Stateful Inspection Firewalls
A Stateful Inspection Firewall, sometimes referred to as a Dynamic Packet-Filtering Firewall, is a more sophisticated kind of network firewall that provides more protection than more straightforward packet-filtering firewalls. In order to make wise security judgements its main job is to keep an eye on and record the status of all current network connections.
You can also read How Does A RADIUS Server Work, Architecture And Functions
How Stateful Inspection Firewall Works
Maintaining “state” and “context” for network connections is the fundamental function of a stateful firewall.
State Table:
Every connection that has been allowed to flow through the firewall is tracked in detail by the firewall’s dynamic state table, also known as a stateful database. Details like these are stored in this table:
- IP addresses for the source and the destination.
- numbers of the source and destination ports.
- protocol, such as TCP, UDP, or ICMP.
- LISTEN, ESTABLISHED, CLOSING, establishing, established, and closing are examples of the connection’s current states.
- numerical sequences.
Connection Awareness and Tracking:
- The firewall checks a new connection when it is established (for example, a TCP SYN packet in a three-way handshake). In the event that the packet satisfies a pre-established security rule, the firewall adds the connection to its state table.
- The connection’s whole lifecycle is then tracked, with entries added when a connection is established and removed when it is closed or, in the event that no activity is detected, after a predetermined timeout.
- This ongoing oversight also covers connection termination, guaranteeing that closures are valid.
Contextual Decisions and Dynamic Filtering:
- The context of the traffic is taken into account by a stateful firewall as opposed to stateless firewalls, which check each packet against every rule separately.
- The firewall checks entries in its status table for subsequent packets that come as part of an active session.
- Allowed Traffic: A packet is allowed to pass if it corresponds to a known, valid connection in the status table (for example, a reply to an outgoing request that was previously approved). Comparing this to reevaluating rules for each packet is significantly faster.
- Denied Traffic: A packet is banned if it doesn’t match any entries in the status table or if it behaves suspiciously. An external attacker that sends random packets without a matching session, for example, will be blocked.
Packet Inspection
Stateful firewalls look for data threats or unauthorized activity by examining and analyzing data packets. To ascertain whether a packet is a fresh request or a continuation of an already-existing discussion, they examine its header. Some technologies, such as Barracuda’s CloudGen firewall, examine the header and contents of network traffic in order to do deep packet inspection.
Protocol Handling:
- TCP (Transmission Control Protocol): As a connection-oriented protocol, Transmission Control Protocol (TCP) offers comprehensive state information, including SYN, ACK, and FIN flags. Throughout the TCP handshake and session, the firewall records this information.
- UDP (User Datagram Protocol): User Datagram Protocol, or UDP, is connectionless and has a lower amount of state information built in. To implement “pseudo-stateful” protection, stateful firewalls can nonetheless make use of contextual data regarding ports, IP addresses, and device profiles. Usually, a set timeout is used to delete UDP sessions from the state table.
- ICMP (Internet Control Message Protocol): Network control information is transmitted by ICMP (Internet Control Message Protocol) messages, and stateful firewalls permit ICMP replies to pass through.
- FTP (File Transfer Protocol): FTP prevents unauthorized data transfers by using a stateful firewall that monitors the command connection to confirm the request and only permits the data connection when requested.
Key Features
Works at Multiple Layers: The majority of network activity and data packet exchanges take place at the Network Layer (Layer 3) and Transport Layer (Layer 4) of the OSI model. It keeps track of the sessions’ status as well.
Policy Implementation and Enforcement: Enforcing and implementing security and privacy standards for the network as a whole, including user behaviour and access, is possible.
Intelligent Defence: In contrast to static firewalls, stateful inspection firewalls are able to apply traffic settings for both inbound and outbound traffic and use defence mechanisms driven by AI and machine learning.
Traffic Filtering: Through intelligent, thorough packet inspection, traffic filtering defends against malware, brute force attacks, and denial-of-service attacks.
Network Monitoring: Network monitoring can be integrated with application-monitoring technologies to prevent data breaches and backdoor attacks. It also keeps an eye on direct communications.
Communication Protocol Management: Regulates which communication protocols are permitted on the network and gathers data about the protocols being used for privacy and security.
