What is CWPP?
A security solution that finds and eliminates risks within cloud software is called a cloud workload protection platform (CWPP). Similar to an auto technician who finds defects and malfunctions in an automobile’s engine before they cause more harm, a CWPP examines the interior of cloud services rather than automobiles. Virtual machines, server less operations, and actual on-premise servers are just a few of the workloads that CWPPs automatically monitor.
How Do CWPP work?
In order to ensure protection across various environments, including virtual machines, containers, and serverless architectures, cloud workload protection platforms (CWPPs) offer security policies specifically designed for cloud-based workloads. In order to monitor, protect, and manage the lifetime of cloud workloads, they usually interact with internal systems and cloud providers.
Workloads are regularly inspected for vulnerabilities, configuration problems, and runtime risks by CWPPs. They frequently collect comprehensive data on every task using both agent-based and agentless techniques. Agent-oriented CWPPs provide rich, real-time information and control by installing lightweight agents on particular workloads. Agentless CWPPs provide security without the overhead of agents by collecting metadata via cloud provider APIs.
Vulnerability management, network segmentation, and runtime protection are essential elements of CWPPs. Vulnerability management include checking workloads for unpatched vulnerabilities, obsolete software, and configuration errors. By separating critical resources, network segmentation helps reduce the amount of time that workloads are exposed to unwanted access. Runtime protection automatically blocks harmful behaviours and applies security controls while continually scanning workloads for unusual activity.
CWPPs guarantee uniform security in hybrid and multi-cloud settings by integrating with both cloud-native and conventional infrastructure. They help businesses have a solid security posture even when workloads grow or move across cloud providers by automating a large portion of the security management process.
Why Importance of a CWPP?
Modern businesses cannot be protected by traditional security measures. As cloud services were adopted, the cloud workload protection platform appeared. As single-cloud deployments gave way to multicloud and hybrid cloud models, it soon became indispensable.
While these models provide businesses several advantages, they also introduce complications and particular dangers. The dynamism and heterogeneity of cloud systems are increased by virtual machines (VMs), containers, serverless computing, and other varied workload types in addition to the many public, private, and hybrid cloud setups.
The CWPP simplifies the cloud environment, which is badly required. It offers thorough visibility in a single platform that can protect a variety of workloads. Organisations may confidently exploit the advantages of the cloud by putting in place a CWPP that meets their needs.
Key Features of CWPP
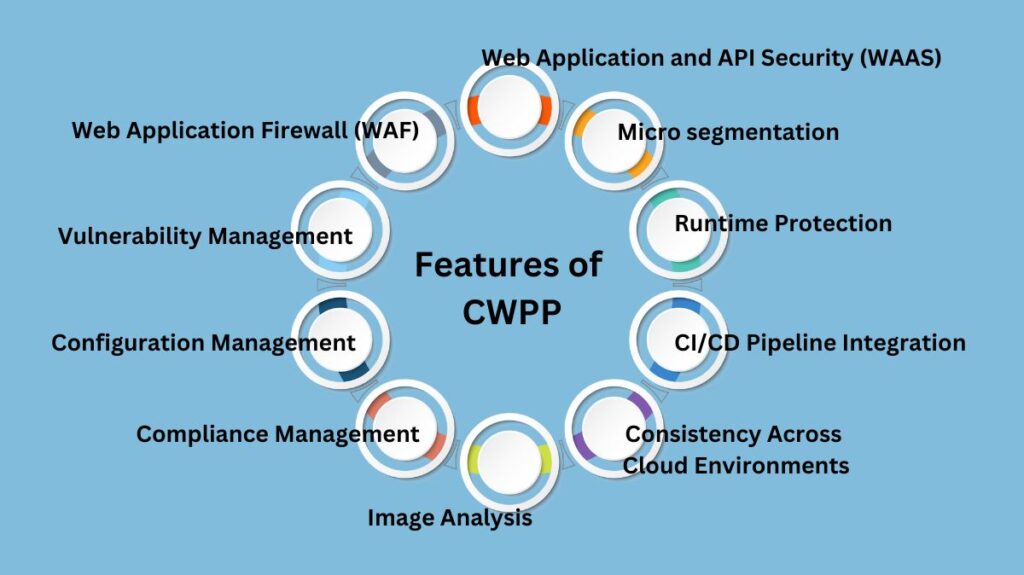
An omnibus set of integrated capabilities to safeguard cloud workloads is provided by a well-rounded CWPP, which unifies several security components under one roof.
