All of the following topics were discussed in this article: what packet filtering firewalls are, how it work, key features, types, Advantages, disadvantages of packet filtering firewall, use cases, and comparisons with other technologies.
What is a packet filtering firewall?
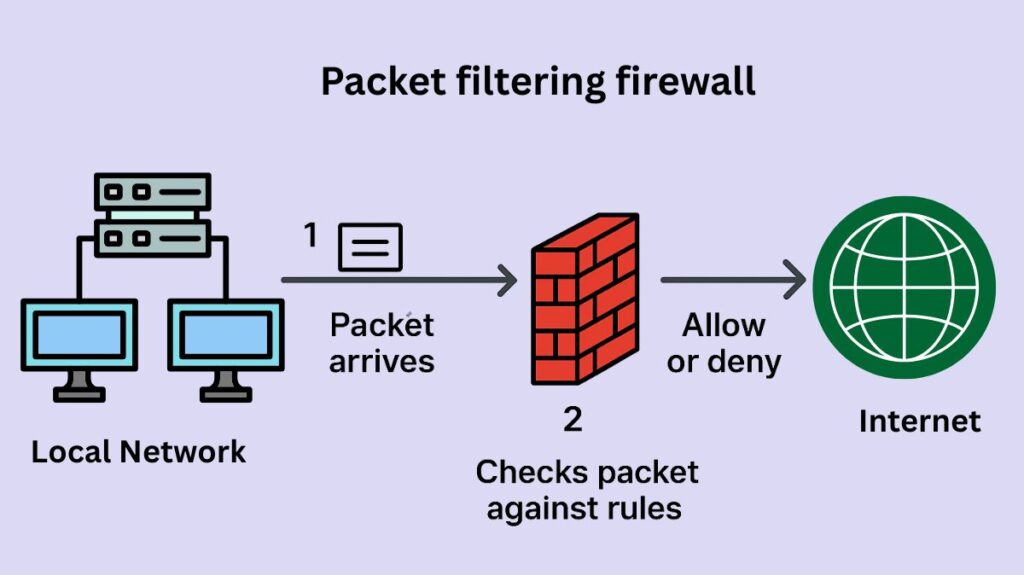
Packet filtering firewalls are network security tools that act at the network layer of the OSI model to regulate network traffic by examining packet headers and permitting or prohibiting packets according to pre-established criteria. Usually based on source and destination IP addresses, port numbers, and protocols, these rules also referred to as Access Control Lists, or ACLs do not examine the packet’s actual contents. Although packet filtering firewalls are quick and resource-efficient, they have drawbacks because malicious or designed packets can get past them and they don’t check packet contents for threats.
How Packet-Filtering Firewalls Work
At the edge of the network, packet-filtering firewalls serve as a virtual gatekeeper. The firewall looks at certain information in a data packet’s header when it arrives, including:
- IP addresses identify packet senders and receivers.
- Port 80 handles HTTP traffic.
- Protocols: ICMP, TCP, UDP.
- Protocol header flags, such as a signal requesting a connection.
- The Network Interface Cards(NIC), or physical interface, that the packet is travelling through.
ACLs, or predetermined rule sets, are compared to this data. A packet is destroyed by the firewall if it matches a denial rule; if it matches a rule that permits it, it is allowed to pass. A default action is normally to refuse all traffic if no rule matches. According to the OSI Model, these firewalls normally operate at the network layer (Layer 3) and transport layer (Layer 4).
Characteristics of packet filtering firewall
Characteristics of packet-filtering firewalls include:
- Using rule sets on networks that receive data.
- Individual data packets can be affected.
- Making use of external packet data, such as data transfer protocols, source and origin ports, and IP addresses.
- Deep packet inspection is not being done.
- They are often stateless, which means they evaluate packets on their own without recalling or picking up on past behavior.
Types of Packet-Filtering Firewall
Firewalls using packet filtering come in a variety of forms:
Stateless Packet-Filtering Firewalls
Among the earliest solutions are stateless packet-filtering firewalls, which handle each packet separately and are unaware of previous packets or the link to which they belong. They only use established regulations (ACLs). Despite being quick and resource-efficient, they are susceptible to assaults like IP spoofing because of this lack of context. They are frequently utilized for low-power customer-premises equipment or domestic internet customers.
Stateful Packet-Filtering Firewalls
Also referred to as dynamic packet filters, they are more sophisticated since they keep a “state table” of all open connections in addition to inspecting the packet header. By comprehending the context of the traffic, they are able to make more informed judgements. For example, they can only allow incoming response packets if they are a part of a connection that was started by an internal user. Compared to stateless firewalls, this provides a higher level of security.
Also Read About What Is DNAT Destination Network Address Translation? Uses
Static Packet-Filtering Firewalls
Network managers must manually develop and modify firewall rules for this popular kind. Until an administrator modifies permissions, both internal and external network connections are either open or closed. They are simple and function best in networks with fewer users and smaller applications.
Dynamic Packet-Filtering Firewalls
These enable dynamic rules that satisfy predetermined criteria, including ports staying open for only predetermined amounts of time. Compared to static filters, they are more adaptable and may automate routine tasks, improving security without compromising the functioning of applications.
Advantages And Disadvantages Of Packet Filtering Firewall
Advantages of Packet Filtering Firewall
The following are some advantages of packet-filtering firewalls:
- Speed and Efficiency: They make decisions rapidly by evaluating only packet headers at the network layer, reducing network overhead and processing time.
- They are inexpensive security solutions because they are integrated into routers and easy to install and configure.
