Learn what DoS and DDoS attacks are, how they crash services by exhausting resources, and the challenges of mitigating distributed attacks. Explore attack types, motivations and DoS Vs DDoS Attack.
Attacks that aim to interfere with the availability of network services, devices, or applications are known as denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks.
What is DoS Attacks
Denial-of-Service (DoS) attacks are designed to exhaust a system’s resources, resulting in the failure of services and systems or their inaccessibility to authorized users. In essence, it causes network services to stop working.
One of the more serious types of DoS attacks is a Distributed Denial-of-Service (DDoS) attack. The objective is the same, but it comes from several well-coordinated sources. Many infected machines, sometimes referred to as “bots,” are “distributed” in the attack, flooding or attacking the same target at the same time. An organization of these “zombie” hosts is called a “botnet,” and a threat actor uses a command-and-control (CnC) program to manage it.
You can also read User Security Awareness: Tips For Protecting Your Authority
How DoS Works
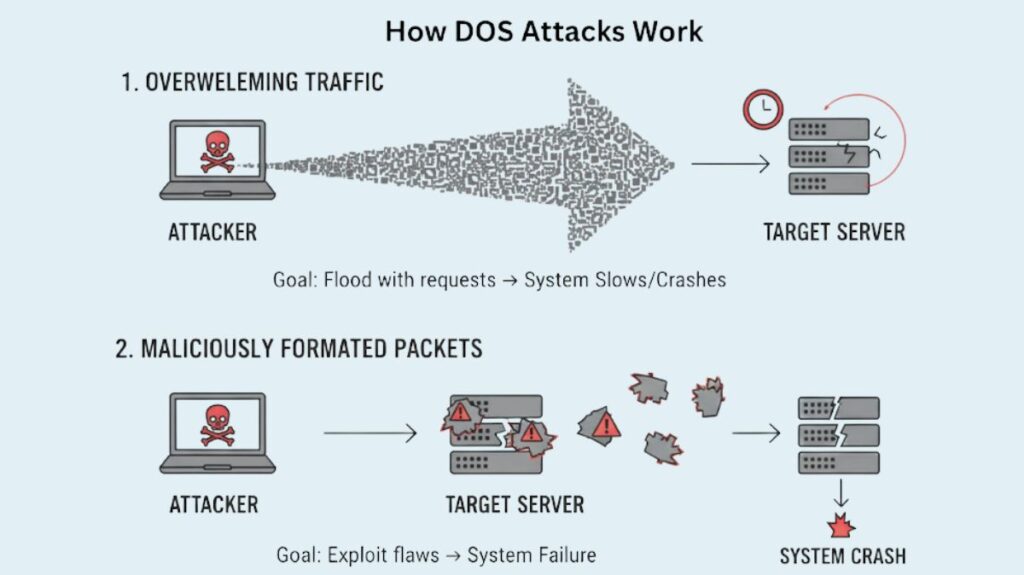
DoS attacks function primarily in two ways:
Overwhelming Quantity of Traffic: The threat actor transmits a massive amount of data at a speed that is too fast for the host, application, or network to process. As a result, response and transmission times are slowed, and a device or service may crash.
Maliciously Formatted Packets: The maliciously formatted packets are sent by the threat actor in a way that the host or application cannot properly process. As a result, the receiving device may crash or run very slowly.
DDoS attack
When a DDoS attack occurs, the scope is increased since the botnet concurrently targets the target with enormous volumes of traffic, making mitigation more challenging. An attacker could try to use thousands of new TCP connections per second to fill a web server’s connection table, for instance, which would be significantly higher than typical or heavy traffic rates. The unusual volume from a few clients to a particular server is usually detected by a stateful firewall as a denial-of-service attack.