Efficient Traffic Processing: Utilizes memory and processing power for logging and malicious attempt tracking, allowing it to manage large volumes of network traffic without compromising security.
Advantages of Stateful Inspection Firewall
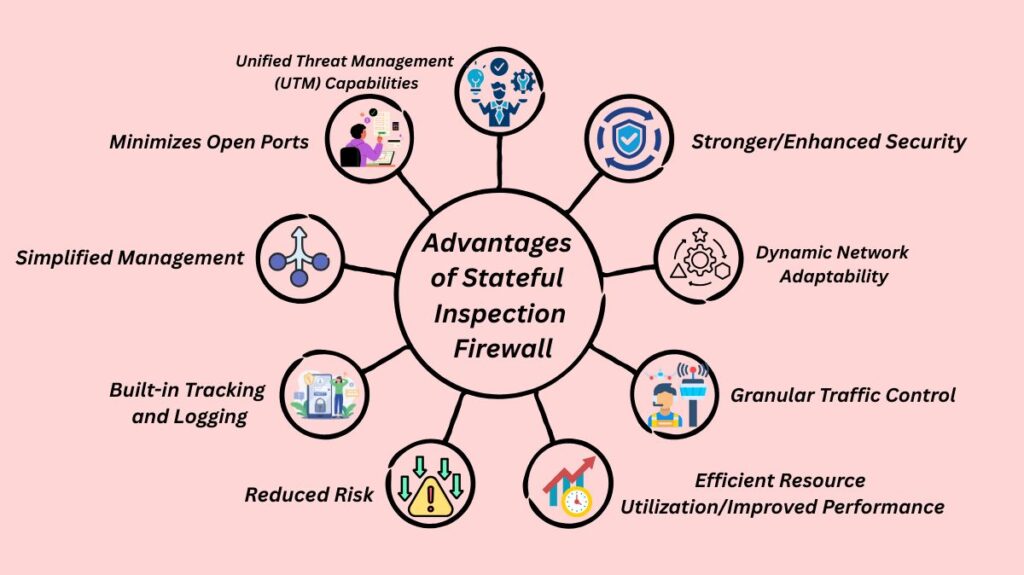
Stronger/Enhanced Security: By understanding context and blocking unauthorized traffic that stateless firewalls would overlook, this protection surpasses that of simple packet filtering. IP spoofing, session hijacking, and some Denial-of-Service (DoS) assaults are among the sophisticated threats that it can identify and stop.
Dynamic Network Adaptability: This responsive security feature modifies filtering tactics in real-time as connections are created, used, and broken.
Granular Traffic Control: Enables sophisticated security measures by enabling administrators to specify exact policies according to context (connection status, application type, and user identification).
Efficient Resource Utilization/Improved Performance: Minimizes processing overhead and increases throughput by eliminating the need for frequent re-evaluation of data packets for connections that have already been established. State table lookup speeds up the processing of the following packets after the initial connection.
Reduced Risk: Guarantees that only legitimate connections are sent through.
Built-in Tracking and Logging: With built-in tracking and logging, you can keep track of network activities and attacks, which is helpful for cyber forensics and in-software learning to stop similar attempts in the future.
Simplified Management: Complex, explicit rules for every response packet are not necessary because return traffic for established connections is automatically permitted.
Minimizes Open Ports: To permit traffic to enter or exit, fewer ports need to be opened.
Unified Threat Management (UTM) Capabilities: capable of learning as it goes, which makes it an effective UTM solution.
You can also read NTP Server Configuration And How Does NTP Server Work?
Limitations and Disadvantages of Stateful Inspection Firewall
Resource Intensive: Requires more memory and processing resources than stateless firewalls because of the state table maintenance.
Configuration Complexity: Requiring a thorough understanding of security policies and network protocols, configuration can be difficult, particularly for big networks. Misconfiguration may result in interruptions or vulnerabilities.
Limited Application Layer Defence: Not all application layer attacks may be stopped, and unlike next-generation firewalls, they are still unable to examine deep application data. Additional solutions, like as intrusion prevention systems or application layer firewalls, may be required to close this gap.
Vulnerability to State-Table Attacks: By flooding the firewall with connection requests, malicious actors may try to overrun it and trigger a denial of service (DoS) attack.
