This page discusses session hijacking, how it works, types, Impacts, session hijacking prevention, and how to mitigate session hijacking.
Session Hijacking

By effectively stealing the session token or cookie, an attacker can assume control of a user’s active session with a web application or service and pretend to be the authorised user without requiring their password. This is known as session hijacking. Until the session is ended, the hacker can access the user’s account, take activities, or steal data. TCP hijacking is a common term for this.
By obtaining the unique session identification or token, the attack seeks to get around security authentication methods like passwords and Multi-Factor Authentication (MFA). The attacker can pose as the system’s genuine user once they get this token.
Also Read About ICMP Attacks Types: Ping Flood, Smurf & Tunneling Explained
Understanding the Target: The Web Session
Because HTTP is stateless, websites employ sessions to store user context.
What is a Session?
Web servers and browsers communicate short, interactive data during sessions. Your session ends when you log out or automatically after inactivity. Logging in starts a website or app.
In order to preserve state in the stateless HTTP protocol, sessions are essential. They enable websites to retain user preferences and information between page requests. This takes into consideration personalized user experiences, including preserving login status or storing products in a shopping cart.
The server usually creates a distinct session ID at the beginning of a session. This ID is frequently attached to URLs or saved on the client side as a cookie. The server links the user to their server-side information using this ID.
The Session ID/Token:
The server creates a special session identifier (a token) if authentication is successful. Usually, this is a lengthy string of randomized alpha-numeric characters.This token is the account “key” during the session. Servers send IDs to client browsers, which store them in hidden fields, HTTP cookies, or URLs.
Maintaining State:
For each link visited or product added to a cart, the browser sends the Session ID cookie to the server. After ID verification, the server knows the user is authorised and linked to their account.t actors taking over sessions, can be prevented with session management. Sessions improve user experience and enable advanced web apps.
How Session Hijacking Works
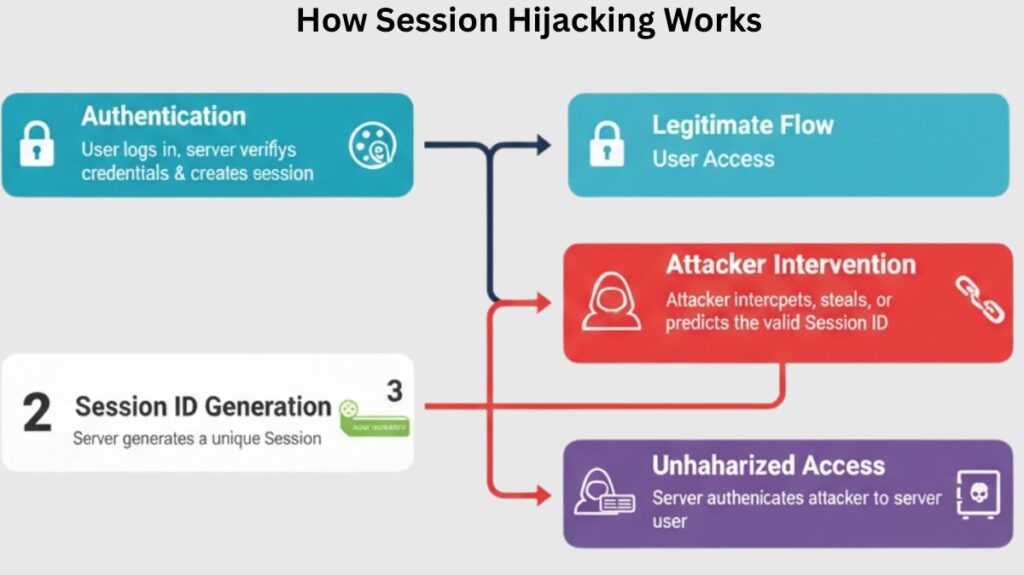
Following a successful authentication transaction, the attacker often places themself in between the claimant (user) and the verifier (server).
- Authentication: To access a website or application, the authorised user inputs their login information. After confirming these credentials, the server creates a fresh session connection for the user.
- ID Generation: The server generates a session ID after authentication. Long, random IDs are intentionally hard to guess. The browser stores this ID as a cookie from the server.
- Attacker Intervention: Advanced methods predict, intercept, brute-force, or spoof session IDs. It may exploit network vulnerabilities or web application session management issues.
- Impersonation: An attacker requests the server using a stolen or assumed ID. The session ID is legitimate, thus the server authenticates these requests.
- Unauthorized Access: The attacker takes confidential data, starts financial transactions, and performs other crimes with the same privileges.
