This guide explains the step-by-step process of how Data Flows Through The OSI Model, including encapsulation and decapsulation. Discover why this universal networking standard is crucial for modern network design and analysis.
Open Systems Interconnection
One conceptual framework that standardizes the way various computer systems communicate via a network is the Open Systems Interconnection (OSI) model. The International Organization for Standardization (ISO) created it, and it offers a common language for computer networking.
The intricate process of data transmission is separated into seven separate levels by the OSI model, each of which has a particular set of duties. By adopting common protocols, this layered approach helps guarantee that various systems can communicate with one another.
Importance of the OSI Model
- It explains the process by which data moves from one computer’s software application to another computer’s application across a network medium. Together, the specialized functions of each layer guarantee accurate and effective data transmission.
- The model facilitates networking protocol standardization and simplifies troubleshooting. By segmenting communication into discrete layers, network experts may efficiently isolate and fix difficulties, identifying problems to a particular layer.
- It gives computer networking a universal language that makes communication between various network hardware and software possible.
- It promotes quicker research and development because developers may concentrate on enhancing particular layers without influencing others, which results in quicker breakthroughs.
- Even though the more straightforward TCP/IP model is more closely aligned with the present Internet, the OSI model is still frequently utilized as a useful theoretical framework for comprehending and debugging network communication.
Seven Layers of OSI Model
Application Layer (Layer 7)
Function: User applications receive network services directly from this layer, which is the one nearest to the end user. It makes it easier for applications to deliver and receive data by facilitating communication between lower layers and API endpoints.
Key functionalities: Shared resources, file transfers, network administration, communication and authentication, remote access (e.g., email clients, web browsers), and directory services.
Examples: DNS (converting domain names to IP addresses), SMTP (mailing), FTP (file transfer), and HTTP (web browsing). This layer supplies the protocols that client software programs depend on, but the apps themselves are not a part of it.
Presentation Layer (Layer 6)
Function: In order to prepare data for the application layer, this layer also referred to as the syntax layer or translation layer makes sure the data is in a format that the receiving application can comprehend.
Key functionalities: ENcrypt/decrypt, compress, and translate (ASCII to EBCDIC). It guarantees compatibility across systems that use various techniques for representing data.
Examples: Secure transmission via SSL/TLS, image compression using JPEG, video compression with MPEG, and GIF.
Session Layer (Layer 5)
Function: The communication sessions between two hosts or apps are started, maintained, and ended via this layer. In order to save resources, it makes sure that sessions stay open long enough for data transfer and then ends them.
Key functionalities: formation, upkeep, and termination of sessions (including authentication), synchronisation (including recovery checkpoints), and dialogue control (full-duplex or half-duplex communication).
Examples: PPTP, RPC (Remote Procedure Call), and NetBIOS.
Transport Layer (Layer 4)
Function: Data delivery between hosts is handled by this layer from beginning to end. At the receiving end, it reassembles the data after it has been broken up into smaller parts known as segments for transmission from the session layer.
Key functionalities: Error control (ensuring full data delivery and asking retransmission if necessary), flow control (regulating data transmission rate to prevent overflow), data segmentation and reassembly, and service point addressing (using port addresses to deliver messages to the appropriate process).
Services: Provides connectionless service (faster, less dependable, like UDP) as well as connection-oriented service (reliable, with acknowledgements, like TCP).
Examples: The UDP and TCP protocols.
Network Layer (Layer 3)
Function: The data routing over many networks (an internetwork) is the responsibility of this layer. It specifies the route that packets will take to get to their final location. It uses logical addresses to uniquely identify hosts outside of subnets as well.
Key functionalities: logical addressing (such as IP addresses) to identify devices in a unique way across networks, packet fragmentation/reassembly, and routing (figuring out the optimum path for data). At this layer, routers function.
Examples: Open Shortest Path First (OSPF), Internet Control Message Protocol (ICMP), IP (Internet Protocol), including IPv4 and IPv6, and IGMP. This layer does not require error reporting or reliability.
Data Link Layer (Layer 2)
Function: The dependable conveyance of data between two network nodes that are directly connected on the same network segment is the responsibility of this layer. It creates data frames from the raw transmission data from the physical layer.
Sublayers: Media Access Control (MAC) regulates device access to network media and physical addressing, whereas Logical Link Control (LLC) manages flow control, synchronisation, and multiplexing.