- Transparency: They operate without user intervention or warning unless a packet is dropped, ensuring network security does not compromise user experience.
- Basic Protection: By restricting undesired traffic and thwarting IP spoofing attempts by authenticating source IP addresses, they offer a basic level of protection.
Disadvantages of Packet Filtering Firewall
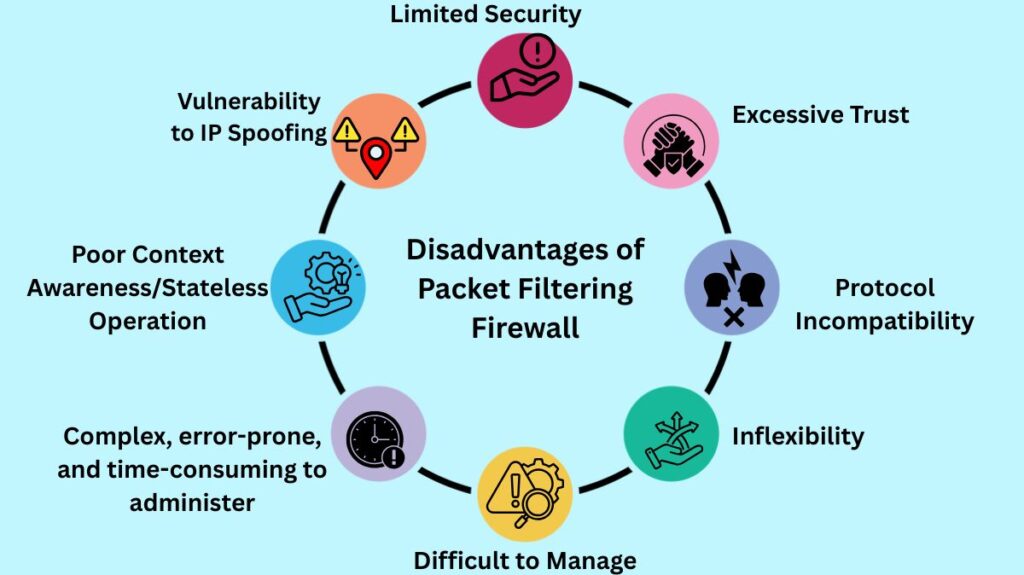
While beneficial, packet-filtering firewalls have disadvantages:
- Limited Security: They cannot inspect data packet payloads, making them vulnerable to malicious malware in legal traffic.
- Vulnerability to IP Spoofing: Spoof packets can pass stateless firewalls if the source IP address matches an authorised one because they simply examine static header data.
- Poor Context Awareness/Stateless Operation: They cannot recognize malicious traffic patterns or protect against complex threats since they process each packet separately and do not recollect prior packets or sessions.
- Complex, error-prone, and time-consuming to administer: Rule sets require manual configuration and updates in big networks.
- Difficult to Manage: They log little data, making it hard for businesses to comply and notice questionable activities.
- Inflexibility: They cannot dynamically adjust to changing security concerns because they use manually updated rules rather than threat management automation.
- Protocol Incompatibility: There may be issues with certain protocols that need state information or dynamic port allocation.
- Excessive Trust: Because they don’t check payloads or record previous data, they are unable to completely apply Zero Trust principles, leaving them open to hostile actors posing as reliable users.
Also Read About Network Controllers: How It Work, Advantages, And Components
Use Cases
There are several uses for packet-filtering firewalls:
- Stopping all incoming traffic from an IP address that seems suspicious.
- Blocking other connections, such Telnet or UDP segments, and only permitting certain traffic, like HTTP (port 80) and HTTPS (port 443), to a web server.
- Examining the source IP addresses of incoming packets helps prevent IP spoofing attacks.
- Controlling and optimising network traffic flow by restricting traffic between various subnets inside a company.
- Situations when efficiency of resources and quickness are given priority.
Comparison with Other Technologies
Application Gateways (Proxy Servers)
The most secure kind of data connection is offered by application-level gateways (bastion hosts), which function at the application layer and analyze all communication layers, including application data, in contrast to packet filters that function at the network level. Proxies provide better content filtering, user authentication, and the ability to anonymize internal network traffic.
Stateful Inspection Firewalls
These are an improvement on conventional packet filtering since they keep track of the status of active connections and preserve context awareness of network traffic. They create a dynamic control flow that detects assaults that basic packet filtering could overlook, allowing for more precise and secure data packet assessment.
Circuit-Level Gateways
These offer session-layer security by confirming the validity of sessions without looking through the contents of packets. They add a layer of protection by stopping attacks that take use of flaws in session management protocols by monitoring the session status of connections.
Next-Generation Firewalls (NGFWs)
NGFWs feature URL filtering, enhanced malware protection, contextual awareness, and deep packet inspection up to Layer 7, going beyond simple packet filtering. They also identify applications based on data.
Suppliers
WatchGuard Network Security, Palo Alto Networks, Fortinet, Cisco, Forcepoint, Barracuda Networks, Sophos, Versa Networks, SonicWall, and Check Point Software Technologies are a few well-known vendors of packet-filtering firewalls.
In conclusion
With their stateless design, lack of deep packet inspection, and limited security scope, packet-filtering firewalls are a basic and affordable network security solution, but they are not enough to protect large enterprise networks with complex and changing needs. Although they work well for home and small-scale applications, corporations often use them in a more complete security solution with stateful inspection or next-generation firewalls for greater protection, automation, and data insights.
Also Read About What is a Network Server, How it Works, Types and Components
