This article gives an overviews Man-in-the-Middle attack, Types Of MitM Attack, how it works, why it is important, Advantages and disadvantages of MitM Attack.
Man-in-the-Middle attack
In a Man-in-the-Middle (MitM) attack, a threat actor places himself in the path of communication between two devices that think they are speaking to each other directly. The main objective of such an attack is to covertly intercept data that is being transferred between these machines. Additionally, attackers can play a more active role by altering the data as it moves through their position as an intermediate.
You can also read Types of Mitigation Techniques, How it Works and Advantages
How MitM attack Works
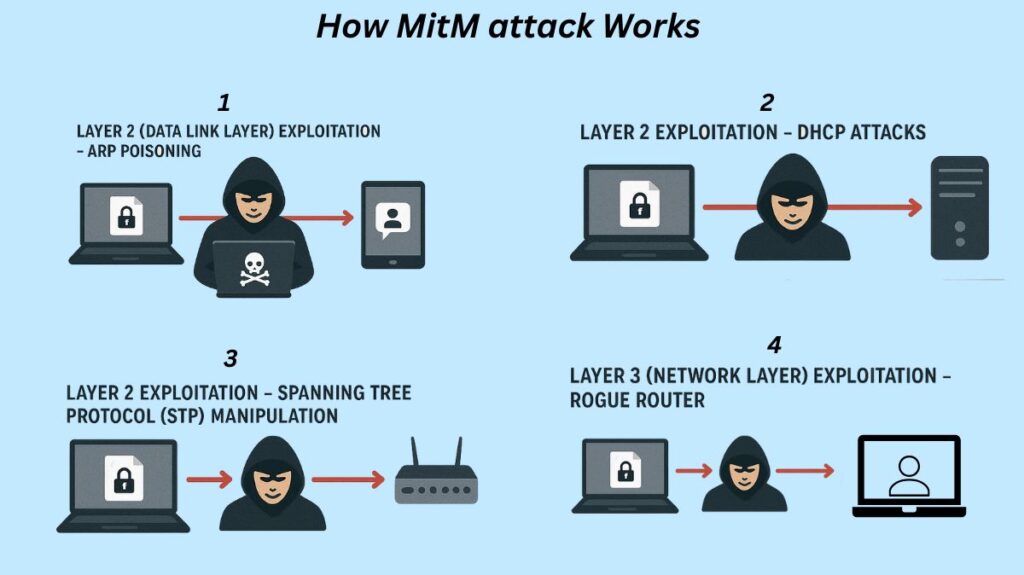
By using the attacker’s computer as a middleman, MitM attacks take advantage of the trust that exists between the parties involved. Several network tiers may experience this:
Layer 2 (Data Link Layer) Exploitation – ARP Poisoning:
- A popular technique is taking use of the Address Resolution Protocol (ARP) table that every host keeps for communication within the local network.
- To determine a target IP address‘s MAC address, a client typically broadcasts an ARP request. The actual MAC address of the rightful owner is returned in response.
- An ARP poisoning attack involves the attacker sending a spoof ARP reply, also known as a gratuitous ARP response, with their own MAC address, posing as the IP address of the legitimate destination.
- Using the attacker’s MAC address for the destination’s IP, listening hosts update their ARP tables in anticipation of the attacker sending the final ARP reply. This causes LAN devices to reroute traffic to the attacker by making them think that the attacker’s Layer 2 address is the Layer 2 address of their default gateway.
- The attacker can carry out this procedure again, contaminating ARP records on several hosts before rerouting traffic between them, frequently evading detection.
Layer 2 Exploitation – DHCP Attacks:
- An attacker can set up a rogue DHCP server to give legal customers erroneous IP setup parameters, including a default gateway address pointing to their device.
- By doing this, the attacker can reroute traffic meant for outside the subnet, creating a MitM scenario in which the attacker can duplicate any data transmitted by the client.
Layer 2 Exploitation – Spanning Tree Protocol (STP) Manipulation:
- To take control of a switch, an attacker can alter its Spanning Tree Protocol (STP). This provides a point of view for a MitM attack by enabling the attacker to monitor any communication that must pass through the root switch.