Key functionalities: Physical addressing (using MAC addresses), flow management, error control (identifying and retransmitting lost or damaged frames), and framing (arranging bits into frames).
Examples: Wi-Fi (MAC layer), Ethernet, and PPP (Point-to-Point Protocol). At this layer, switches and bridges frequently function.
Physical Layer (Layer 1)
Function: This layer, which is the lowest one, handles the actual connections between devices. In order to transfer raw bits (1s and 0s) over a communication media, it specifies the electrical, optical, and mechanical requirements.
Key functionalities: Bit rate management (establishing transmission rates), physical topologies (device configuration), bit synchronization (providing a clock for sender and receiver), and transmission mode (simplex, half-duplex, full-duplex).
Examples: Network interface cards (NICs), hubs, repeaters, modems, radio waves, USB, Bluetooth, and cables (such as Ethernet and fiber optic cables). It also describes the process of encoding over a physical signal, such as light pulses or electrical voltage.
How Data Flows through the OSI Model
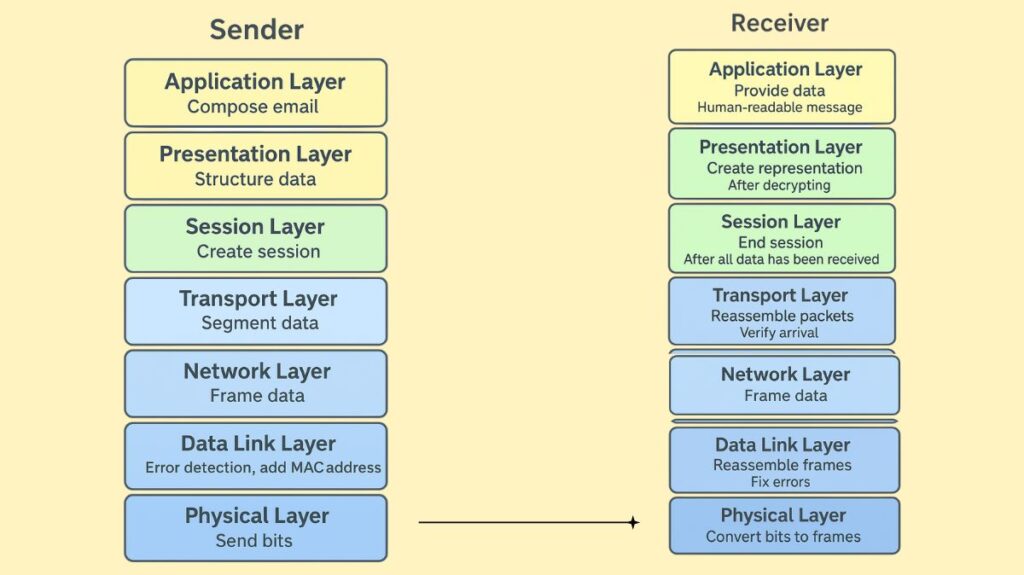
When data is moved between devices, it first moves down the sending device’s seven OSI model layers before moving back up the receiving device’s seven layers.
As an illustration, when sending an email:
Application Layer (Sender): In an email client (such as Outlook or Gmail), which employs a protocol like SMTP, the user composes an email.
Presentation Layer (Sender): Email data is structured for transmission (e.g., encrypted, compressed).
Session Layer (Sender): Between the email servers of the sender and the recipient, a session is created.
Transport Layer (Sender): Sequence numbers and information about error-checking are added once the email data is divided into smaller sections.
Network Layer (Sender): The optimal path across networks is determined by routing each segment, assigning source and destination IP addresses, and packaging it into a packet.
Data Link Layer (Sender): Error detection, MAC address addition for local devices, and packet encapsulation into frames are all done.
Physical Layer (Sender): After being transformed into raw bits, such as electrical impulses or light pulses, frames are sent via the actual network medium, such as cables or Wi-Fi.
Upon reaching the receiving device, the process reverses:
Physical Layer (Receiver): Returns the electrical bits and signals to frames.
Data Link Layer (Sender): Fixes errors and puts frames back together to generate packets.
Network Layer (Sender): Verifies that packets arrived correctly and puts them back together into segments.
