This article gives an overview of Endpoint in Networking, How it work’s, types, Advantages, Disadvantages and Importance Of Endpoint Security.
What is an Endpoint in Networking?
Any host or connected device is referred to as an endpoint in networking. It basically refers to any hardware or software that acts as a communication or access point for network resources. Destination of data communication, endpoints are the “ends” of a network connection. The network can locate and communicate with them because they are uniquely identified by an address, like a MAC or IP address.
How Network Endpoints Work
The devices that send, receive, and process data at a network’s edge are known as network endpoints. They are either the first or last places where data is transferred. Any device that communicates with a network, such as a computer, smartphone, server, printer, or other gadget, can be considered a network endpoint.
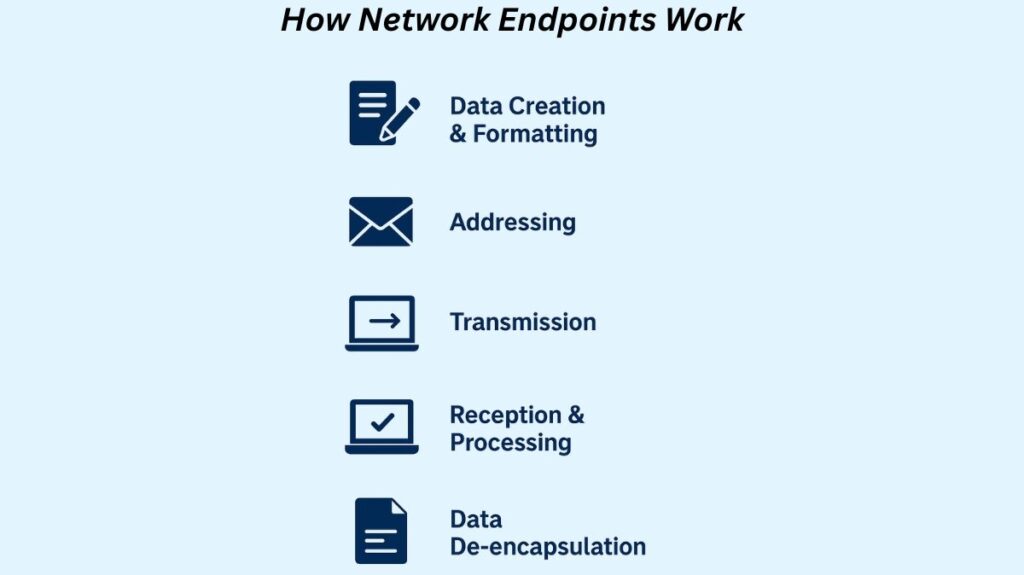
An endpoint’s functionality can be divided into several essential processes that are managed by the Network Interface Card (NIC) or a comparable device.
Data Creation & Formatting: On the endpoint, data is created by a user or application (e.g., entering a message, opening a web page). Following formatting, this data is divided into distinct units known as packets.
Addressing: The operating system and network stack of the endpoint append header information to the packet, which includes the recipient’s destination address and the packet’s own unique source address (such as an IP address and MAC address).
Transmission: After the packet has been formed, it is sent to the NIC, which transforms the digital data into a format that can be sent over the physical medium, like radio waves for Wi-Fi or electrical impulses for Ethernet connections.
Reception & Processing: The NIC gets the signal when a packet is transferred to the endpoint and transforms it back into a digital representation. The packet’s intended destination address is then verified by the operating system’s network stack.
Data De-encapsulation: The several levels of header information included during transmission are removed by the endpoint as the packet ascends the network stack. The original data is put back together and sent to the proper program, like an email client or web browser, after the last header has been deleted. The endpoint may send and receive data thanks to this entire procedure, which makes it the point of entry and exit for network communication.
Characteristics of Endpoints
Connection Point: Devices known as endpoints are those that join a network to allow data transmission and reception. Either a wired or wireless connection is possible.
Data Exchange: Through the establishment of communication sessions, processing of data requests, and information transmission, they enable communication between various devices or applications throughout the network.
Unique Identification: An IP address or MAC address is a common way for each endpoint to be uniquely identified, which enables other devices to find and connect to it.
User Interface: Endpoints are frequently end-user devices that serve as the internet’s and computer networks’ user interfaces.
