What is ARP spoofing Attack?
A common form of cyberattack is ARP spoofing, sometimes referred to as ARP cache poisoning or ARP poison routing, in which a malevolent actor transmits forged Address Resolution Protocol (ARP) packets across a Local Area Network (LAN).
The attack’s main objective is to trick networked devices into associating the attacker’s MAC address with the IP address of a genuine host, usually the router or default gateway. An attacker can effectively position himself for a Man-in-the-Middle (MITM) attacks by changing network routing through a successful ARP spoofing attack.
How the Attack Works (Attack Anatomy)
The attack takes advantage of the stateless, trust-based ARP protocol, which converts an IP address into a MAC address for a device connected to a local network.
ARP’s Normal Function:
- A device (Host A) requires Host B’s MAC address in order to communicate with another device (Host B) on the same network.
- Host A examines its ARP table or cache. “What is the MAC address for this IP address (Host B’s IP)?” is the question that Host A broadcasts in an ARP request if the MAC address cannot be located.
- In response, Host B provides an ARP response with its accurate MAC address.
- For later usage, Host A keeps this IP-to-MAC mapping in its cache.
The Spoofing Attack:
- Using a program (such as Ettercap or Arpspoof), the attacker, who is also on the local network, frequently sends fake ARP replies to Host A and the default gateway (router).
- The attacker replies to Host A with the assertion that “The MAC address for the Gateway’s IP address is the Attacker’s MAC address.”
- To the Gateway: The attacker responds with the assertion that “The Attacker’s MAC address is the MAC address for Host A’s IP address.”
- Both Host A and the Gateway update their ARP caches with the attacker’s fictitious information because ARP does not confirm the sender’s legitimacy.
Man-in-the-Middle:
- Now, Host A utilizes the Attacker’s MAC address to send data to the attacker when it sends data meant for the internet (via the Gateway).
- After intercepting, copying, or altering the data, the attacker’s computer sends it to the actual Gateway.
- The Attacker’s MAC address also receives the Gateway’s response intended for Host A, which enables the attacker to intercept and send the reply back to Host A.
- Now that they are in a silent position between the two parties, the attacker can intercept any unencrypted communication.
In order to evade detection, the attacker can then spy on the packets, alter the data before sending it to the real destination, or drop packets to initiate a denial-of-service attacks.
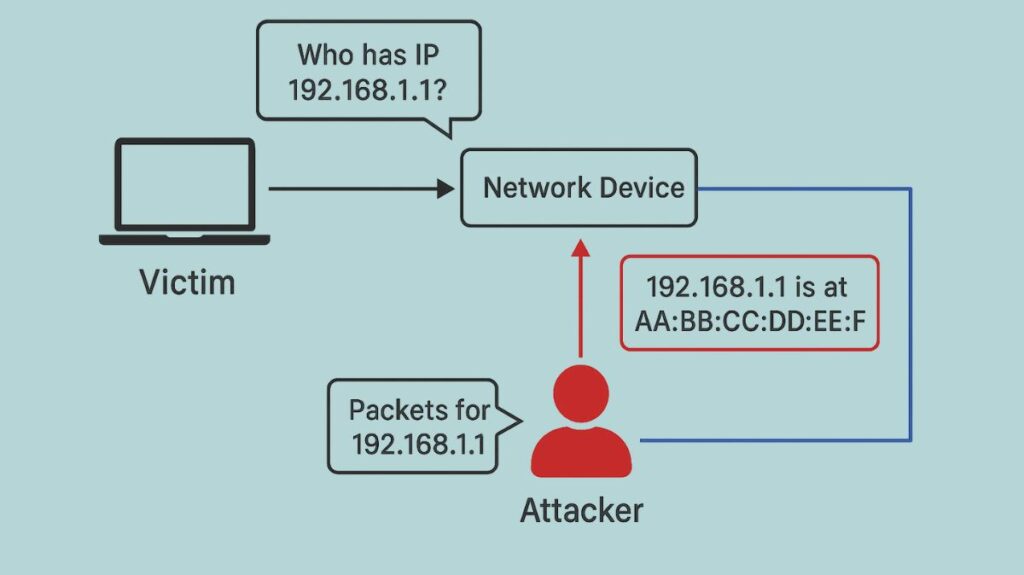
For example:
- “Who has IP 192.168.1.1?” a victim queries.
- A faked ARP reply stating that “192.168.1.1 is at AA:BB:CC:DD:EE:FF” (the attacker’s MAC) is the attacker’s response.
- The victim delivers upcoming packets for that IP to the attacker’s MAC after updating its ARP cache.
- While reading or altering packets, the attacker passes them to the actual device (to evade detection).
