We covered subnetting in this blog, including its definition, key concepts, how it works, why it is important, benefits of subnetting, disadvantages, and advanced subnetting concepts, which are explained below.
Subnetting
The process of splitting a single, big IP network into smaller, easier-to-manage sections known as “subnets” or “subnetworks” is known as subnetting, and it is a basic networking concept. Effective IP routing, network administration, and general network optimization depend on this procedure. While still being a part of the main network, each subnet operates as a separate tiny network.
In simple words: Subnetting is the process of splitting a large network into smaller ones for security, performance, and efficiency.
Key Concepts in Subnetting
A few fundamental ideas are necessary to comprehend subnetting:
Also Read About Network Switching: How Switches Connect For Device Networks
Subnet
- Subnet A smaller, logical group inside a larger network is called a subnet.
- It gives every group of devices a separate area for communication.
IP addressing
- A device on a network can be uniquely identified by its IP address.
- The four “octets” that make up an IPv4 address are separated by dots (e.g., 192.168.1.1).
- A network portion, also known as a network ID, identifies the network to which the device belongs, and a host portion, also known as a host ID, uniquely identifies a device within that network. These are the two primary components of every IP address.
- IPv4 addresses are divided into classes (A, B, and C) according to the length of their host and network segments. A Class C network, for instance, has an 8-bit host ID and a 24-bit network ID.
Subnet Mask
- In IP addressing, a subnet mask is a 32-bit value that separates the host and network components of an IP address.
- It assists devices and computers in identifying which portion of an IP address corresponds to the network they are on and which portion corresponds to their host, or precise location, within that network.
- The subnet mask is made up of binary 1s and 0s, where the host portion is represented by a 0 and the network/subnet sections by a 1.
Example: 255.255.255.0
Host portion = .0 to .255
Network portion = 192.168.1
Common Subnet Masks
/24→ 255.255.255.0 → 254 usable hosts/25→ 255.255.255.128 → 126 usable hosts/26→ 255.255.255.192 → 62 usable hosts/30→ 255.255.255.252 → 2 usable hosts (used in point-to-point links)
CIDR Notation
- CIDR (Classless Inter-Domain Routing) notation uses a slash and a number (e.g., /24) to simplify the representation of subnet masks.
- The number following the slash shows how many bits were used for the IP address’s network component.
- Example:
/24=255.255.255.0(24 bits for network, 8 bits for hosts).
Reserved Addresses within Subnets
- Subnet ID (Subnetwork Address/Subnet Number): When all host bits are set to zero, the first (lowest) numeric address in a subnet’s range is its Subnet ID (Subnetwork Address/Subnet Number).
- Subnet Broadcast Address: It cannot be linked to a host; instead, it identifies the subnet itself. When all host bits are set to 1, the subnet broadcast address is the final (highest) number in the subnet’s range. It cannot be assigned to a host, and packets addressed to this address are sent to every host in that particular subnet.
- Usable Host Addresses: All IP addresses that fall between the subnet ID and the subnet broadcast address are considered usable host addresses. These can be linked to real network devices, or hosts. The formula 2^H – 2, where ‘H’ is the number of host bits, is used to determine the number of acceptable hosts.
- Subnet Zero: In the past, the initial subnet, which consisted of all zeros, was not used by default; however, contemporary systems permit its use in order to improve address efficiency.
Also Read About What Is Repeater In Networking, How It Works And Advantages
How Subnetting Works
The fundamental process of subnetting entails “borrowing bits” from the IP address’s host section and redistributing them to form a subnet portion. As a result, there are fewer host addresses accessible in each subnet.
Subnet Masks and IP Address Parts
Each device on the network needs to know which portion of an IP address identifies the host and which part identifies the network in order for subnetting to work. To do this, a subnet mask is used.
- A 32-bit value made up of binary 1s and 0s is called a subnet mask.
- The host portion of the IP address is represented by the 0s in the subnet mask, whilst the network and subnet portions are represented by the 1s. The host part’s size is directly determined by the number of zeros.
- There are three ways to express IP addresses and subnet masks
- Binary.
- DDN, or dot-decimal notation (255.255.255.0).
- For example, /24 is a prefix notation (CIDR). The number of network/subnet bits activated is indicated by the slash notation.
- To facilitate communication across several subnets, routers are utilized.
- A device utilizes the subnet mask when sending a packet to identify whether the recipient is on the same network or a different one. The packet is routed across the network if the destination is on a different subnet.
- Subnet masks are used by internal routers to divide data into subnetworks inside a network. They are utilised internally for effective routing but do not travel over the internet.
