TACACS+ Protocol
The main purpose of the popular security protocol TACACS+ (Terminal Access Controller Access-Control System Plus) is to give users centralized Authentication, Authorization, and Accounting (AAA) services when they access network devices like firewalls, switches, and routers.
TACACS+ is an improved version of the original TACACS protocol, which was developed in the 1980s by Cisco Systems. Although TACACS+ is a completely new and distinct protocol that is incompatible with its predecessors, TACACS and XTACACS, it has mostly supplanted them. Although TACACS+ is frequently preferred in Cisco-dominated workplaces, it was first made available as an open standard in 1993.
Importance
You can save your login and passwords on a central server by using remote authentication. Using RADIUS or TACACS+ on this central server has the benefit of allowing you to handle user additions, deletions, and password changes without having to set up changes on every individual network device. Devices continue to connect to the server for authentication after you make a single modification to the server’s configuration. Authorization and accounting are two further features offered by RADIUS and TACACS+, despite authentication being their most well-known feature.
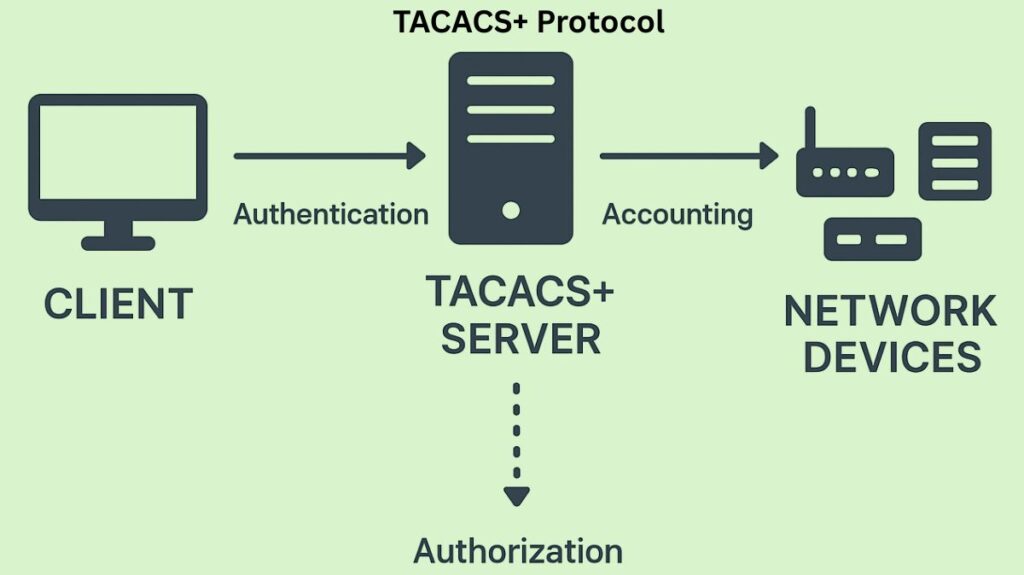
How does it work?
The AAA Framework
TACACS+ controls user access to network infrastructure while functioning under the AAA security framework.
- Authentication (A): This stage makes sure that only authorized users can access the network device by confirming the user’s identity, usually with a username and password.
- Authorization (A): Based on predetermined policies, authorization establishes exactly what the user is allowed to perform upon successful authentication.
- Accounting (A): This procedure creates an audit trail by recording and monitoring every user action. Accounting records contain data that can be utilized for reporting or auditing, including user IDs, start and stop times, and executed commands.
Also Read About What Is The AAA Framework Security For Network Admins
Key Technical Characteristics and Advantages
A number of technical characteristics set TACACS+ apart, especially from RADIUS:
Transport Layer and Reliability
- TCP Based: TACACS+ operates on Port 49 and makes use of the Transmission Control Protocol (TCP).
- Connection-Oriented: TCP offers a dependable, connection-oriented transport mechanism that guarantees dependable delivery. UDP (used by RADIUS) lacks built-in support mechanisms that TCP offers, namely instantaneous notice (a reset, or RST) in the event that a central server stops or fails.
Enhanced Security
Complete Packet Encryption: TACACS+ encrypts the full payload, or body, of the packet that is sent back and forth between the client and server devices. This safeguards all private data, including session information, authorization parameters, and user credentials. The entire body is encrypted, but a typical TACACS+ header is left behind. RADIUS, on the other hand, encrypts the password solely inside the access-request packet.
Separation and Granular Control
Division of AAA Functions: The Accounting, Authorization, and Authentication operations are clearly divided by TACACS+. Significant flexibility is offered by this split; for instance, administrators can utilize TACACS+ for authorization and accounting services and Kerberos for authentication.
