This blog post discusses multi-factor authentication (MFA) and its benefits and importance, including core authentication factors, common MFA methods, implementation with AAA, MFA vs 2FA authentication, security considerations, and weaknesses.
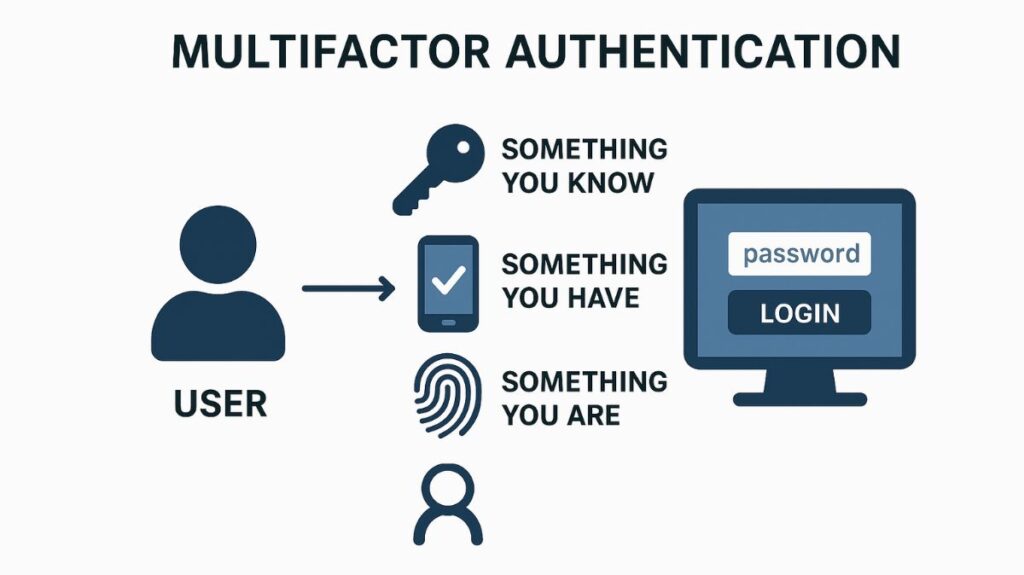
Multi-factor authentication (MFA) is a security system designed to enhance credential complexity and security by verifying a user’s identity only after they have successfully presented two or more distinct types of evidence (or factors) from different categories to an authentication mechanism. MFA makes it difficult for attackers to log in using stolen passwords.
Also Read About What is Dynamic Trunking Protocol DTP Spoofing Overview
The Core Authentication Factors
At least two unique kinds of factors must be used by true MFA systems. Occasionally a fourth or fifth category is introduced, however authentication requirements are usually divided into three sources:
| Factor Type | Description | Examples |
|---|---|---|
| Something You Know (Knowledge) | Information only the user should know. | Password, PIN, Security Question Answers. |
| Something You Have (Possession) | A physical or digital item only the user possesses. | Mobile phone (for codes/push notifications), Hardware Security Key (e.g., FIDO), Smart Card, Authenticator App. |
| Something You Are (Inherence) | An intrinsic physical characteristic of the user, typically biometric. | Fingerprint scan, Facial recognition, Iris scan, Voice print. |
| Location (A potential fourth factor) | Somewhere the user is, or where they are connecting from. | GPS coordinates, trusted network, or source IP address. |
| Behavioral Factors (A potential fifth factor) | Something the user does, based on unique patterns. | Keystroke dynamics, typical IP address range, or recognized trusted device. |
The key difference between multi-factor authentication (MFA) and two-step verification is that using two knowledge factors, such as a password and a security question, does not meet the aim of MFA.
Common MFA Methods
Multiple factor combinations are used to achieve MFA, frequently utilizing mobile devices:
- Mobile apps like Microsoft Authenticator produce 30-second Time-based One-Time Passwords (TOTPs). Users’ phones (Possession) and a time-limited code (Knowledge) are merged.
- Push Notifications: Registered mobile devices can press “Approve” or “Deny” to authorize or refuse logins. A thing you own.
- One-time passcodes are sent via email or SMS. Due to interception and SIM-swapping, this is less secure than authenticator apps despite its popularity.
- Sensors: Touch ID and Face ID are used for biometric verification under Something You Are.
- Adaptive MFA (Risk-Based Authentication) uses AI and machine learning to dynamically determine the number and type of authentication factors needed based on contextual information like the user’s location, time of day, device, and number of failed attempts. High-risk activities may require three or four factors or be rejected, while low-risk actions may only require a password.
Implementation using AAA
Highly scalable, centralized security systems offer multifactor authentication.
- Multifactor user credentials can be supported via centralized authentication, authorization, and accounting (AAA) servers, like the Cisco Identity Services Engine (ISE) platform.
- Authentication Process: The switch or router receives a “challenge” message from the AAA server when a device (Network Access Device or NAS) queries it (e.g., RADIUS/TACACS+) and the server requests further credentials, like those required for multifactor authentication.