Layer 3 (Network Layer) Exploitation – Rogue Router:
- By putting a rogue router on the network, an attacker can fool other routers into thinking that it has a better route to specific locations.
- This enables the attacker to steal or alter network data by causing network traffic to pass through the rogue router. In IPv6 networks, a client may route all traffic through a rogue router due to incorrect autoconfiguration by the rogue router, which could result in a MitM attack.
General: The attacker can actively alter data in transit or passively examine communications once they are in position.
You can also read What Is A Network Security Threat? History, And How It Works
Why MitM attack Important
Man-in-the-Middle attacks directly jeopardize core security principles, which makes them extremely significant:
Compromises Confidentiality: Data can be eavesdropped by the attacker, allowing unauthorized individuals to read the information of legitimate users.
Compromises Data Integrity: By altering data flowing between hosts, the attacker may tamper with transmitted data or introduce dangerous new information into network sessions.
Compromises Availability: Conditions known as Denial of Service can be exacerbated by MitM attack.
Enables Further Exploitation: They can help with information theft, traffic analysis for reconnaissance, and hijacking of active sessions to access internal network resources.
Impact on Critical Infrastructure: Cybercriminals have the knowledge and resources necessary to conduct such attacks, which might have an impact on infrastructure and vital systems.
Subtlety: Due to their frequent “avoid detection” design, MitM attacks are very deadly.
You can also read How Is The IEFT Related To The IRTF, History & Types Of IETF
Types of MitM attack
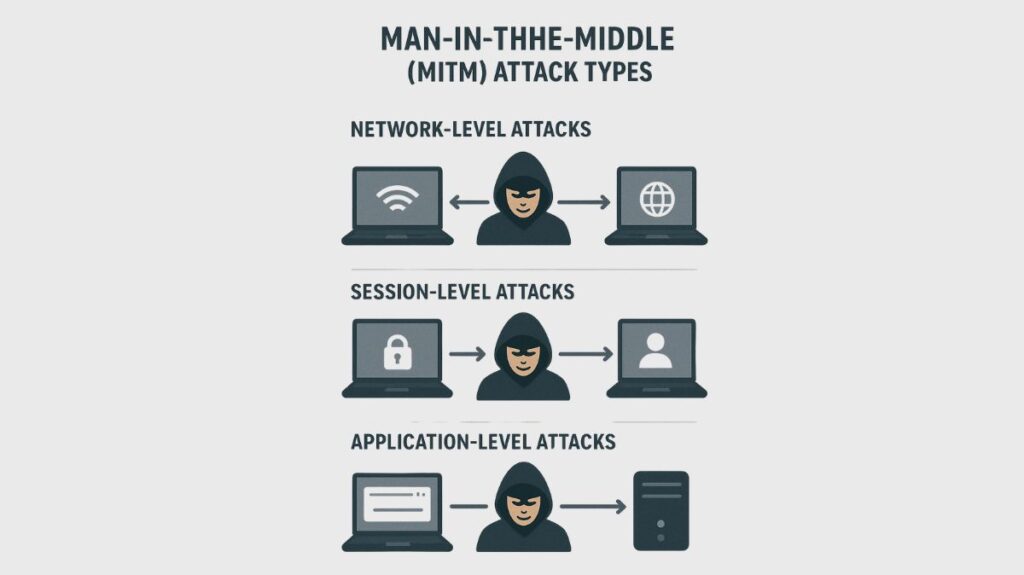
MitM attacks can take many different forms:
Network-Level Attacks
In order to introduce the attacker’s device into the communication channel, these attacks concentrate on taking advantage of flaws in network protocols.
ARP Spoofing/ARP Cache Poisoning: This approach to local area network (LAN) attacks is frequently used. ARP is a protocol that connects a device’s physical MAC address to its IP address. Fake ARP packets are sent to a network by an attacker, who links their own MAC address to a gateway’s or another device’s IP address. By deceiving devices, the attacker receives their traffic and redirects it to the desired location.