Exploiting the TCP three-way handshake is a common DoS attack, especially TCP SYN flood attacks. The target receives constant TCP SYN session request packets from the attacker with a randomly spoof source IP address. After responding with TCP SYN-ACK packets to these fictitious or unreachable IP addresses, the target waits for an unsuccessful TCP ACK packet. Until the target’s connection queue is full, these “half-open” or “embryonic” connections use up system resources (such as memory and CPU) and prevent the target from reacting to valid connection requests.
You can also read Types Of Password Attacks And How Password Attacks Work?
Why it is Important
DoS and DDoS attacks must be understood and mitigated for a number of reasons.
Business Disruption: When legitimate users are denied access to vital network resources and services, denial of service (DoS) attacks can cripple a company’s ability to operate.
Costly Outages and Losses: Successful attacks can result in significant financial consequences, including expensive network outages, lost productivity, and the theft or damage of valuable assets or information.
Simplicity and Prevalence: DoS attacks are comparatively easy to carry out, even for a novice threat actor. They pose a frequent and enduring threat because of their simplicity of execution.
Resource Exhaustion: Because of these attacks, legitimate services become inaccessible as vital system resources like CPU, RAM, and network bandwidth are depleted.
Ubiquitous Vulnerabilities: Every networking protocol and function has ways for attackers to take advantage of features, leaving networks vulnerable all the time.
You can also read How To Prevent Password Attacks, Advantages & Disadvantages
Types of DoS and DDoS Attacks
The many varieties of DDoS and DoS attacks include:
Overwhelming Quantity of Traffic: Putting more data on a target than it can process.
Maliciously Formatted Packets: Transmission of specially constructed packets that slow down or crash the target.
TCP SYN Flood Attack: Makes use of the TCP three-way handshake by sending a flurry of SYN packets with faked source IP addresses. As the target waits for ACKs that never come, it uses up all of its resources.
UDP Flood Attack: Threat actors bombard known ports on a server with UDP packets, frequently from a spoof host. Using a lot of bandwidth, the server replies with ICMP port unreachable messages.
ICMP Attacks (“Ping of Death”): Involves altering IP header sections to cause system crashes or flooding a server with ICMP echo (ping) packets to overload it.
Chargen Attack: Causing severe network congestion by sending enormous volumes of UDP packets.
Packet Fragmentation and Reassembly Attack: Creates unreassembleable fragments to take advantage of buffer overrun bugs, which causes system crashes.
E-mail Bombs: Utilizing a lot of email service resources by sending a lot of emails.
Land.c Attack: System crashes occur when a TCP SYN packet is used with the target host’s address set as both the source and destination IP address, along with the same port.
Smurf Attack: An amplification attack in which a target’s spoof source IP address is used to send a lot of ICMP echo traffic to IP broadcast addresses, bombarding the target with replies and overloading its resources.
Reflection and Amplification Attacks: These DoS-related attacks deceive a “reflector” host into directing a significant amount of traffic towards the real target by using spoof source addresses. Specifically, amplification attacks use protocols or services on the reflector (such as DNS or NTP) to produce a lot more traffic than the attacker sent at first, using up a lot of network bandwidth.
DHCP Starvation Attack: The use of fake MAC addresses by an attack tool such as Gobbler to lease all available IP addresses within a DHCP scope is a specific DoS condition for connecting clients.
DAI as a DoS Target: The switch’s CPU usage may increase if an attacker generates a lot of ARP messages, making Dynamic ARP Inspection (DAI) vulnerable to DoS attacks.
You can also read Different Types Of MitM Attack, How It Work And Advantages
Advantages (from an Attacker’s Perspective)
Threat actors benefit from DoS and DDoS attacks in a number of ways.
Ease of Execution: Many DoS attacks are fairly easy to carry out, even for inexperienced users.
Disruption: They can essentially make it impossible for a company to operate by cutting off vital services.
Resource Exhaustion: A target’s system resources can be successfully exhausted by an attacker, causing services to malfunction or stop working.
Anonymity: Attackers can alter their identity by using spoof source IP addresses, which makes it more difficult to determine where the attack originated and may even frame innocent people.