A Class C Network Subnetting Example:
Let’s say you have:
- Network:
192.168.1.0/24 - This means:
- 256 total addresses (
0–255). - Usable: 254 hosts (
1–254).
- 256 total addresses (
Now, if you subnet it into two subnets (/25):
- Subnet 1:
192.168.1.0/25→ hosts:1–126 - Subnet 2:
192.168.1.128/25→ hosts:129–254
Each subnet can now hold 126 usable hosts.
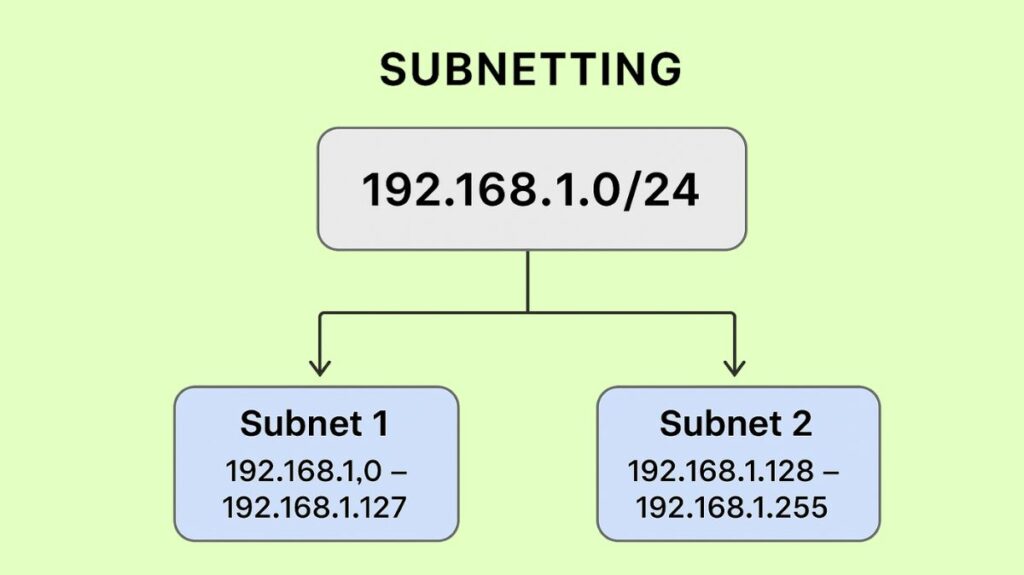
Think about a business that has 256 IP addresses on a Class C network (such as 192.168.1.0/24).
- In the absence of subnetting, all 256 IP addresses are accessible to all users, resulting in IP waste, performance problems (data overloads the network), and security threats (critical data is accessible to everybody).
- The network can be divided into smaller subnets using subnetting. If separated into two subnets (/25) for example:
- Subnet 1: 192.168.1.0 – 192.168.1.127, offering 126 usable hosts.
- Subnet 2: 192.168.1.128 – 192.168.1.255, offering 126 usable hosts.
The Subnetting Process (IPv4) typically involves four steps:
The IPv4 Subnetting Process
Four primary phases are usually included in subnetting:
- Choose which bits to borrow based on the desired number of subnets or the necessary number of hosts per subnet.
- 2^S, where ‘S’ is the number of borrowed subnet bits, is the number of subnets that can be created.
- Find the updated subnet mask: To the default network bits, add the borrowed bits. Prefix notation or dotted-decimal notation can be used to express this.
- Find the Magic Number, or subnet multiplier: The subnets can be readily listed using this value. It is computed as 256, which is the subnet mask’s interesting octet value. The subnet mask’s “interesting octet” is the octet that isn’t 0 or 255.
- Enumerate the broadcast addresses, host ranges, and subnets: To obtain consecutive subnet IDs, start with the network ID (which, when enabled, is also the zero subnet) and keep adding the magic number. The number that comes right before the ID of the following subnet is its broadcast address. Between the broadcast address and the subnet ID are the useable hosts.
IPv6 Subnetting
Unlike IPv4 addresses, which are 32-bit, IPv6 addresses are 128-bit. In IPv6, subnetting is still used to divide address blocks. Like IPv4, IPv6 global unicast addresses include taking a larger block and dividing it into subnets. A /64 prefix length is frequently used when assigning IPv6 subnets.
Also Read About Importance Of Computer Network Security Protect Your Data
Why Is Subnetting Important
- Efficient Use of IP Addresses: By dividing a large network into smaller portions, subnetting saves IP addresses. Subnets use only the addresses they need.