DNS Spoofing/DNS Cache Poisoning: Human-readable domain names, such as google.com, are converted into IP addresses by the Domain Name System (DNS), which is the target of this attack. When a user requests a legitimate website, the attacker either delivers a false DNS answer or corrupts the DNS server’s cache, rerouting the user to a hostile, phoney website under their control.
Evil Twin Attack: This technique entails configuring a phoney Wi-Fi access point that looks like a real one (such as “Starbucks Free Wi-Fi”). An attacker can capture and examine data when an unwary person connects because all of their internet traffic is passed through their device.
Session-Level Attacks
These attacks target the user’s ongoing interaction with a service or website.
SSL Stripping (or Downgrade Attack): The secure connection mechanism is exploited in this attack. When a victim attempts to visit a secure website (HTTPS), the attacker intercepts the request and uses a secure HTTPS connection to interact with the website. But the attacker gives the user access to an unprotected HTTP version of the website. Because the user sees a downgraded connection that looks normal, they might not realise that their data is now being sent in unencrypted, making it susceptible to interception.
Session Hijacking: To identify a user for the duration of a session, the server sends a session token, also known as a cookie, to the user’s browser after they log in. Without the user’s password, an attacker can obtain unauthorised access to their account by stealing this session cookie and using it to impersonate the user.
Application-Level Attacks
In these attacks, the application or the user’s device are compromised.
Man-in-the-Browser (MitB): The victim’s web browser gets infected by malware that has been installed on their machine. Despite an encrypted connection, the malware serves as the “man in the middle,” intercepting and changing real-time communication between the browser and the web server. It can steal login credentials while they are being entered, change transaction data, or change web pages.
HTTPS Spoofing: A phoney security certificate is presented to the user’s browser in this more complex attack. This keeps security warnings from appearing by tricking the browser into thinking it is interacting with a trustworthy, secure website. After decrypting the ostensibly secure traffic, the attacker can intercept it.
You can also read Advantages And Disadvantages Of Malware & Types Of Malware
MitM attack Advantages
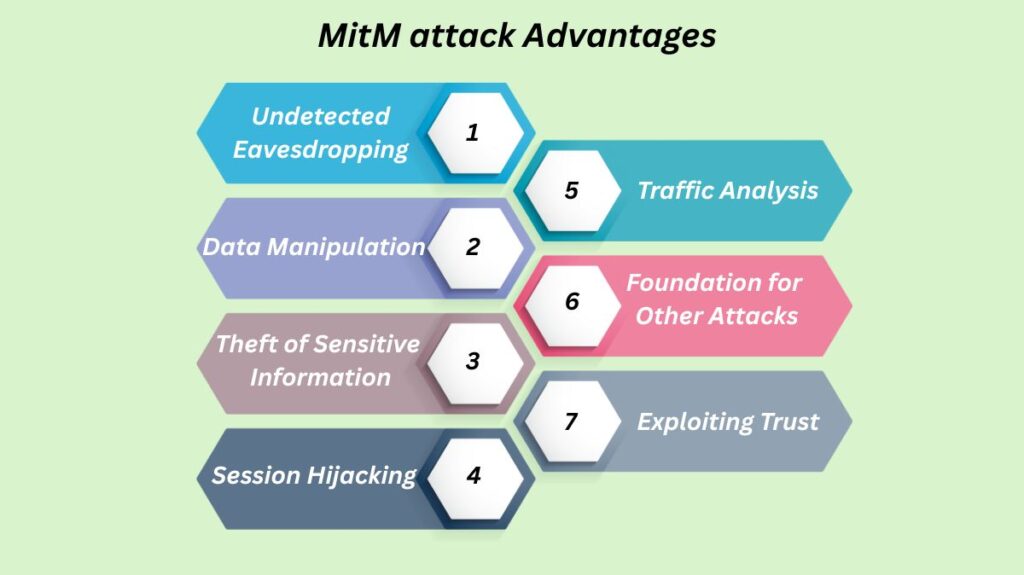
Threat actors can benefit greatly from MitM assaults in a number of ways.
