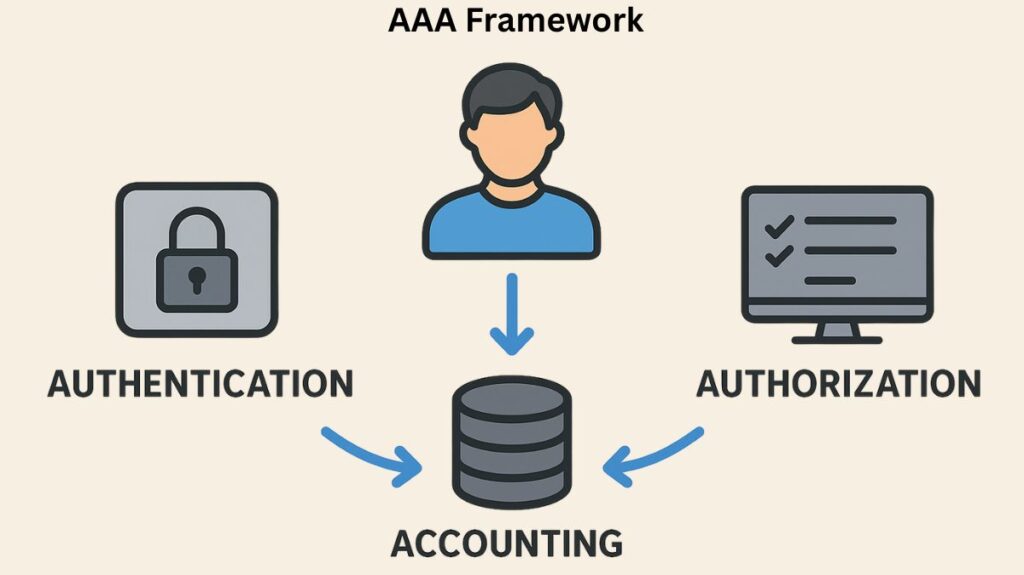
A collection of services known as the AAA framework is seen to be essential for efficient network administration and security since it intelligently regulates access to computer resources. Three separate, sequential concerns concerning any entity trying to access network resources are addressed as it moves forward chronologically:
- Who are you? (Verification)
- What are your permitted actions? (Credit)
- What did you do? In accounting
Also Read About MFA Vs 2FA Authentication, Methods, Benefits And Importance
Authentication (AuthN)
The first step in the AAA procedure is authentication.
Definition and Goals: The security procedure of confirming the identification of an individual or a process is known as authentication. It guarantees that only verified users are granted access and validates the legitimacy of the organization making the request. It provides an answer to the query, “Who are you?”
Procedure: The user must supply credentials, including a username and password, and divulge personal information. By comparing these credentials to a database of stored credentials, a specialized AAA server validates them.
Techniques: The user may be authenticated by something they own (such as a smart card or USB key), something they know (such as a password), or something they are (such as a fingerprint or other biometrics).
Result: The user is authenticated and granted network access if the credentials match; if not, access is refused.
Authorization (AuthZ)
Successful authentication is followed by authorization.
Definition and Goals: Authorization is the security procedure that establishes the rights and particular permissions that a verified user or device is permitted to have. It is the procedure for implementing regulations. It provides a response to the query, “What can you do?”
Function: Following authentication, the user could be granted permission for various kinds of activities or access. The system compares an access control policy with the user’s specified responsibilities, privileges, or group memberships. This procedure complies with the Principle of Least Privilege by giving users just the minimal amount of access required to carry out essential tasks.
Control: Authorization gives certain areas of a system or network access rights. For example, an IT worker can change VPN passwords for specific users even if they were previously prohibited access since a network administrator can change user privileges.
Also Read About Identity Based Access Control(IBAC) Features And Advantages
Accounting (Audit)
Accounting is the framework’s monitoring and logging feature.
Definition and Goals: Accounting is the security function that keeps track of user activity and logs access attempts. The user’s session is continuously recorded. It provides an answer to the query, “What did you do?”
Data Tracked: Accounting logs usage data and session statistics to maintain tabs on activities occurring within the network. An “audit trail” is created by this logged data, which contains information like:
- The entire time spent, including both login and logout periods.
- How much data is delivered or received.
- The resources or services used.
- Certain directives were carried out.
Usage: Accounting data is utilized for capacity planning, forensic analysis, auditing user behavior, detecting user trends, and generating more accurate invoicing (if the system bills by time).
AAA Architecture and Implementation
Usually, a client/server architecture is used to distribute AAA.
| Component | Role | Examples |
|---|---|---|
| AAA Client (Authenticator/NAS) | The device users connect to (e.g., a router or switch) that forwards user credentials for checking. | Routers, Switches, WLAN Controllers (WLCs), and Access Points (APs). |
| AAA Server (Authentication Server) | The central system that verifies user details, manages access rules, and stores the security database and policies. | Cisco Identity Services Engine (ISE), Access Control Server (ACS), or third-party identity platforms like Auth0. |
Compared to setting up simple security settings on each device separately, this architecture’s centralized access control and scalability make managing big setups simpler.
This communication is made possible by common protocols such as:
- An Open Standard protocol called RADIUS (Remote Authentication Dial-In User Service) is frequently used for centralized network access, including VPNs and Wi-Fi. Typically, RADIUS integrates permission and authentication into a single resource. UDP ports 1812 and 1813 are used for authentication and accounting, respectively.
- The protocol known as TACACS+ (Terminal Access Controller Access-Control System Plus) was initially exclusive to Cisco. Because it allows granular command-by-command permission and separates authentication, authorization, and accounting, it is typically more appropriate for network device administration. TACACS+ performs all of its activities on TCP port 49.
- Diameter: A development of RADIUS intended to maximize multimedia and LTE networks.
Also Read About Cisco Switch BPDU Guard Configuration In Networking
