In this article, we learn about Social Engineering Attacks, Definition, How Social Engineering Works and Examples of Social Engineering Attacks
Social Engineering Attacks

A subset of network and cybercrime assaults known as “social engineering” attacks mostly use psychological manipulation as opposed to technological flaws to undermine security. Often called “human hacking,” the technique takes advantage of social behaviors, trust, and human error to obtain sensitive data, systems, or assets.
You can also read What is Reconnaissance Attack, How it Works, History & Types
Definition and Goals
The use of psychological coercion to get someone to do something or reveal private information is known as social engineering. Its main objective is to trick people into willingly divulging personal information, including bank account information, passwords, or computer system access.
Attackers take advantage of the fact that, even in networks with strong software and systems, end users pose a serious security risk. The two main objectives of the attacks are either sabotage (disturbing or damaging data) or stealing (getting goods like money, information, or access). The primary source of network breaches nowadays is social engineering, which appeals to cybercriminals because it allows them to get over robust technological controls like firewalls and antivirus software.
How Social Engineering Works
Social engineering assaults are particularly successful at influencing a user’s behavior since they are based on human thought and behavior.
Exploiting Human Emotions and Tactics
Attackers manipulate emotions and instincts to bypass logical thinking and critical judgment. Key emotions and tactics exploited include:
Fear and Urgency: Fear and urgency override critical thinking skills by causing anxiety and hurried behaviors. Attackers may use messages like “respond now or account closed” that contain threats or urgent deadlines.
Greed/Excitement: Using the promise of a reward or a valuable thing, greed or excitement lowers caution by taking advantage of the drive for gain.
Curiosity: Uses fascination to promote interaction, such as persuading people to download free software or plug in unknown media.
Helpfulness/Authority: Focusses on the natural desire to help, frequently by imitating trusted individuals, government organizations, or authoritative figures (such as IT support).
Trust: In order to create a credible story and establish legitimacy, attackers carry out research, which makes it simple for the victim to accept the falsehood.
Attack Cycle
Most social engineering attacks follow a cycle:
Preparation: Compiling background data about the victim or the group they belong to; frequently, this is done to personalize scams by studying targets on social media or LinkedIn.
Infiltration: Forming a connection or striking up a conversation, frequently by assuming a false identity or fostering trust.
Exploitation: Exploitation is the process of controlling a victim to perform a desired action (such as disclosing login credentials) once trust and a weakness have been developed.
Disengagement: After the user completes the intended action, the attacker departs.
You can also read Different Types Of MitM Attack, How It Works And Advantages
Examples of Social Engineering Attacks
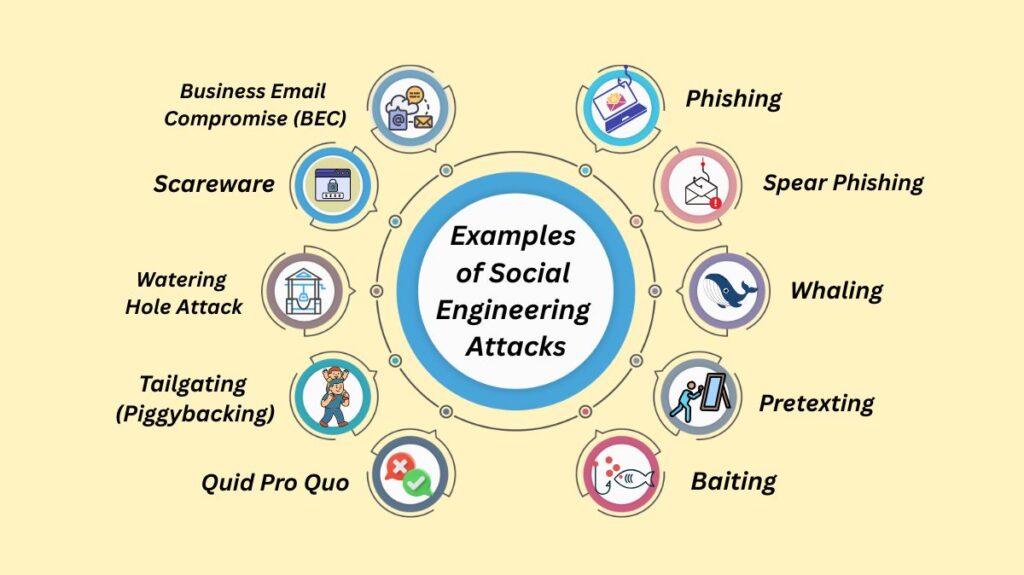
Social engineering forms the backbone of many cyber threats. While many attacks occur online, some can manifest in physical spaces like offices.
