This topic included an introduction of watering hole attacks, how it works, important features and risks, examples, and how to prevent watering hole attack.
Watering hole attack
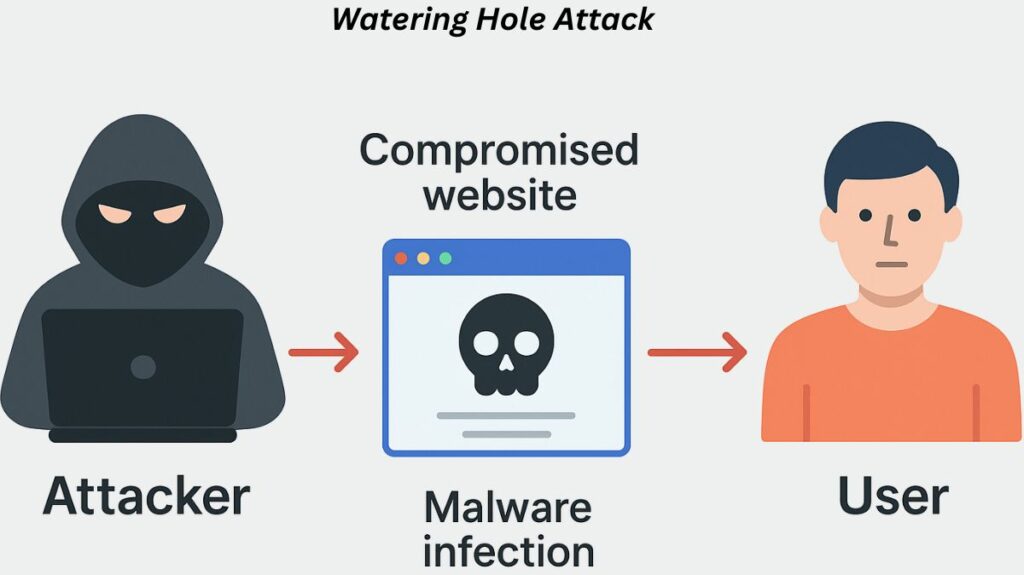
An attacker who uses a highly focused attack tactic known as a “watering hole cyberattack” compromises a trustworthy and genuine website that a particular user or organisation member is known to visit. In order to obtain access to the organization’s network, steal confidential data, or conduct espionage, this attack aims to infect the devices of the targeted users with malware when they visit the website.
A predator waiting at a watering hole in the wild to ambush unwary victims is the analogy from which the term “watering hole” originates. Another name for these attacks is strategic website compromise attacks.
Also Read About What Is Spear Phishing Attack? Phishing Vs Spear Phishing
How Watering Hole Attack Works?
These crucial steps are usually followed by the attack:
Target selection and reconnaissance: The attacker initially chooses a specific target group, which may include personnel from a given organisation, individuals of a particular industry, or a group with similar interests (such as government employees or financial analysts). After that, the attacker investigates the open websites, discussion boards, or trade publications that this group frequently visits.
Website Compromise: One of these reliable websites has a vulnerability that the attacker discovers and takes advantage of. This could entail utilizing methods like SQL injection, cross-site scripting (XSS) exploits, or just hacking the web server.
Infection: The attacker inserts malicious code or a drive-by download script into the website once they have control of it. This virus is frequently advanced enough to only target users who fit certain requirements, like having an IP address that is part of the network of the target business.
The Ambush/Exploitation: A victim from the target group’s device is immediately infected with malware when they visit the hacked website. The infection typically occurs transparently through a drive-by download attack, which means that the user only needs to visit the website to become infected they don’t need to click on a dubious link or open an attachment. Once deployed, the malware can be used to access linked corporate networks without authorisation or steal data.
The detection of these lures is especially difficult because attackers may even use emails that appear to be “harmless” and highly relevant to persuade users to visit particular sections of the hacked website. These emails may be delivered through the website’s automated email notifications or newsletters.
Important Features and Risks
Watering hole attacks are very successful because of a few special features:
Highly Targeted: These attacks are designed to compromise a particular victim group, in contrast to general phishing, which makes them an extremely successful strategy for getting access to a high-value network.
Bypasses Vigilance and Exploits Trust: The attack takes advantage of the victim’s faith in reliable and authentic websites. The victim is typically not on high alert for security threats because they are browsing a familiar website.