Types of Endpoints
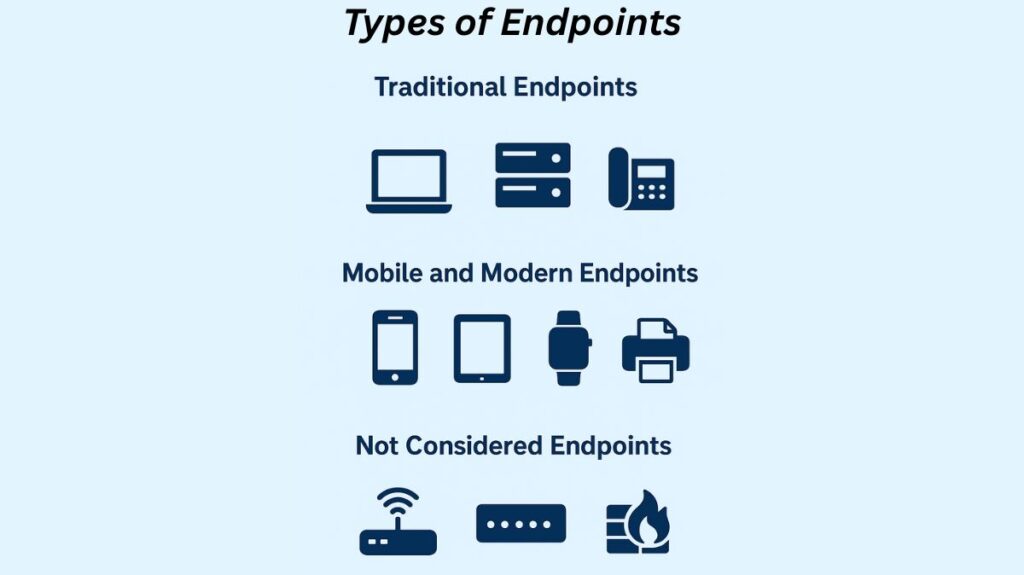
Endpoints currently include a vast range of devices due to their tremendous evolution.
Traditional Endpoints: These consist of well-known instances such as:
- Desktop and laptop computers.
- Servers, such as file servers, database servers, and web servers, can act as the main endpoints for client devices.
- IP phones.
Mobile and Modern Endpoints: This category has expanded quickly and now consists of:
- Smartphones and tablets that connect through cellular data or Wi-Fi.
- Smartwatches.
- Printers.
- Conventional servers running directly on hardware, virtual machines (VMs), or containers, particularly in the context of Cisco’s Application Centric Infrastructure (ACI).
- Cloud services and cloud instances.
- Smart thermostats, industrial sensors, wearable technology, smart home appliances, smart badge readers, and even electrical power meters that use mobile phone technology for invoicing are examples of Internet of Things (IoT) products.
- Retailers employ point-of-sale (POS) devices.
- Diagnostic tools and networked monitoring are examples of medical devices.
- Electronic video screens for advertisements.
Not Considered Endpoints: Routers, switches, and firewalls are examples of network infrastructure devices that are usually not regarded as endpoints because they serve as middlemen that facilitate data transmission. If a router, switch, or gateway connects to other endpoints and network resources, it can be regarded as an endpoint. In some cases, edge routers in a LAN or wireless network access points are also referred to as endpoints.
Role and Function: Endpoints are the devices used by end users to connect to the network. They make it possible for users to do almost whatever they need to do on a daily basis that involves network connectivity. In order to guarantee that information packets reach their intended locations, endpoints are in charge of preserving the efficiency and integrity of data flow. Policies specify the communication between the “endpoint groups,” which are groups of endpoints in an ACI operating architecture.
Advantages of Network Endpoints
Access to Network Resources: Endpoints are the locations where users can connect to a network and its resources, including the internet, shared files, and printers.
Decentralized Processing: Instead of depending on a single central server, they allow distributed computing, in which processing work can be divided across several devices. Overall system resilience and efficiency are increased as a result.
Scalability: The network can readily expand to handle more users and devices because adding new endpoints is comparatively easy.
User Customization: Through endpoints, individual users can tailor their computing environment, settings, and apps to suit their unique requirements and tasks.
Disadvantages of Network Endpoints
Security Vulnerabilities: Potential entry points for security risks including malware, viruses, and illegal access are present on every endpoint. It is incredibly difficult to secure every single device on a network.
Management Complexity: Large endpoint management and upkeep can be difficult and time-consuming. Deploying software updates, installing security patches, and resolving problems on a variety of devices are all included in this.
Performance Issues: The entire performance of the network can be harmed by an infected or poorly functioning endpoint. A device that has malware or a high-traffic application, for instance, may use excessive bandwidth.
Data Loss Risk: If data is not adequately backed up to a network-attached storage or cloud service, it may be lost due to theft, damage, or hardware failure on an endpoint.
Network Topology and Connections
- Endpoints in a spine-leaf network topology, which is typical in data centers, only ever connect to leaf switches.
- Each host (endpoint) in an Ethernet LAN with a star topology connects via a separate cable to a hub, switch, or router.
- Endpoint devices, including two-tier and three-tier topologies, are important when talking about LAN design.
- Access Points (APs) and Wireless LAN Controllers (WLCs) are regarded as endpoints for wireless LAN components in terms of physical infrastructure connectivity.
- Usually, hosts (endpoints) are aware of the IP addresses of a minimum of two DNS servers in order to provide redundancy in name resolution requests.
Importance of Endpoint Security
Because endpoints act as points of entrance and departure for data, they are frequently the focus of cyberattacks. Threat actors may use a hacked endpoint to obtain sensitive data and important system devices, thereby jeopardising the network as a whole. The growing number of connected devices, remote work arrangements, and Bring Your Own Device (BYOD) rules all increase this risk by dismantling traditional network perimeters and increasing the attack surface.