Transport Layer (Sender): Handles sequencing and puts segments back together to create the original data.
Session Layer (Sender): Ends the session after it has been maintained until all of the data has been received.
Presentation Layer (Sender): Creates a comprehensible representation for the data after decrypting it.
Application Layer (Sender): Provides the recipient’s email client with the human-readable data so they may read the message.
You can also read CCNA Topics And What Is A CCNA Certification In Networking?
OSI Model vs TCP/IP Model
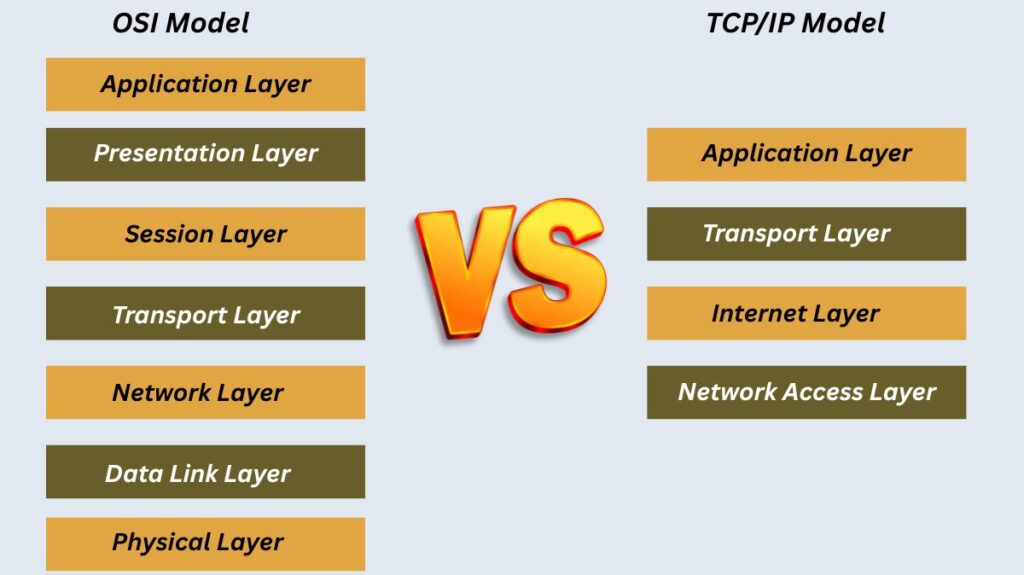
Although the OSI model is a theoretical structure, the TCP/IP model is founded on standardized protocols that are extensively used in actual networks.
Layers: Whereas TCP/IP has four layers, OSI has seven.
Layer Consolidation: A single Application layer is created in TCP/IP by combining the Session, Presentation, and Application layers of the OSI model. TCP/IP combines the Physical and Data Link layers of OSI into the Network Access layer.
Purpose: An all-purpose, protocol-neutral paradigm, OSI aims to characterise all types of network communication. TCP/IP is a functional model built on particular, standardised protocols that was created to address certain communication issues.
Usage: The OSI model is useful for creating new protocols and for teaching, although it is not as frequently utilized in real-world applications. Because of its pragmatic approach and practicality, TCP/IP has become the foundation of contemporary networking.
Necessity of Layers: Only the first, second, and third levels of the OSI model are required for all data transfer. In TCP/IP, data transfer typically requires all levels.
Layer Integration: Each OSI layer has a largely autonomous set of protocols. Layers are increasingly interconnected with TCP/IP, with certain layers depending on others.
Advantages of the OSI Model
Simplifies understanding and troubleshooting: Divides network communication into levels that are easy to handle.
Standardizes communication: Each layer contains set protocols and functions that enable communication between software and devices from many vendors (open interoperability).
Modular design: Enables separate layer development and upgrades and quicker innovation without affecting the network stack as a whole.
Streamlined knowledge sharing: Aids developers in sharing simpler models and conceptualizing networks.
Disadvantages of the OSI Model
Complexity: It can be difficult for novices to comprehend its seven layers.
Theoretical focus: Being more of a theoretical framework, it is less immediately applicable to networking in the real world, where more straightforward models like TCP/IP are favoured.
Efficiency: Every layer adds its own rules and functions, which could result in a less effective and time-consuming procedure.
You can also read What Is A Metropolitan Area Network Architecture & Benefits