Vulnerability Management
To find and rank vulnerabilities in cloud workloads, the CWPP facilitates ongoing vulnerability evaluation. The CWPP uses threat intelligence to evaluate the risk presented by vulnerabilities by including vulnerability databases such as CVE (Common Vulnerabilities and Exposures). By offering patching tools or interacting with pre-existing patch management systems, the platform also facilitates vulnerability repair. The CWPP assists in setting mitigation priorities according to the sensitivity of the impacted data and services, contextual risk factors with the workload, and the degree of vulnerabilities.
Configuration Management
Configuration management, security best practice monitoring, and enforcement are made possible by the CWPP. It offers automatic compliance tests against industry standards, such as CIS Benchmarks, and is in line with them. Additionally, the platform automates the enforcement of secure setups or provides repair guidance.
Compliance Management
Cloud workloads are guaranteed to comply with legal requirements like PCI DSS, HIPAA, and GDPR to compliance management. CWPPs offer compliance-oriented security setups and automated monitoring to assist organizations in maintaining compliance. Along with dashboards to show security posture and compliance status, the platform also produces compliance reports that describe the compliance status of cloud workloads. CWPPs assist minimise possible regulatory fines by ensuring a prompt and compliance response in the case of a security issue.
Image Analysis
Before container images enter the runtime environment, image analysis entails examining them for any security flaws and removing those that could include embedded malware or out-of-date, insecure packages. Implementing policies that specify which registries, repositories, and images you may trust is another capability of the CWPP. Organisations may make sure that application components only come from approved sources by employing trustworthy images.
Consistency Across Cloud Environments
CWPPs guarantee uniform application of security rules and controls across all cloud environments. This includes on-premises infrastructure, private clouds, and public clouds like Microsoft Azure, Google Cloud Platform, and Amazon Web Services.
CI/CD Pipeline Integration
SIEMs, SOAR platforms, and DevOps technologies are just a few of the security tools and procedures that the CWPP connects with. The CWPP can assist support shift-left security techniques to identify and address security vulnerabilities before they reach production by interacting with CI/CD pipelines and provide security feedback early in the software development lifecycle. By doing this, it assists teams in conforming to DevSecOps standards.
Runtime Protection
In order to fight against assaults and unauthorised activity in real time, runtime protection entails keeping an eye on and safeguarding workloads while they operate in the cloud computing environment. Using methods including behavioural analysis, machine learning, and signature-based detection, the CWPP provides strong threat detection capabilities together with runtime protection. For the most recent threat detection, it connects with threat intelligence streams. The CWPP offers comprehensive forensics to look into occurrences and facilitates incident response automation, such as automated quarantine or workload termination.
Micro segmentation
Developers and security teams may segregate workloads and restrict lateral movement inside the environment with the help of the microsegmentation features that many CWPPs offer. When it is available, this functionality easily combines with both native cloud networking and container networking solutions.
Web Application and API Security (WAAS)
Web application and API security (WaaS) is incorporated into several CWPPs, particularly when it comes to cloud-native and containerised apps. In terms of API security, for example, a CWPP could have features to guarantee safe communication between microservices in a microservices architecture, which is frequently used in cloud-native apps.
As part of this, the CWPP may monitor API activity to identify and address abnormalities and possible risks, offer identity and access management to guarantee that only authorised organisations can use the APIs, and enforce encryption for data in transit.
Web Application Firewall (WAF)
Certain sophisticated CWPPs include security capabilities that are commonly seen in web application firewalls (WAFs). WAFs guard against the OWASP Top 10 security threats, which include cross-site scripting (XSS) vulnerabilities, injection, and failed authentication.
It’s crucial to remember that although CWPPs and WAFs and API security solutions may share some features, they should be used in addition to rather than in instead of these solutions.
