What is a WPA2 PSK key?

The popular wireless security setup known as WPA2-Personal, or WPA2-PSK (Pre-Shared Key), is mainly designed for home or small office networks (SOHO). Without the need for a specialized authentication server, this security option offers robust encryption and data protection.
Within the broader framework of the WPA2 (Wi-Fi Protected Access 2) security standard, WPA2-PSK is a particular authentication technique. When properly set, WPA2 is generally regarded as secure and offers more security than WPA.
The working principles, security features, and weaknesses of WPA2-Personal (PSK) wireless security are explained here.
You can also read AH Authentication Header In Network Security & How AH Works
How Does WPA2 PSK Work?
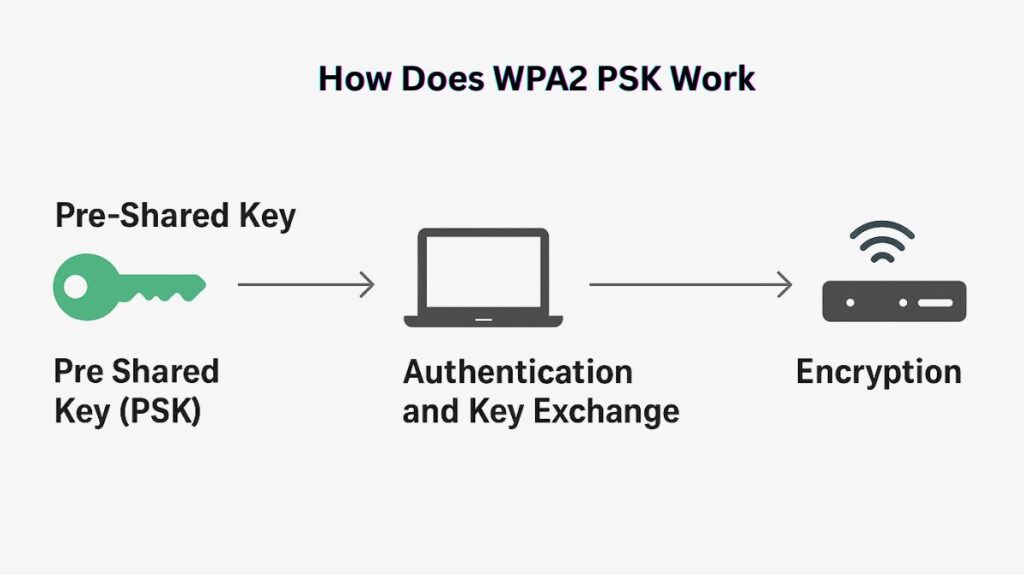
For key generation and authentication, WPA2-Personal uses a single, shared secret key called the Pre-Shared Key (PSK).
- The Pre-Shared Key (PSK): In essence, the PSK is a password or passphrase that the network administrator has set up on the wireless router or access point (AP). Before connections can be established, this key must be shared or set up in the same way on both the AP and each client device. When establishing a secure connection, the PSK serves as the basis.
- Authentication and Key Exchange: The four-way handshake is a procedure that the WPA2 protocol starts when a client device tries to connect.
- Without sending the PSK itself over the air, this handshake uses the PSK string to cryptographically demonstrate that the client and the AP are both aware of the proper password.
- The encryption key material is derived and exchanged using the PSK during the handshake.
- For that particular client’s connection, a distinct, transient session key, more precisely, a Pairwise Transient Key, or PTK, is created.
- Encryption: All information sent between the client and the access point is encrypted when the session key has been determined. This guarantees that unauthorized users cannot decode wireless traffic even if it is intercepted.
Key Security Features
WPA2 makes use of robust, contemporary encryption standards:
- Encryption Standard: Data encryption is accomplished via WPA2 using the Advanced Encryption Standard (AES) algorithm.
- Encryption Protocol: Counter Cypher Mode with Block Chaining Message Authentication Code Protocol (CCMP) is the encryption and integrity technique that is employed. AES-CCMP is regarded as an excellent and powerful technique that ensures data integrity and confidentiality. In particular, 128-bit AES-CCMP encryption is used by WPA2-Personal.
- No RADIUS Requirement: No Remote Authentication Dial-In User Service (RADIUS) server is needed for WPA2-Personal, which makes setting it up easier in small settings.
You can also read Applications Of MD5 Message Digest 5 Algorithm & Features
Security Limitations and Vulnerabilities
WPA2-Personal has some drawbacks even if it provides robust security when set up correctly:
- Reliance on Shared Key: The same PSK is used by every user connecting to the network. The entire network is at risk if this one PSK is compromised or extensively disseminated.
- Vulnerability to Dictionary Attacks: The PSK’s strength and complexity play a major role in network security. A malevolent user can intercept and record the information sent during the four-way handshake while using WPA2-Personal mode. Dictionary or brute force attacks can then be employed offline to automatically guess the PSK using this collected data.
- Known Protocol Flaws: WPA2 is vulnerable to more complex assaults, such as the Key Reinstallation Attack (KRACK), which takes advantage of flaws in the way the four-way handshake is implemented in the WPA2 protocol.
- Management Burden: Because all devices share the same key, updating or changing the PSK requires reconfiguring each device on the WLAN separately, which can be administratively taxing in settings with a large number of users.
Recommendations for Setup and Security
To optimize a WPA2-PSK network’s security:
- Strong Passphrase: A strong password should consist of a mix of capital and lowercase letters, digits, and special characters, and it should be at least 8 to 20 characters long (at least 16 is advised).
- Regular Updates: Keeping the router’s firmware updated and altering the PSK regularly reduces risk and guarantees that the most recent security fixes are applied.
- Disable WPS: Because Wi-Fi Protected Setup (WPS) poses a security concern, it is advised to disable it.
Because WPA2-Enterprise uses a central authentication server rather than a shared PSK and provides each user with unique credentials, it is typically advised for increased security in larger environments. By employing the Simultaneous Authentication of Equals (SAE) protocol, more recent protocols, such as WPA3-Personal, provide improved defense against offline dictionary attacks.
You can also read Dynamic Host Configuration Protocol and DHCP DORA Process
