Pay to Public Key Hash (P2PKH)
Bitcoin can be sent to an address using Pay-to-Public-Key-Hash, the most common network transaction method. Bitcoin is sent to a hash of the recipient’s public key in Pay to Public Key Hash transactions. After that, this hash serves as the Bitcoin address that most people view and utilize.
Core Concept
The recipient’s public key hash is used to lock funds in a P2PKH transaction. Both the owner’s public key and a digital signature generated by the matching private key are required in order to spend this money. Pay to Public Key Hash employs a shortened, hashed version of the public key instead of immediately embedding the complete one in the transaction output, which is a significant distinction from the previous Pay-to-Public-Key (P2PK) approach.
How P2PKH Transactions Work
The process of a Pay to Public Key Hash transaction involves several steps:
Key Generation and Hashing
- Initially, the recipient (e.g., Bob) must generate a private/public key pair. Bitcoin uses the Elliptic Curve Digital Signature Algorithm (ECDSA) with the secp256k1 curve for this.
- The public key is then cryptographically hashed using HASH160, which applies SHA-256 followed by RIPEMD-160. This hashing process shortens and obfuscates the public key.
Address Creation
- The public key hash is typically encoded as a Bitcoin address, which is a Base58Check-encoded string that includes an address version number, the hash, and an error-detection checksum.
- Pay to Public Key Hash addresses are easily recognizable as they always start with the digit ‘1’ on the main Bitcoin network.
You can also read Rollup in Blockchain, How it works, Types, And Applications
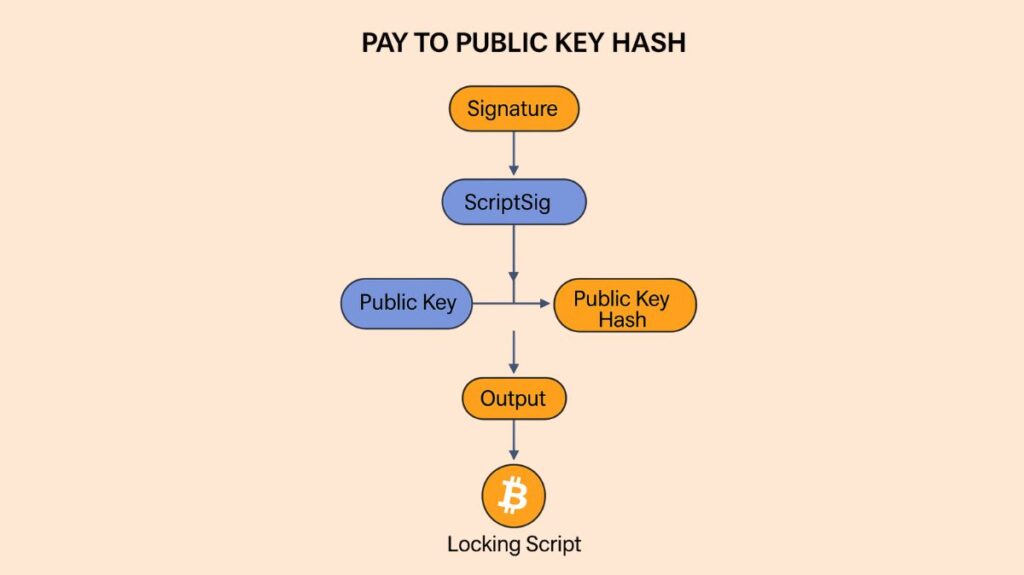
Creating the Output (Locking Script / scriptPubKey)
- When a sender (e.g., Alice) sends bitcoins to a Pay to Public Key Hash address, she creates a transaction output with a “locking script,” also known as scriptPubKey.
- This scriptPubKey contains specific opcodes that set the rules for spending the funds. The typical P2PKH scriptPubKey looks like this: OP_DUP OP_HASH160 <public_key_hash> OP_EQUALVERIFY OP_CHECKSIG
- Essentially, this script states that “to spend these funds, you must provide a public key that, when hashed, matches this public key hash, and you must also provide a valid signature created with the private key corresponding to that public key”.
Spending the Output (Unlocking Script / scriptSig)
- Once Alice’s transaction is broadcast and added to the blockchain, it becomes an Unspent Transaction Output (UTXO).
- When Bob decides to spend this UTXO, he creates a new transaction input that includes an “unlocking script,” known as scriptSig.
- This scriptSig provides two crucial pieces of data: a digital signature (created by Bob’s private key) and Bob’s full public key. The public key provided can be compressed (33 bytes) or uncompressed (65 bytes), but it must use the same format that was originally used to create the public key hash in the scriptPubKey.