- Better Network Performance: Subnetting speeds up communication and reduces network congestion by lowering broadcast traffic.
- Improved Security: Subnetting isolates departments and groups, improving security. This simplifies access controls and data security.
- Simplifies Management and Troubleshooting: Simplifies Management and Troubleshooting Locating, managing, and fixing network issues is faster with smaller subnets.
- Scalability: Subnetting organises network growth. New subnets can be introduced without system change.
- Efficient Routing: Subnetting simplifies route summarisation, reducing routing table size and speeding routing.
Benefits of subnetting
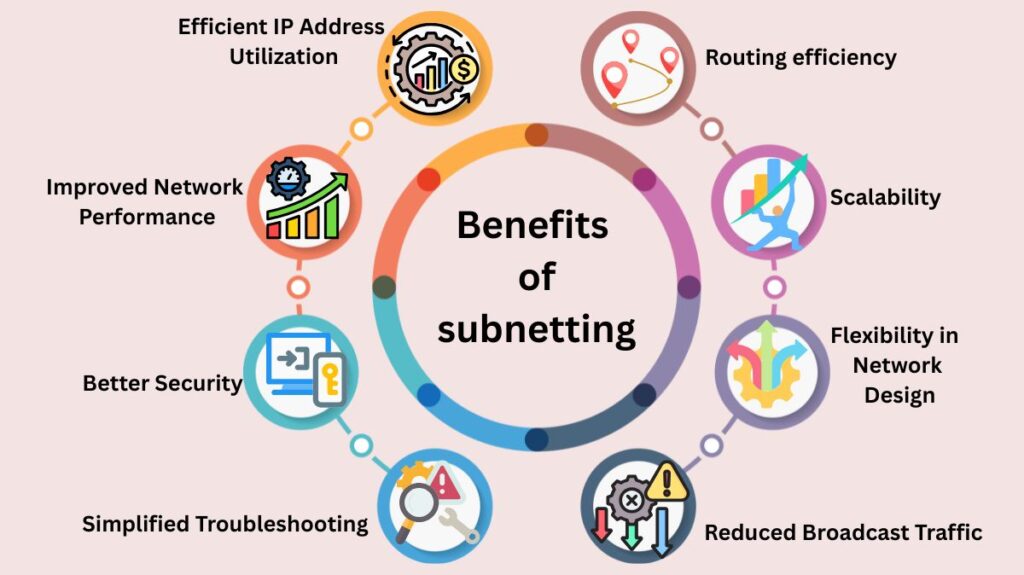
- Efficient IP Address Utilization: Subnetting divides a big network into smaller, more manageable pieces to conserve IP addresses.
- Improved Network Performance: Smaller networks minimise congestion and speed data flow since subnet broadcasts are constrained.
- Better Security: Subnets segregate important network areas, making access management and data protection easier.
- Simplified Troubleshooting: Because the network is divided, problems are easier to discover and rectify.
- Reduced Broadcast Traffic: Messages are broadcast exclusively within the subnet.
- Flexibility in Network Design: Subnetting lets organisations design networks by department, location, or function.
- Scalability: Add subnets without rewriting the system as the network grows.
- Routing efficiency: Subnetting decreases routing table size and speeds up routing decisions by summarising routes.
Disadvantages of Subnetting
Subnetting has a number of disadvantages despite its many advantages.
- Enhanced Complexity: Compared to a subnetted network, fewer steps are needed in a single network for data to reach a process.
- IP Address Waste (per subnet): In contrast to a single network, which wastes only two IP addresses overall, each subnet created wastes two IP addresses (Subnet ID and Broadcast address).
- Higher Cost: Subnetting necessitates the use of extra internal network equipment, such as hubs, switches, routers, and bridges, all of which can be expensive.
Advanced Subnetting Concepts
Within the same network address space, subnets of varying sizes can be created using the Variable-Length Subnet Masks (VLSM) approach. Compared to classful subnetting, which frequently wastes IP addresses, VLSM is more effective in allocating addresses. It is advised to begin subnetting with the biggest host demand first in order to prevent overlapping address spaces using VLSM.
The opposite of subnetting, route summarization (also known as supernetting or route aggregation) combines smaller subnets into a single, bigger network address for routing reasons. By promoting a single summary route rather than numerous separate subnet routes, the main advantage is to speed up the routing process and minimize the size of router routing tables. Careful network architecture is necessary for this.
Also Read About Computer Network Security Measures: Protect Your Network