Amplified Impact: A small amount of attacker traffic can produce a much larger volume of disruptive traffic against a target through reflection and amplification attacks.
Disadvantages (Risks from a Defender’s Perspective)
For defences against DoS and DDoS attacks, the repercussions are dire:
Service Unavailability: When legitimate users are excluded from network resources, apps, and services, operations come to a standstill.
System Slowdown or Crashes: Malicious packet formatting or excessive traffic can make devices and apps operate very slowly or crash completely.
Resource Depletion: In order to prevent the system from processing valid requests, attacks use up essential system resources like CPU, RAM, and TCP connection tables.
Bandwidth Consumption: The overall performance of the network may be impacted by the consumption of large amounts of bandwidth.
Difficulty in Mitigation (DDoS): Preventing and stopping attacks that come from multiple coordinated sources (DDoS) is extremely challenging.
No “Bulletproof” Solution: Despite the protections Cisco provides, it is currently impossible to totally stop DoS attacks without also blocking authorised users.
Security Device Failure Impact: The inline placement of an intrusion prevention system (IPS), which is used to mitigate DoS, could bring down the entire network if it fails.
You can also read What is Reconnaissance Attack, How it Works, History & Types
Applications (Mitigation Techniques)
Several tools and techniques are used by network security to thwart DoS and DDoS attacks:
Intrusion Prevention Systems (IPS): Placed in line with network traffic, these active security devices continuously search for unauthorized activity and recognized indicators of frequent attacks. They can even shut down possible threats and automatically stop attacks by logging, blocking, or rerouting malicious traffic. It is especially advised to use IPSs to prevent DoS attacks. Through the use of contextual data and zero-day threat monitoring, Next-Generation IPS (NGIPS) goes beyond this and may be able to identify worms through anomaly detection.
Firewalls: These devices use packet filtering, legitimate traffic identification, and malicious message discarding to enforce security policies at network boundaries.
- Stateful Firewalls: The ability to monitor the status of TCP conversations and detect and filter unusually high connection requests that may be signs of a DoS attack makes them essential for mitigating DoS attacks.
- Demilitarized Zone (DMZ): In order to mitigate various forms of attacks, it is recommended that public-facing servers, such as web servers, be placed in a DMZ that is firewall-segregated from the internal network. This prevents Internet users from directly accessing internal devices.
Access Control Lists (ACLs): When set up on routers, ACLs can control traffic flow, filter unwanted packets, and apply security policies. They can filter ICMP messages and counteract DoS SYN and DoS SYN attacks on TCP. They can also be used in conjunction with TCP Intercept and other features to defend servers against SYN-flood attacks.
DHCP Snooping: Protects against rogue DHCP servers and validates DHCP messages to prevent DHCP starvation attacks. In order to guard against DoS attacks on the switch CPU, DHCP snooping itself supports rate limitations.
Dynamic ARP Inspection (DAI): Examines ARP frames to stop attacks that might be a component of a larger DoS plan. In order to stop DoS attacks against the switch’s CPU, DAI also supports rate limits.
Disabling Unnecessary Services: Cisco IOS’s default services (echo, chargen, discard, BOOTP, MOP, IP Unreachables, Finger, and TCP/UDP small servers) are frequently superfluous and vulnerable to denial-of-service attacks. Attack vectors are decreased when these are disabled.
TCP Intercept: An exclusive Cisco IOS feature that guards against TCP SYN-flooding DoS attacks on TCP servers.
DoS Detection and Monitoring: Cisco IOS has tools for tracking and identifying denial-of-service attacks.
Logging and Audit Trails: Real-time alerts and audit logs are gathered and analyzed to help authorities track down attackers and conduct investigations. Attack details can be logged and alerts can be sent by IPS.
Unicast Reverse Path Verification (uRPF): By blocking packets attempting to enter the network with fake source IP addresses, it helps prevent DoS attacks.