Granular Authorization Control: TACACS+’s capacity to provide fine-grained control over user operations, frequently down to the command level, is one of its main advantages. Administrators have the ability to specify which commands a user is permitted to run on the network device. It is perfect for protecting administrative access because of its strong functionality.
Router Management: Because TACACS+ allows command authorization on a per-user or per-group basis, either by explicitly defining permissible commands in the server or by assigning permission levels to instructions, it is often more helpful for router management than RADIUS.
Also Read About What Is The AAA Framework Security For Network Admins
Operational Flow (Client-Server Model)
TACACS+ uses a client-server architecture to function. To control access, network devices (clients or Network Access Servers, NAS) communicate with a central TACACS+ server.
Request and Authentication: A user tries to access a client device, like a router, to log in. The TACACS+ server receives the credentials from the client and compares them to a central database to confirm the user. In order to get more information, the server could converse with the user during this procedure.
Server Reaction: One of four primary messages is returned by the server:
- ACCEPT: After successful authentication, the service can start. It moves on to the next stage if authorization is needed.
- REJECT: Access is refused because the user is not authorized.
- ERROR: The client tried a different authentication method (such as a local database) when an error occurred, possibly as a result of a server or network issue.
- CONTINUE: More authentication details are requested from the user.
Accounting and Authorization: The device makes another connection to the TACACS+ server if authentication is successful and authorization is turned on. The services, session duration, and command limits for the user’s session are determined by the attributes (Attribute-Value or AV pairs) that are frequently included in the server’s ACCEPT or REJECT permission response. The accounting procedure monitors user activity during the session.
Implementation
AAA commands, like aaa new-model, must be used to enable the security services in order to implement TACACS+. The IP address of the TACACS+ server and a shared secret key (password) that corresponds to the server configuration must be set up on the network device.
Defining a method list, which indicates the sequence in which authentication methods should be searched, is a standard setup technique. To ensure access in the event that the server is unavailable, the device could be set up to use a local database as a fallback method after initially using a TACACS+ server group.
Enterprise and carrier-grade devices typically support TACACS+. There are implementations for servers (such the Cisco Identity Services Engine and the FreeRADIUS TACACS+ module) and clients (like Cisco IOS, Junos OS, and Arista EOS). Administrators can map TACACS+-authenticated users to local user accounts or templates, which establish their authorization, and implement TACACS+ authentication and accounting, for example, using Junos OS.
Configuration and Fallback
When administrators use TACACS+ to set up remote authentication, they typically set up a local backup method:
Local Fallback: To make sure administrators may still log in in the event that the TACACS+ server is unavailable or down, it is crucial to include a backup local authentication mechanism (a fallback) when configuring remote AAA authentication. One way to achieve this is by using the phrase local in the setup command.
Enable Password Authentication: To make changing passwords on many Cisco devices easier, the enable? menu on a Cisco device displays options such as use-tacacs, which tells the router or switch to authenticate through a TACACS server. If no TACACS servers answer, an action can be defined using the last-resort option.
Example Configuration Command: aaa authentication login default group tacacs+ local is an example command that sets up AAA login authentication by first using a group of TACACS+ servers, with a fallback to local authentication.
Also Read About What Is UDP Flood Attack? How it Works & Why it is Important
TACACS+ vs RADIUS
| Feature | RADIUS (Remote Authentication Dial-In User Service) | TACACS+ (Terminal Access Controller Access-Control System Plus) |
| Primary Use | Network Access control (Wi-Fi, VPNs, 802.1x). | Device Administration control (Routers, Switches, Firewalls). |
| Standard | Open Standard (IETF RFCs). | Cisco Proprietary (though supported by other vendors). |
| Transport Protocol | UDP (User Datagram Protocol) | TCP (Transmission Control Protocol) |
| Port | UDP 1812 (Auth/Auth) and 1813 (Acct) or 1645/1646. | TCP 49. |
| Security/Encryption | Only the password is encrypted. Usernames and other attribute fields are sent in plaintext. | The entire packet payload is encrypted, offering higher security. |
| AAA Separation | Authentication and Authorization are generally combined. | Authentication, Authorization, and Accounting are separated into distinct processes. |
| Authorization Granularity | Less granular. Authorization is primarily based on user profiles or group access. | Highly granular. Supports per-command authorization, allowing administrators to control exactly which commands a user can execute. |
| Reliability | Less reliable due to UDP (requires retransmission logic built into the client). | More reliable due to TCP (connection-oriented, guaranteed delivery). |
| Vendor Support | Widespread (supported by virtually all network devices). | Primarily supported by Cisco and major enterprise network vendors. |
TACACS+ = Best for device administration with strong security and granular control, but mainly Cisco-focused.
RADIUS = Best for network access control (VPNs, wireless, etc.), widely supported, and more scalable.
Also Read About Cisco Switch BPDU Guard Configuration In Networking