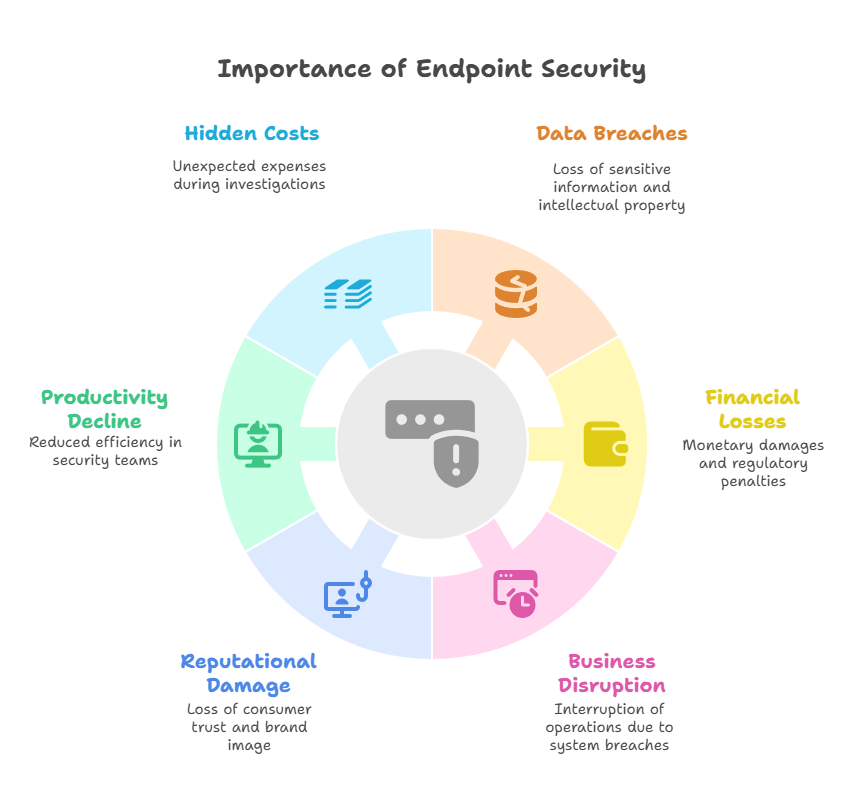
Endpoint security flaws may result in:
- Data breaches include private company information, consumer information, and intellectual property.
- Monetary losses as well as infractions of regulations.
- Interruption of corporate activities as a result of system breaches and ransomware attacks.
- Reputational harm and a decline in consumer confidence.
- Decreases in security teams’ productivity.
- Expenditures that are not disclosed during forensic investigations and incident response.
Security Measures for Endpoints
Several tools and mitigation strategies are part of an all-encompassing endpoint security plan.
Software Protection:
- Host-based Cisco Advanced Malware Protection (AMP) software (e.g., Cisco AMP for Endpoints).
- Content security appliances for fine-grained control over email and web browsing.
- Antivirus and anti-malware software.
- Endpoint Protection Platforms (EPP) focused on threat prevention at the perimeter.
- Endpoint Detection and Response (EDR) for continuous monitoring, detection, and analysis of endpoint activities, enabling prompt detection and response to suspicious behavior.
- Extended Detection and Response (XDR) solutions provide greater visibility, correlating threat information across endpoints and the network, employing analytics and automation.
- Managed Detection and Response (MDR) offers always-on monitoring by cybersecurity experts.
Access Control and Authentication:
- Network Admission Control (NAC) and Identity Services Engine (ISE) to interrogate devices before they connect, verifying security requirements.
- Network Access Control (NAC) to restrict network resource availability.
- Multi-factor authentication (MFA), a critical component of zero-trust security, requiring multiple identity factors for login.
- Implementing strong authentication measures for API endpoints (e.g., OAuth, two-factor authentication).
Data Protection:
- Encryption to secure data.
- Data Loss Prevention (DLP) to detect and stop data breaches.
Network Controls:
- Firewalls.
- Virtual Private Networks (VPNs) to protect remote connections.
- Network segmentation to divide networks into smaller partitions, limiting traffic flow and attacker movement.
- URL filtering to control user web page access.
- Browser Isolation to isolate web browsing from local networks.
Management and Policies:
- Regular software updates and patch management.
- Keeping an endpoint inventory current for compliance and vulnerability monitoring.
- Establishing clear access policies.
- Zero-trust security, which verifies identity before granting access and applies security controls at user, device, and application levels.
- Automated tools for real-time monitoring and threat detection.
- Endpoint management involves identifying, monitoring, and controlling devices, ensuring optimal function and adherence to policies.
User Training: Staff must be trained to recognize phishing and social engineering.
Overall, securing endpoints is crucial for businesses to protect sensitive data, prevent downtime, and maintain operational continuity, especially with the growing number of devices and evolving cyber threats.