You can also read Different Types Of Buffer Overflow Attacks And Advantages
More Details
Security Fundamentals: Identification of assets, remediation of vulnerabilities, and application of mitigation strategies prior to, during, and following an attack are all necessary for effective security. Exploiting a system’s vulnerability is the foundation of DoS attacks.
Accidental DoS: When legitimate users run network devices that are not configured correctly, DoS conditions can occasionally happen by accident.
Reconnaissance: To increase the focus and effectiveness of DoS attacks, reconnaissance attacks which obtain data about a target’s systems and vulnerabilities often come before them.
Continuous Evolution: With new threats and vulnerabilities appearing on a regular basis, security is “never completely done” because the landscape is always evolving. This dynamic environment is addressed by Cisco’s Talos Intelligence Group, which actively investigates global security issues.
DoS Vs DDoS Attack
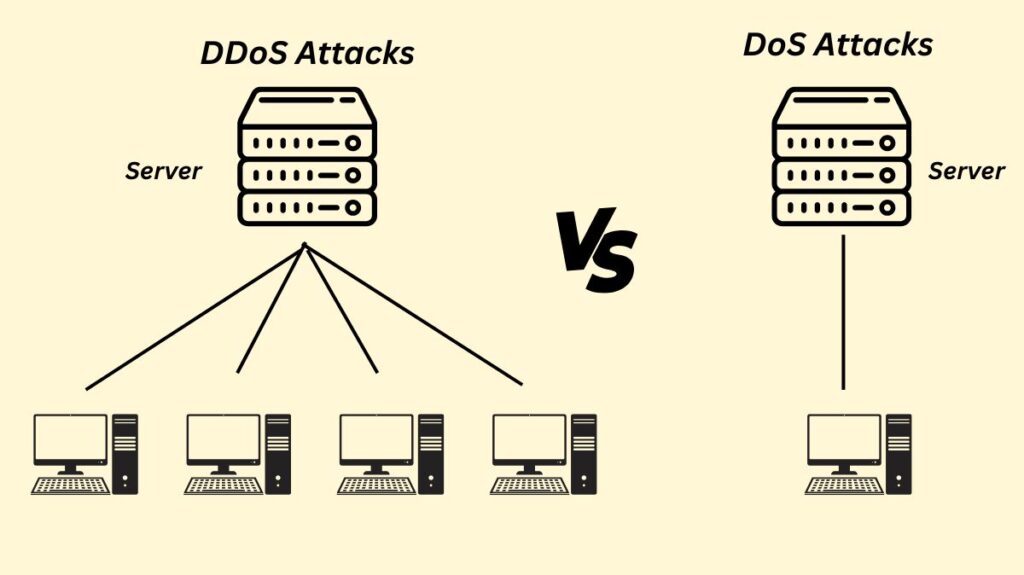
| Feature | Denial-of-Service (DoS) Attack | Distributed Denial-of-Service (DDoS) Attack |
| Attack Source | A single computer or network connection. | Multiple, compromised devices (a botnet) controlled by a single attacker. |
| Attack Volume | Generates a lower volume of traffic, as it is limited by the single source’s bandwidth. | Capable of generating a much larger, overwhelming volume of traffic due to the number of attacking machines. |
| Detection & Mitigation | Easier to detect and block. An administrator can identify the single malicious IP address and block it using a firewall. | Much harder to detect and mitigate. The attack traffic comes from many different, legitimate-looking sources, making it difficult to distinguish from normal user traffic. |
| Complexity | Generally less complex to execute, often using simple scripts or tools. | More complex to orchestrate, requiring the creation and control of a botnet. |
| Execution Method | The attacker directly uses their own machine to flood the target. | The attacker uses a command-and-control (C&C) server to remotely command the botnet (zombies) to attack the target. |
You can also read Advanced Phishing Techniques, Prevention And Mitigation
