Network Bridges
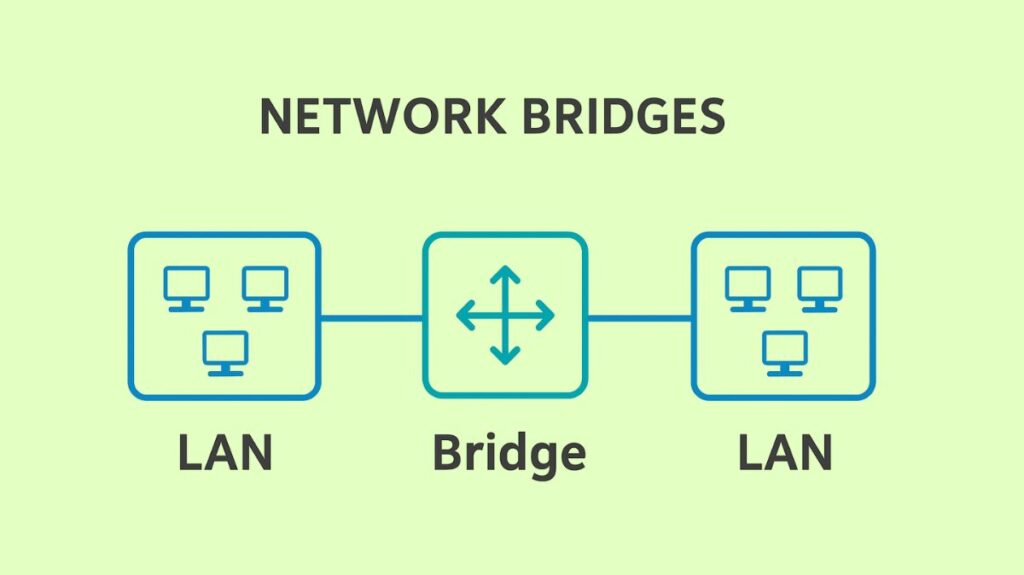
By joining two or more network segments, a bridge is a local internetworking device that creates a wider network. For increasing network reach and performance, they are regarded as a crucial networking tool.
In the 1980s, bridges were originally used to join Ethernet segments and increase a network’s coverage area. In order to join several segments to create a bigger network, they were first employed to get around Ethernet networks’ distance restrictions.
How Does Network Bridge Work
Operational Layer and Core Functionality
OSI Model Layer: Layer 2 of the OSI (Open Systems Interconnection) model is the Data Link Layer, where a bridge functions.
MAC Addresses: Bridges decide how to forward traffic based on the MAC addresses of devices. They deal with hardware addresses instead of IP addresses.
Learning Process (MAC Address Learning): When a bridge is turned on, it looks at the incoming frames’ MAC address and creates a filter table, sometimes referred to as a MAC address table or learning table. The bridge uses this table to determine which hosts are reachable via which interfaces. As hosts move or new ones join, this ongoing learning process adjusts.
Filtering: The bridge blocks traffic if the destination MAC address is on the same network segment. It speeds up and decongests networks by cutting unneeded traffic.
Forwarding: Only the relevant segment where the destination device is known to reside receives the frame from the bridge if the destination MAC address is on a different segment.
Flooding: Flooding occurs when the bridge broadcasts or transmits a frame to all segments or devices other than the one from which it was received if it does not know the destination MAC address (it is not listed in its filter table).
Signal Regeneration: Physically speaking, bridges may either fully regenerate the signal or increase its power like a repeater.
Transparency: Bridges seem as a single, complete network because hosts are not aware of their existence. They are also self-learning and plug-and-play gadgets.
You can also read What Are Firewall Logs? Benefits And Importance Of Firewalls
Relationship with Hubs and Switches
The ability of bridges to evaluate incoming frames and decide whether to advance or drop them depending on addressing information makes them more intelligent than hubs. All packets are amplified to the other side by hubs without any clever screening.
In essence, a LAN switch is a multiple-port bridge with extremely fast speed. At the same time, contemporary switches can contain hundreds of ports, whereas traditional bridges usually had just two or four (some 16).
LAN segments are connected by bridges and switches, which both use MAC address tables and aid in traffic reduction. Modern switches use specialized hardware (ASICs) for significantly lower latency and greater throughput, while bridges often use software to conduct switching. This is a significant difference.
Collision and Broadcast Domains
A network can be divided into several collision domains with the help of bridges. By enabling several devices to communicate concurrently without crashing, this segmentation expands the useable bandwidth available to individual stations.
Bridges, however, do not divide broadcast domains. Bridges always propagate broadcasts since all network devices must process them; hence, all segments in a bridged environment stay inside the same broadcast domain.