Transaction Verification
When a network node validates a Pay to Public Key Hash transaction, it combines the scriptSig (from the input) and the scriptPubKey (from the output being spent) and executes the resulting script. The verification process is as follows:
- The scriptSig pushes the digital signature and the recipient’s public key onto the stack.
- The scriptPubKey then executes its opcodes:
- OP_DUP duplicates the public key on the stack.
- OP_HASH160 hashes the duplicated public key.
- <public_key_hash> (from the scriptPubKey) is pushed onto the stack.
- OP_EQUALVERIFY compares the newly generated hash of the public key with the hash included in the scriptPubKey. If they match, it proves that the provided public key corresponds to the address where the funds were sent.
- OP_CHECKSIG then verifies that the provided digital signature is valid for the public key. If both checks pass, the transaction is considered valid, and the funds can be spent.
You can also read What Is RACE Integrity Primitives Evaluation Message Digest
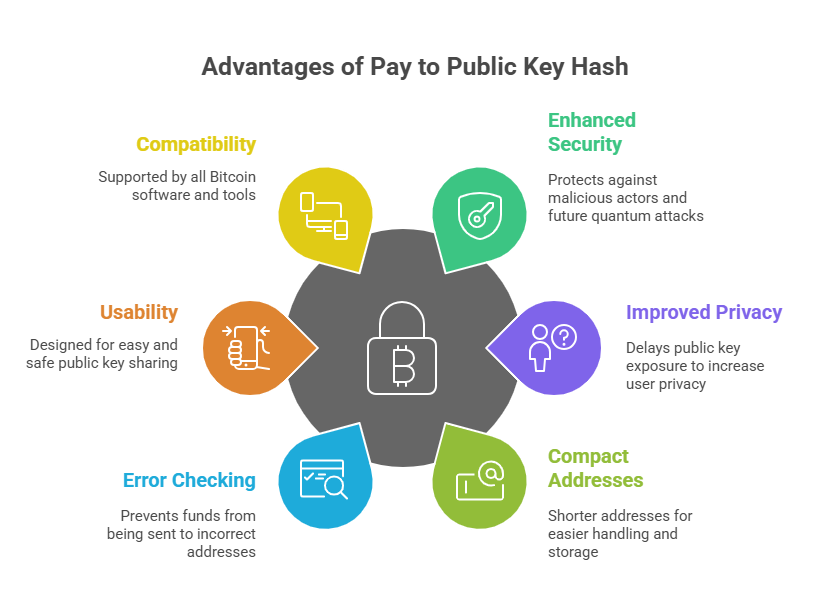
Advantages of Pay to Public Key Hash
Advantages of Pay to Public Key Hash
Pay to Public Key Hash became the standard for several compelling reasons, offering significant improvements over the earlier P2PK method:
- Enhanced Security: The full public key is not revealed on the blockchain until the funds are actually spent. This makes it more challenging for malicious actors to target the public key, particularly against theoretical attacks from future quantum computers, as the hash itself (secured by SHA-256 encryption) is difficult to break.
- Improved Privacy: By delaying the exposure of the public key, P2PKH helps to increase user privacy, making it harder to link transactions to a specific identity.
- Shorter and More Compact Addresses: Hashing the public key results in a much shorter address format (typically 34 characters), making them easier to print, transcribe manually, and embed into small storage mediums like QR codes.
- Built-in Error Checking: Bitcoin addresses, as a representation of a public key hash, include a checksum. This feature helps to prevent funds from being sent to mistyped or non-existent addresses, catching errors before they lead to lost funds.
- Usability: Satoshi Nakamoto’s design choice for P2PKH was largely driven by a desire to make it easier and safer for people to share their public keys.
- Widespread Compatibility: P2PKH is well supported by all Bitcoin software, wallets, and tools.
Disadvantages and Legacy Status
Despite being popular, Pay to Public Key Hash is regarded as a legacy script pattern. Since they are more efficient, newer transaction types like Pay-to-Witness-Public-Key-Hash (P2WPKH), which were first introduced with Segregated Witness (SegWit), are now frequently chosen. Transaction fees may be higher for P2PKH transactions since they typically have a greater transaction size than SegWit transactions.
Summary Table
| Feature | P2PKH |
|---|---|
| Funds locked to | Hash of the recipient’s public key |
| Address format | Starts with 1 in Bitcoin |
| Output script (scriptPubKey) | Uses OP_DUP OP_HASH160 … OP_CHECKSIG |
| Unlocking script (scriptSig) | Provides signature & public key |
| Advantages | More secure & private than P2PK |
| Use in Bitcoin | Most common in legacy transactions |
You can also read Pay To Script Hash Increases Security Of Bitcoin Transaction
