Protocol Based Intrusion Detection System
A security system called a Protocol Based Intrusion Detection System (PBIDS), sometimes known as a Protocol-Based IDS (PIDS), is made to track and examine how particular network protocols behave. Its objective is to identify abuse, irregularities, and attacks that deviate from the protocols’ set guidelines or anticipated usage patterns.
Also Read About What is RADIUS Components, Architecture and Applications
Core Focus and Mechanism
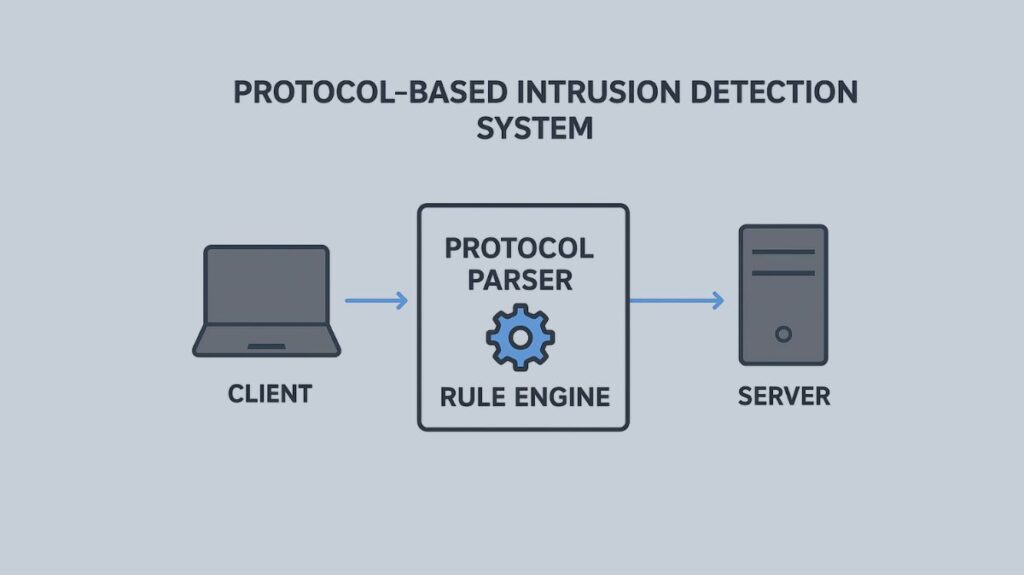
PBIDS functions by emphasizing protocol semantics rather than only raw packet headers or payload bytes. A PIDS’s main job is to make sure that every communication precisely follows the state and expected behavior of the protocol it is monitoring.
How PBIDS works (Functions and Flow):
- Parsing and Validation: The system uses protocol parsers to decode messages and extract commands, headers, fields, and sequences after receiving protocol traffic (often via span/mirror or inline). Following that, these fields and sequences are compared to pre-established procedure profiles and regulations.
- Enforcement: PBIDS makes sure that the proper DNS record formats or HTTP methods are utilized, for example, by enforcing the protocol’s language and semantics.
- Detection: A “Stateful Protocol Analysis” or a predetermined set of guidelines defining acceptable usage is maintained by the system. It combines two techniques for detection:
- Signature engine: Verifies policy infractions or known harmful patterns.
- Anomaly detector: Identifies deviations and learns typical protocol behavior.
- Action: The system can send events to automated defenders or security information and event management (SIEM) solutions, as well as generate warnings and logs if suspicious activity is detected. These protocol events may be connected between hosts and sessions via a correlation and context module.
Example: Web Server Protection
- Protecting a web server by keeping an eye on the HTTP or HTTPS stream is a typical application for a PIDS.
- The PIDS makes ensuring that the client and server communicate in accordance with the HTTP protocol’s guidelines.
- The PIDS is usually positioned in the “shim” (or interface) where the traffic is decrypted and just before it enters the web application layer if the connection is encrypted using HTTPS. This enables it to examine the material prior to it entering the protected system.
Deployment and Detection Capabilities
In order to examine the communication stream, a PIDS is usually set up as an agent or system that stands in front of a server, like a web server.
Important detection zones consist of:
- Identifying odd command sequences or noncompliant fields is known as protocol misuse.
- Malformed Requests: Identifying attacks that depend on a protocol being used maliciously or malformedly.
- Finding attempts to submit too much data in a field is known as a buffer overflow.
- Noncompliant Behavior: For instance, keeping an eye on HTTP streams to make that requests are formatted correctly and that only legitimate HTTP methods such as GET or POST are being used.
- Detecting malicious HTTP requests (like injection or route traversal), spotting questionable DNS activity (like tunneling or exfiltration), and protecting VoIP/SIP signaling are examples of common use cases. Bro/Zeek, Suricata, and ModSecurity are examples of tools that either incorporate or overlap with PBIDS capability.
Advantages and Drawbacks
Advantages:
- PBIDS offers high fidelity detection for threats that are particular to a given application or protocol.
- It can identify complex misuse that systems that only pay attention to packets (like NIDS) could overlook, including sequence-level logic attacks.
- It lessens false positives by comprehending the protocol context.
- Protocols with rich semantics, such as HTTP, SMTP, DNS, SIP, and database protocols, benefit greatly from it.
Also Read About What is HIDS Host Intrusion Detection System & HIDS vs NIDS
Drawbacks:
- Because extensive parsing and analysis need a lot of CPU and memory, processing overhead is an issue.
- The system needs current, comprehensive parsers for each protocol it monitors.
- One of the biggest problems with encryption is that encrypted protocol channels (TLS/HTTPS) need to be decrypted or have TLS terminated in order for the PBIDS to examine the material. The PIDS is usually positioned in the “shim” where traffic is encrypted right before it reaches the web application layer when a web server is protected via HTTPS.
- Due to the system’s restriction on monitored protocols, traffic utilizing unique or obscure protocols may be overlooked.
Typical use cases
- Identifying HTTP requests that are malformed (injection, path traversal).
- Recognizing questionable DNS behavior (tunneling, exfiltration).
- Keeping an eye out for spam and command abuse via SMTP.
- Protecting VoIP/SIP signaling (malformed headers, call hijacking).
- Defending database protocols against unusual queries or SQL misuse.
Also Read About Intrusion Detection System IDS Importance & IDS vs Firewall