| Attack Type | Description | Delivery Methods |
|---|---|---|
| Phishing | The most pervasive method, using fraudulent messages to trick recipients into clicking malicious links, downloading attachments, or divulging sensitive information. Messages often appear to come from a trusted source, like a bank or company. | Email, text (Smishing), voice calls (Vishing), instant messages. |
| Spear Phishing | A targeted email scam that requires in-depth research to tailor messages to a specific individual or organization. | Email, often personalized using insider knowledge. |
| Whaling | A targeted phishing technique specifically aimed at high-profile individuals, such as CEOs, CFOs, or high government officials, to gain access to valuable company data. | Email (often disguised as a subpoena or executive issue). |
| Pretexting | The perpetrator assumes a false identity and creates an invented scenario (a “pretext”) to trick victims into giving up information, often used against organizations with abundant client data (like banks). | Phone, email, in-person (impersonating IT staff, vendors, or auditors). |
| Baiting | Exploits curiosity or greed by promising a reward or offering something enticing (the “bait”) in return for sensitive information or to lure the victim into installing malware. A common physical example is leaving malware-infected USB keys labeled with tempting titles (like “Confidential”) in public places. | Online ads/downloads, physical media (USB drives, CD-ROMs). |
| Quid Pro Quo | An exchange of information or services, where the attacker offers “assistance” (often posing as tech support) in exchange for access or login credentials. | Phone calls, online offers. |
| Tailgating (Piggybacking) | A physical attack where an unauthorized person follows an authorized person into a restricted area, often relying on the victim’s misplaced courtesy to hold the door open. | In-person access to secure buildings. |
| Watering Hole Attack | Uses advanced techniques to infect a website (or “watering hole”) frequently visited by the target group, spreading malware to specific visitors. | Compromised industry-specific websites. |
| Scareware | Bombarding the victim with fake threats and alerts (often pop-up banners) claiming the system is infected, forcing them to install malicious software or pay a fee to resolve the non-existent problem. | Websites, spam email, malicious software downloads. |
| Business Email Compromise (BEC) | A form of email fraud where the attacker impersonates a C-level executive to trick the recipient into performing an illegitimate business function, such as wiring money. | Spoofed or compromised executive emails. |
Protection and Mitigation Strategies
Because social engineering includes human psychology, protection against such attacks is difficult. A major component of mitigation techniques is user awareness and education:
Security Awareness Training: The best defense is to provide mandatory and frequent training. Employees who receive training are better able to identify and avoid these strategies. To show how attackers work, organizations should model assaults (such as phishing).
Verify Communications: Always be wary of unsolicited messages, particularly those requesting personal information or urgent action. Before responding to a request, especially one that is being pressured, confirm the sender’s identification via an independent, reliable method (such as phoning the person’s known number).
Cautious Digital Habits: Users should be advised to manually enter the verified, authentic URL into the address bar rather than accessing links that are included in emails. File names that seem strange or ambiguous should be avoided.
Technical Defenses: Use Multi-Factor Authentication (MFA), which lowers the possibility of account takeover even if passwords are compromised and adds a layer of security. Email security measures (such as SPF, DKIM, DMARC, and anti-phishing filters) can stop some assaults from getting to staff members.
Device and System Maintenance: Update operating systems and apps right away to fix known security flaws that hackers could take advantage of. Avoid putting random USBs or other unfamiliar physical media into your computer.
Policy and Physical Security: Clearly define security rules, such as how to handle passwords. Effective restrictions in physical locations include escort requirements, badges, and visiting logs.
Reporting: Provide a clear procedure for promptly alerting the security team or help desk to questionable emails or phone calls.
You can also read How To Prevent Password Attacks, Advantages & Disadvantages