Using stolen tokens, attackers reproduce a target’s logged-in session on another browser, evading multi-factor authentication.
Also Read About Different Types Of MitM Attack, How It Work And Advantages
Types of Session Hijacking Attacks
The two main types of session hijacking attacks are passive (monitoring to collect data) and active (including interception and instant usage or alteration). A number of particular techniques are frequently employed:
| Attack Method | Type | Description |
|---|---|---|
| Cross-Site Scripting (XSS) | Active | The attacker exploits web application vulnerabilities to inject malicious client-side scripts into a web page. When the victim views the page, the script executes, steals the session cookie (often using document.cookie), and sends it back to the attacker. |
| Session Fixation | Active | The attacker forces the target user to use a predetermined session ID that the attacker already knows. This is often done via a phishing scam involving a link containing the chosen token in the URL. Once the user logs in, the attacker can use the known, now authenticated, session ID. |
| Man-in-the-Middle (MITM) / Session Sniffing | Passive/Active | The attacker places themselves between the target and the web server, often exploiting compromised network devices or unsecured public Wi-Fi. They intercept network traffic to capture the session token, especially if the traffic is unencrypted (HTTP instead of HTTPS). Sniffers like Wireshark may be used to intercept data. |
| Predictable Session ID | Active | Attackers analyze patterns in how a web server generates session tokens (e.g., if they are based on sequential numbers, timestamps, or client data like the IP address). They then use this knowledge to guess or brute-force a valid token. |
| IP Spoofing | Active | The attacker obtains the client’s IP address and injects packets spoofed with that IP address into the TCP session to fool the server, particularly if the server relies on the IP address for session tracking. |
| Adversary-in-the-Middle (AITM) | Active | An advanced MITM attack where the attacker not only steals the token by eavesdropping but also actively manipulates the data being passed, potentially injecting malware. |
| Man-in-the-Browser | Active | Malware infects the user’s browser and covertly modifies transactions or initiates new ones without the user’s knowledge. Since requests originate from the victim’s infected device, they appear legitimate to the web service. |
Impacts of the Attack
Attackers can do full account takeover (ATO) through session hijacking. The results could be disastrous:
- Financial Loss: Unauthorised purchases, transfers, or transactions may be started by attackers.
- Data Breach/Theft: When attackers obtain private or sensitive company data, it may result in identity theft or corporate espionage.
- Reputational Damage: In addition to possible fines and legal repercussions, businesses who encounter session hijacking instances may suffer a major decline in consumer trust and brand loyalty.
- Greater Access: An attacker may be able to access several related systems using a hijacked session if Single Sign-On (SSO) is enabled.
Session hijacking prevention

Both website developers and users need to be vigilant in order to prevent session hijacking.
For Developers/Web Admins
Enforce HTTPS Everywhere
Use TLS/SSL encryption for all traffic, not just the login page, to enforce HTTPS everywhere. This stops the Session ID from being read in transit by Man-in-the-Middle attacks and session sniffing.
Secure Cookie Flags
- To stop client-side scripts (such as those used in XSS attacks) from accessing session cookies, set the HttpOnly setting.
- To guarantee that the cookie is only transferred over HTTPS, set the Secure flag.
Regenerate Session IDs
Whenever a user’s power level changes (for example, from a public page to a secure account setting) or after a successful login, a fresh, random Session ID should be produced. The main line of defence against session fixation is this.
Implement Session Timeouts
Give sessions a brief, manageable expiration time and end them when a user hasn’t used them for a while.
Monitor Session Parameters
Attach the session to parameters such as the User-Agent string or the user’s IP address. The session should be ended or re-authenticated if there is an unexpected change in the middle of it.
For Users
- Steer clear of public Wi-Fi for sensitive access: Avoid using insecure public Wi-Fi to access important services like email or bank accounts.
- Use a Virtual Private Network (VPN): Even when using public Wi-Fi, a VPN encrypts all of your communication, shielding your Session ID from local network sniffing.
- Log Out Correctly: To expressly end the session and render the server’s Session ID invalid, always utilise the designated “Log Out” button. The session could remain open even if you simply close the browser.
- Maintain Software Updates: To fix vulnerabilities that malware or XSS could exploit, update your operating system, browser, and security software on a regular basis.
How to mitigate session hijacking
- Force re-authentication and immediately invalidate all active sessions (server-side).
- Rotate and revoke any session identifiers or API tokens.
- Notify the impacted users and reset their passwords.
- For incident investigation, gather logs (IP, user-agent, and timestamps).
- Check endpoints for compromised devices and malware.
Also Read About What is a DNS Spoofing Attack or DNS Cache Poisoning
