In this article, we learn about what is Data Encryption Standard DES, its Key Characteristics, how Data Encryption Standard Works, Security, and Configuration Context
What is Data Encryption Standard DES?
The National Institute of Standards and Technology (NIST) released the Data Encryption Standard (DES), a groundbreaking and historic symmetric-key block cipher. From 1977 to 2002, it was the official Federal Information Processing Standard (FIPS) for the United States for encrypting unclassified, sensitive electronic government data.
Key Characteristics and Structure
The technical specifications listed below define DES:
- Algorithm Type: DES is a symmetric algorithm, which means that it encrypts and decrypts data using the same key.
- Cipher Type: This cryptographic block cipher works with 64-bit data blocks of fixed size.
- Key Length: Eight of the 64 bits are used only as check bits (parity bits) and are deleted during key transformation; therefore, although the nominal key length is 64 bits, the effective key length is 56 bits.
- Core Structure: DES uses a 16-round Feistel structure and is an implementation of a Feistel cipher.
You can also read What is Challenge Handshake Authentication Protocol CHAP
How Data Encryption Standard Works?
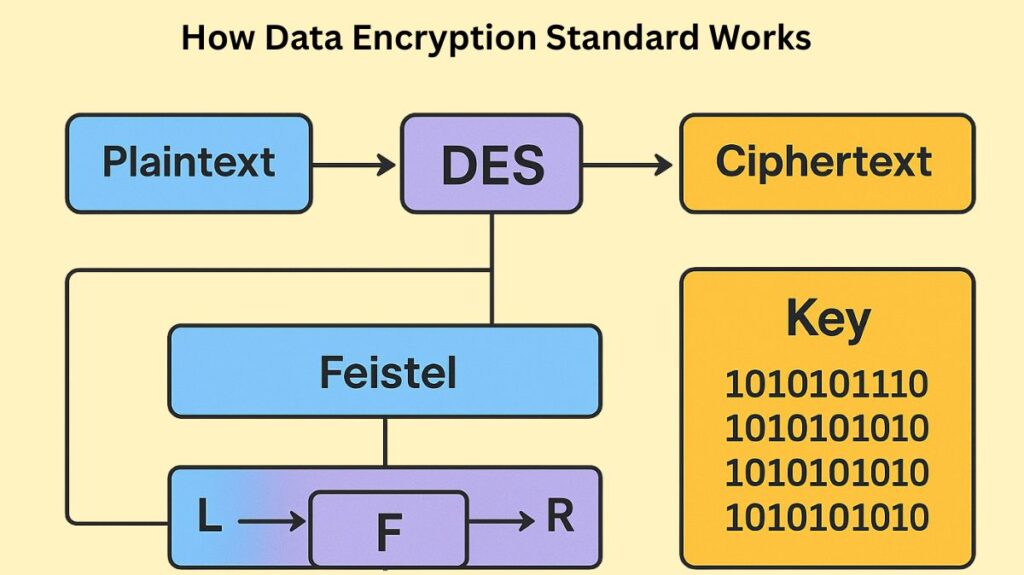
An initial permutation, sixteen processing rounds, and a final permutation are all part of the DES encryption process.
Initial and Final Permutations
A 64-bit block of plaintext is first encrypted by rearranging the bit order using an Initial Permutation (IP) function. The final 64-bit ciphertext is produced via an Inverse Initial Permutation (FP), which is the inverse of the IP. Although they were included to make data loading easier on earlier hardware, the IP and FP are inverses of one another and are straight Permutation boxes (P-boxes) with no cryptographic significance.
The 16 Feistel Rounds
The 64-bit permuted plaintext is separated into a 32-bit Left Plaintext (LPT) and a 32-bit Right Plaintext (RPT) following the Initial Permutation. Over 16 identical rounds, these portions are treated alternately.
In each round (i), the process involves:
- The Left Half for the next round (Li) is simply the Right Half of the current round (Ri-1).
- The Right Half for the next round (Ri) is determined by XORing the current Left Half (Li-1) with the output of the Mangler (F) function operating on the current Right Half (Ri-1) and the round subkey (Ki).
The Feistel (F) Function
The core of the cypher is the F-function, which generates a 32-bit output by applying a 48-bit key to the rightmost 32 bits. There are four primary stages to it:
- Expansion Permutation: An expansion permutation (E-box) is used to increase the 32-bit input (right half) to 48 bits.
- Key Mixing: An XOR (⊕) operation is used to combine the 48-bit block that results with the 48-bit round subkey.
- Substitution (S-boxes): Eight 6-bit pieces of the 48-bit output are separated and fed into a matching Substitution Box (S-box). Every S-box substitutes a 4-bit output for its 6-bit input using a non-linear transformation. For DES security, the core mixing (confusion) is provided by the S-boxes.
- Permutation: A fixed Straight Permutation (P-box) is used to rearrange the aggregate 32-bit output from the S-boxes. This stage aids in the dispersion of the bit dependency.
Key Generation (Key Schedule)
The key schedule generates sixteen unique 48-bit round subkeys (Ki) from the 56-bit effective cipher key:
- By discarding the eight parity bits, Permuted Choice 1 (PC-1) reduces the original 64-bit key to 56 bits.
- Two 28-bit halves are created from the 56 bits.
- These halves are subjected to a circular left shift operation (1 or 2 bits, depending on the round number) for every round.
- The shifted 56 bits are combined and then subjected to Permutation Choice 2 (PC-2), which selects and rearranges 48 bits to form the round subkey (Ki) used in that round’s F-function.
Decryption
The algorithm structure used for encryption and decryption in DES is identical; however, the subkeys are applied in reverse order (from K16 down to K1).
You can also read What is Encapsulating Security Payload and How ESP Works
Security and Replacement
Due to its ability to satisfy criteria like completeness and the avalanche effect, DES had a significant impact on the advancement of cryptography. It is a deprecated cryptographic block cypher, nevertheless, and is currently regarded as seriously vulnerable.
Its small 56-bit key length is the main weakness, leaving it open to brute-force assaults (testing every conceivable key). By 1999, specialized hardware like the DES cracker developed by the Electronic Frontier Foundation (EFF) showed that a DES key could be cracked in less than a day.
Because of this flaw, more robust algorithms have taken the place of DES:
- Triple DES (3DES): To improve security, this form uses two or three different keys (effectively 112 or 168 bits of key strength) to run the DES algorithm three times. TDES for sensitive government data has been authorized by NIST till 2030.
- Advanced Encryption Standard (AES): The current global standard, Advanced Encryption Standard (AES), is exponentially more efficient than 3DES and resistant to brute-force attacks because it offers far bigger key lengths (128, 192, or 256 bits) and a larger block size (128 bits).
Configuration Context
For specific security features in Cisco environments, the encryption algorithms DES and 3DES can be specified:
- SNMP Users: To configure users employing the security level of
priv(privacy) in SNMP, the following parameters can be added to the end of thesnmp-server usercommand syntax:- To enable DES encryption: use the
priv des encryption-keyparameters. - To enable 3DES encryption: use the
priv 3des encryption-keyparameters.
- To enable DES encryption: use the
- DH Key Exchange: Symmetric keys produced during the DH exchange are compatible with symmetrical algorithms like Triple Digital Encryption Standard (3DES).
You can also read Dynamic Host Configuration Protocol and DHCP DORA Process