Different Types of Network Bridges
There are generally three types of bridges:
Transparent Bridges: When stations are added or removed, the network does not need to be reconfigured since transparent bridges, sometimes referred to as learning bridges, are “invisible” to other network devices. Blocking or forwarding data depending on the MAC address is their main duty. Plug-and-play and self-updating, they are.
Source Routing Bridges: To ensure that the frame follows a predetermined path, source routing bridges, which were created by IBM for Token Ring networks, require the station to incorporate the full frame’s route within the data frame. They are employed to avoid looping issues.
Translational Bridges: The received data is converted from one networking system to another by translational bridges. Alternatively, it is employed to transfer data or interact between two distinct networking system kinds. The translational cable will be used to connect the networking system and transmit data, just like an Ethernet cable would be used to transport data from a token ring.
Other specific implementations include:
Wireless Bridge: An Access Point (AP) in bridge mode can wirelessly connect two wired LANs. This allows networks to be extended across great distances without the need for physical cable, frequently joining buildings.
Workgroup Bridge (WGB): A Cisco-exclusive technology that enables several wired devices to join a wireless network by connecting them all via a single wireless link.
Brouter: A device that combines the capabilities of a bridge and a router is called a router. Routable and non-routable protocols are routed and bridged by it. These days, routers are less widespread because Layer 2 switches and Layer 3 routers usually incorporate their features.
Models of Bridging
Bridging locally, Local cables are used for local bridging, which links LAN switches. Regardless of whether they are linked to actual LANs or virtual hubs, this enables unrestricted communication between computers on the same Ethernet segment. When LANs in the same vicinity need to communicate directly at the link layer, this technique is employed.
Remote Linking two bridges are connected by remote bridging via a wide area network (WAN). When Local Area Networks (LANs) need to communicate at the link layer and are spread across multiple geographic locations, this paradigm is employed.
Applications and Uses of Bridges in networking
Bridges have a variety of applications in computer networks:
Network Segmentation: By establishing distinct collision domains, network segmentation helps to enhance performance and lessen network congestion by breaking up big networks into smaller parts.
Extension of Network Reach: Bridges link several network segments, enabling devices on those segments to communicate as though they were on the same segment. This increases the network’s physical size and reach.
Interconnection of Different Network Types: They may link many network segment types, including Ethernet, Token Ring, and FDDI, enhancing interoperability.
Wireless Network Bridging: Connecting a wireless network to a wired network increases its coverage and range.
Network Redundancy: If the primary connection breaks, bridges can create redundant network paths to boost network resilience and reduce downtime.
Home networking: They can facilitate smooth device connectivity in a home setting by integrating wired and wireless networks.
Advantages of Bridge in Networking
Improved Network Performance: Better network performance is achieved by lowering congestion and increasing data transfer rates, which results in quicker network speeds and lower latency.
Better Network Security: They lower the possibility of network assaults and prevent unwanted access by establishing logical isolation between network parts.
Flexible Network Design: Allows connecting different network technologies.
Easy to Install and Configure: They require minimal configuration and maintenance, making them suitable for small to medium-sized networks.
Separate Collision Domains: This results in more bandwidth.
Highly Reliable and Maintainable.
Protocol Transparency.
Disadvantages of Bridge in Networking
Limited Scalability: Congestion and performance deterioration may result from adding more devices and segments, therefore they might not be appropriate for bigger networks.
Single Point of Failure: Until it is replaced, a bridge failure may result in network outages.
Limited Functionality: Bridges are not as functional as hubs like switches and routers.
Higher Cost: More costly than hubs.
Slower Speed: Because seeing MAC addresses requires more processing.
Inefficient for Broadcast Traffic: Broadcast traffic is inefficient since it is impossible to filter broadcast data individually, which can result in “broadcast storms” and heavy broadcast traffic.
Increased Latency: Because bridges require computing time for address analysis, Cyclic Redundancy Check (CRC) computation, and temporary frame storage if a port is occupied, they can cause a 10% to 30% increase in network latency.
Spanning Tree Protocol (STP) Context
To avoid network loops in Layer 2 switched systems with redundant links, bridges and switches take part in the Spanning Tree Protocol (STP).
The STP topology uses a root bridge as its reference. The 8-byte Bridge ID (BID) determines the root bridge from the device’s 6-byte MAC address and 2-byte priority field.32,768 is the default priority value.
A loop-free topology is achieved by bridges exchanging Bridge Protocol Data Units (BPDUs) to provide STP information and identify port responsibilities (e.g., designated, root, backup) and states (e.g., blocking, listening, learning, redirecting).
When every port on bridges and switches has changed into a stable forwarding or blocking state, a STP network converges. Until this process is finished, no data is sent. Eighty-two seconds is the default convergence time for 802.1D STP.
You can also read What Is A Firewall? History Of Firewalls, Types Of Firewalls