Use of Zero-Day Exploits: Zero-day exploits that take advantage of a software flaw before a manufacturer has issued a fix are frequently distributed through watering hole attacks.
Difficult to Detect: The assault can evade email scanners and ordinary security filters because it originates from a trustworthy website. It is difficult to block the websites. Additionally, the malicious code might not activate until it detects a particular target, making it more difficult to detect using network monitoring tools. The spyware and scripts are frequently carefully crafted, making standard antivirus software difficult to employ.
Watering Hole Attack Examples
The following are notable historical instances of this offensive strategy:
- 2012 US Council on Foreign Relations: A zero-day vulnerability in Microsoft’s Internet Explorer was the target of malware posted on the website.
- 2013 US Department of Labour: Attackers targeted users who were viewing pages with nuclear-related content on the website in order to take advantage of a zero-day vulnerability.
- Havex (2013): This virus targeted the petrochemical, pharmaceutical, defence, aviation, and energy industries by taking advantage of watering-hole and supply chain attacks.
- NotPetya (2017): This malware infected users and erased data after propagating via a hacked Ukrainian website.
- SolarWinds (2020): This method was employed by state-sponsored operatives to breach government agency and cybersecurity company networks.
How to prevent watering hole attack
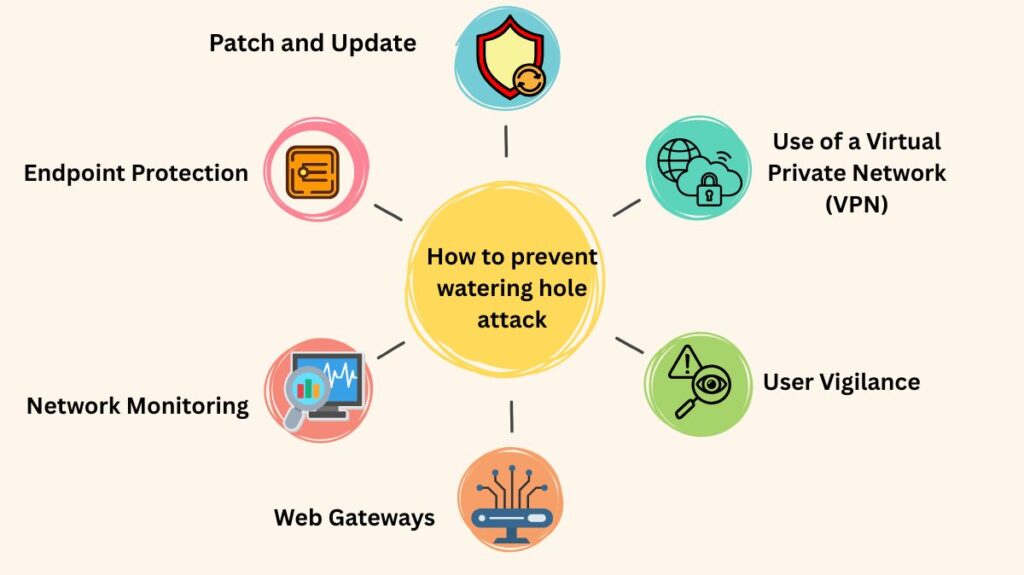
Users and organisations can protect themselves from watering hole attacks in a number of ways:
Patch and Update
To fix vulnerabilities that watering holes frequently take advantage of, keep operating systems, web browsers, and all software up to date with the most recent security updates.
Endpoint Protection
Protect your endpoints by using robust antivirus software and endpoint detection and response (EDR) programs that are able to identify and stop harmful scripts and drive-by downloads.
Network Monitoring
It is essential for detection that organisations keep an eye on network logs for odd traffic patterns and suspicious behaviour. On dubious destination websites, dynamic malware analysis tools can look for harmful activity.
Web Gateways
Web gateways can protect the company from opportunistic drive-by downloads that match a recognized signature or have a negative reputation.
User Vigilance
Even on reliable websites, people should use caution when clicking links or downloading data, and they should be on the lookout for dubious websites. Employers may also encourage staff members to adhere to zero-trust guidelines.
Use of a Virtual Private Network (VPN)
Use a Virtual Private Network(VPN) to encrypt communication when utilizing public Wi-Fi networks, which are vulnerable to watering hole attacks.