Undetected Eavesdropping: The main advantage is that all traffic between two unwary hosts can be passively inspected, frequently escaping discovery.
Data Manipulation: Fraud or additional system compromise may result from attackers’ active manipulation of data in transit or introduction of new information into sessions.
Theft of Sensitive Information: It is possible to obtain unencrypted usernames, passwords, and other private company data by using packet sniffing.
Session Hijacking: Attackers have the ability to take control of an active session and utilise the privileges of the legitimate user to access internal network resources.
Traffic Analysis: MitM offers a perspective on traffic analysis, providing useful insights into the network and its users.
Foundation for Other Attacks: MitM is frequently an essential step that makes more sophisticated assaults, such Denial of Service, possible.
Exploiting Trust: The implicit confidence systems have in network addresses is exploited by attackers by posing as authentic network devices or gateways.
MitM attack Disadvantages
When it comes to MitM attacks, network defenders face serious risks and drawbacks.
Loss of Confidentiality, Integrity, and Availability: The CIA’s three security pillars are directly threatened by these attacks. Data corruption, loss of privacy, and denial of services are all possible outcomes.
Unauthorized Access: In addition to possibly increasing privileges, attackers can obtain sensitive data and vital systems.
Difficulty in Detection: MitM attacks are difficult to identify because attackers deliberately try to go unnoticed.
Human Vulnerability: Internal users or hacked endpoints may unintentionally act as the “man in the middle,” which makes security awareness and training crucial but difficult.
Complex Mitigation: A multi-layered strategy is needed to effectively defend against MitM attacks, addressing weaknesses at several network tiers and using a variety of protocols.
You can also read What Are Spoofing Attack Types? How It Works, And Advantages
MitM attack Applications
Several mitigation measures are used in a comprehensive security strategy to combat MitM attacks:
Virtual Private Networks (VPNs): By establishing secure communication channels over public networks, VPNs offer anti-replay services (which stop packet replaying), data integrity (which stops alteration), secrecy (which stops eavesdropping), and authentication. Data encryption while in transit is recommended.
Dynamic ARP Inspection (DAI): This Layer 2 switch feature examines ARP messages and compares them to valid MAC-to-IP address mappings in order to prevent ARP spoofing and poisoning.
DHCP Snooping: By acting as a firewall, this Layer 2 feature stops malicious IP configurations from being issued by rogue DHCP servers, which could result in MitM attacks.
Spanning Tree Protocol (STP) Guards: Attackers that attempt to use STP manipulation to take control of the root switch can be thwarted by strategies like root guard.
Routing Protocol Authentication: Routing peers can be protected against Layer 3 MitM attacks by implementing authentication protocols.
Encryption for Management Protocols: An attacker in a MitM position could readily read cleartext protocols like Telnet and HTTP to obtain usernames and passwords, hence it is best practice to utilize secure, encrypted management protocols like Secure Shell (SSH) and HTTPS instead. Moreover, message integrity, confidentiality, and authentication are offered by Transport Layer Security (TLS).
Unicast Reverse Path Forwarding (uRPF): As part of a MitM strategy, this capability can stop assaults that use spoof IP packets.
User Awareness and Training: It is essential to educate users about password hygiene, social engineering attacks (such as phishing and pharming), and the risks of dubious links in order to reduce human weaknesses that an attacker could use to obtain information for a MitM attacks or to establish an initial foothold.
AAA Services (Authentication, Authorization, Accounting): In order to regulate and monitor user activity and make it more difficult for unauthorised individuals (perhaps “men in the middle”) to obtain access or operate discreetly, AAA is used to challenge user credentials, authorise only necessary access, and maintain thorough accounting records.
Intrusion Prevention Systems (IPS): While not exclusively for MitM, IPS devices are designed to detect and prevent attacks by scanning traffic for malicious signatures and abnormal behavior, and can actively block suspicious packets.
You can also read User Security Awareness: Tips For Protecting Your Authority