MFA vs 2FA authentication
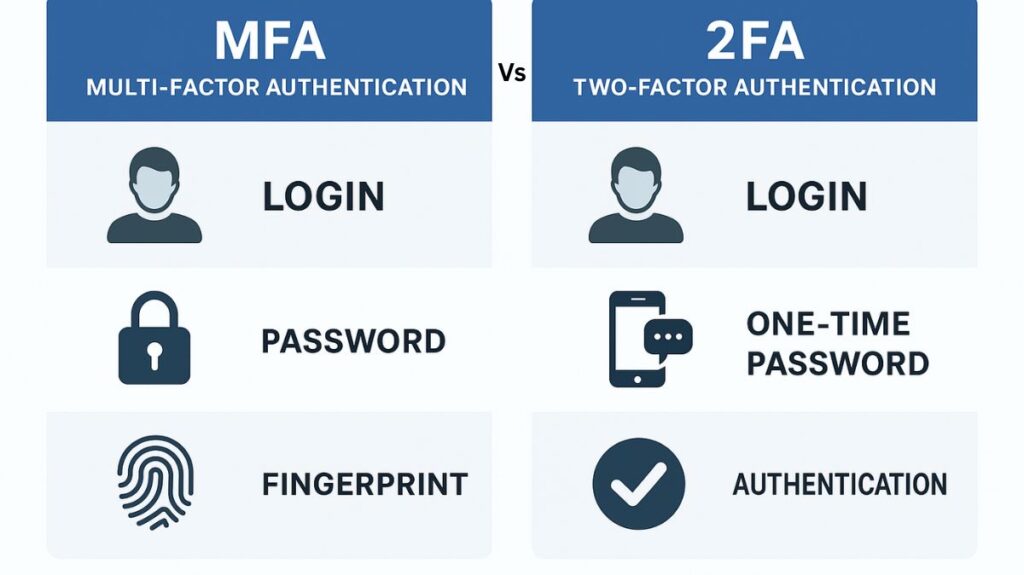
A subset of MFA known as “two-factor authentication” (2FA) requires precisely two different factors. Since two factors are frequently adequate for security, 2FA is now used in the majority of MFA applications. On the other hand, MFA is the more general phrase that describes situations in which two, three, or even more factors may be needed.
An example of two-factor authentication is the requirement for a physical bank card (Something You Have) and a PIN (Something You Know) in order to withdraw money from an ATM.
| Feature | 2FA (Two-Factor Authentication) | MFA (Multi-Factor Authentication) |
|---|---|---|
| Definition | A security process that requires exactly two types of authentication factors. | A security process that requires two or more authentication factors. |
| Number of Factors | Always two factors. | Two or more factors (can be 3 or more). |
| Purpose | Adds an extra layer of security beyond a password. | Provides stronger protection by adding multiple independent layers of authentication. |
| Examples of Factors | 1. Password + OTP (One-Time Password) 2. PIN + Fingerprint | 1. Password + OTP + Fingerprint 2. Smart Card + PIN + Facial Recognition |
| Security Level | Moderate (depends on strength of the two factors). | High (each additional factor significantly increases security). |
| Common Usage | Online banking, email login, or cloud services. | High-security environments, enterprise networks, or government systems. |
| Implementation Complexity | Easier to deploy and manage. | More complex setup; may require hardware tokens or biometric systems. |
| User Experience | Slightly more time-consuming than single-factor login. | Can be slower, depending on how many factors are required. |
Also Read About IPv4 Address Exhaustion: Simple Guide To IP Address Shortage
Benefits and Importance of MFA
MFA offers several benefits for compliance and security:
- Improved Security: It significantly reduces the possibility of account takeover and illegal access. Microsoft claims MFA eliminates 99.9% of credential-based automatic attacks.
- Protects Credentials: A stolen password cannot access an account without the second factor. Data breaches sometimes entail password hacking.
- An attacker cannot log in without the second factor if a user unintentionally submits their password on a phishing website.
- HIPAA, PCI DSS, and GDPR require or recommend MFA for sensitive data.
Also Read About IPv4 Address Exhaustion: Simple Guide To IP Address Shortage
Security Considerations and Weaknesses
Despite its great effectiveness, MFA has drawbacks and weaknesses.
- Usability and Inconvenience: The need for several verification processes may make the login process take longer and cause the user some inconvenience.
- Hardware token systems are more expensive and require more upkeep.
- SMS and email MFA are subject to advanced phishing and man-in-the-middle attacks.
- MFA Fatigue Attacks: This popular social engineering method constantly requests login information via push notifications until the user accidentally clicks “Accept” due to noise.
- SIM Cloning: Because scammers can employ SIM cloning techniques to intercept passcodes transmitted to the victim’s phone number, SMS-based verification is susceptible to vulnerabilities.