Absence of User Authentication: This usually means that users behind the traffic are not authenticated, which means that extra authentication methods are needed to confirm the identity of the users.
Susceptibility to MITM Attacks: This vulnerability may make it more vulnerable to MITM attacks.
Protocol Limitations: Does not support every kind of communication protocol. Certain protocols, such as ICMP and UDP, are more difficult for purely stateful inspection because they lack strictly regulated state information.
Connection-based Limitation: Based on connections, Limitation: Since they rely on connections, they can’t keep an eye on or disrupt network activity that doesn’t take place through approved routes.
Obsolete Without Updates: Without regular software upgrades, it may become outdated.
Cost: Because of its complexity and resource needs, it is typically more expensive than other firewall choices.
Unexpected Disconnects: Half-open TCP connections or unexpected disconnects may result from connections that are inactive for longer than the timeout.
Stateful Vs Stateless Firewall
The primary distinction lies in their approach to traffic management and security.
| Feature | Stateful Firewalls | Stateless Firewalls |
| Connection Tracking | Track ongoing connections and maintain a state table for every communication channel, from initiation through its lifecycle. They remember previous interactions. | Inspect packets individually and have no memory of past traffic or context. |
| Context Awareness | Understand the context of ongoing connections and traffic flow. They analyse the behaviour and characteristics of data packets. | Rely on a set of predefined rules (Access Control Lists – ACLs). They classify traffic based on surface information like packet headers. |
| Filtering Basis | Filter based on pre-established rules and the ongoing connection state. They compare packets against entries in their state table. | Filter solely based on header information (e.g., source/destination IP, port, protocol). Each packet is evaluated in isolation. |
| Security Level | Enhanced security; detect patterns for security and prevent complex threats like IP spoofing, TCP session hijacking, and certain DoS attacks that stateless firewalls miss. | Potentially less secure; block by basic criteria and offer general access control. |
| Performance | After initial connection, subsequent packets are quickly processed via state table lookup, leading to improved performance. However, maintaining the state table is resource-intensive. | Generally less resource-intensive and perform well with high traffic volumes due to basic processes. |
| Complexity & Cost | More complex configuration and generally more expensive. | Simpler, more cost-effective, and easier to set up for basic needs. |
| Ideal Use Case | Complex, dynamic network environments where tracking connection context enhances security (e.g., large enterprises). | Simpler, less dynamic setups with basic security needs, limited resources, or where speed is critical (e.g., individual users, small businesses, or basic network filtering). |
| Vulnerabilities | Can be vulnerable to DDoS or other attacks involving floods of malicious data that overwhelm the state table. | Less vulnerable to DDoS attacks in some aspects due to not maintaining state. |
Utilizing Stateful Firewalls
Security Zones: Stateful firewalls frequently function using the idea of security zones, such as inside, outside, and Demilitarized Zones (DMZs). The hosts that can establish connections between these zones are governed by rules. An elementary rule might, for example, automatically prohibit external users from connecting to internal hosts while permitting internal users to connect to an outside zone for preset safe ports.
Adaptive Security Appliance (ASA): Stateful filtering is used in Cisco implementations, including the Adaptive Security Appliance (ASA) and Firepower product lines. For instance, by default, the ASA allows higher-security interfaces (like the inside network at level 100) to initiate traffic to lower-security interfaces (like the outside network at level 0). The stateful inspection dynamically allows the return traffic.
Next-Generation Firewalls (NGFWs): An Evolution Although stateful inspection is a conventional firewall function, Next-Generation Firewalls (NGFWs) expand on it by incorporating more sophisticated functionalities. To identify programs and stop sophisticated attacks, they include Advanced Malware Protection (AMP), Application Visibility and Control (AVC), and URL filtering. they techniques carry out further analysis beyond Layer 3/4 headers, occasionally even up to Layer 7.
Cisco IOS: Cisco IOS routers have the ability to perform stateful filtering as well. Context-Based Access Control (CBAC) and other older technologies were early attempts at stateful filtering on IOS, but the more modern Zone-Based Firewalls (ZBFs) have now entirely supplanted them. For stateful filtering and application inspection on IOS routers, ZBFs are the suggested approach.
You can also read Key Difference Between Physical Server And Virtual Server