Also Read About What Are Spoofing Attack Types? How It Works, And Advantages
Purposes and Goals of ARP Spoofing Attacks
An essential initial step in enabling more complex cyberattacks is ARP spoofing:
Man-in-the-Middle (MITM): The attacker reads, intercepts, and frequently alters data as it is being transmitted. Particularly via unsecured networks, this is used to steal private data including login credentials, credit card numbers, passwords, and private correspondence.
Session Hijacking: To obtain unauthorised access to a user’s authenticated session, the attacker takes session IDs or tokens from intercepted traffic.
Data Modification/Malware Injection: Malicious code, such as viruses or malware, may be injected into the forwarded data stream if the attacker modifies the content of data packets while they are in transit.
Denial-of-Service (DoS): By delivering faked ARP answers, the attacker can either completely block all traffic between two hosts by not forwarding the intercepted packets, reroute traffic to unknown destinations, or overwhelm a single device with traffic (by mapping numerous IP addresses to its MAC address).
Detection and Prevention
Attacks using ARP spoofing are restricted to local network segments.
Detection Methods
Attack warning signs include:
- Identifying several distinct MAC addresses linked to the same IP address by looking through the ARP cache (arp -a).
- Internet connectivity failure that occurs suddenly or sporadically.
- unexpected messages about certificates when accessing HTTPS websites.
- ARP broadcast traffic volume that is unusual or fluctuates quickly.
How to prevent ARP spoofing attack
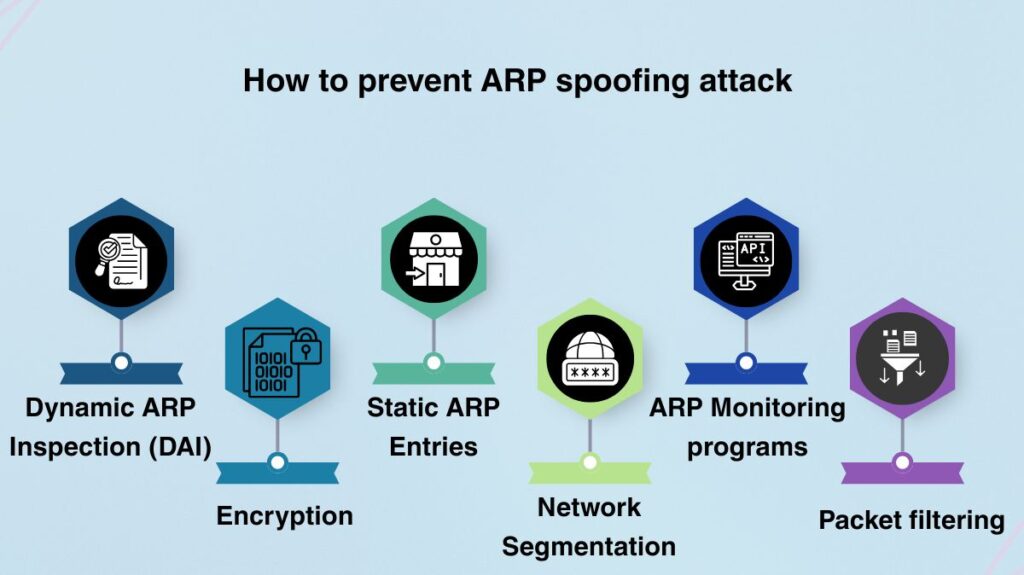
Both network setup and encryption are necessary for effective countermeasures:
Dynamic ARP Inspection (DAI): On business-grade switches, this works quite well. In order to prevent the attack from getting a foothold, DAI proactively removes invalid IP-to-MAC bindings and verifies ARP packets against a trusted database, which is frequently constructed using DHCP Snooping.
Encryption: Even if an attacker manages to get in the middle, any intercepted data is rendered useless when using encrypted communication protocols like Virtual Private Networks(VPNs), HTTPS/TLS, or SSH.
Static ARP Entries: Administrators have the option to manually add permanent IP-to-MAC entries to the ARP cache for crucial devices, such as servers or gateways. This keeps fraudulent responses from overwriting the cache, but it is time-consuming and unfeasible for big networks.
Network Segmentation: Since ARP messages cannot traverse Layer 3 boundaries, dividing big networks into smaller subnets (using VLANs) reduces the potential for an ARP spoofing attack.
ARP Monitoring programs: Administrators can be notified via host-based programs such as ARPwatch or XArp, which actively scan the ARP cache for unusual or often changing entries.
Packet filtering: Malicious ARP packets with contradicting source information can be prevented by using firewalls or filtering solutions, which can also be used to identify data packets coming from an address that appears twice in the network.
Also Read About Network Topology Types: Bus, Star, Mesh And More Topologies
