Password Attacks

Threat actors employ a variety of techniques known as password attacks to obtain unauthorised access to systems by figuring out or compromising user credentials. These attacks, which are regarded as frequent network attacks, target weaknesses in the creation, storage, and management of passwords.
How Password Attacks Work?
The majority of enterprise network systems employ usernames and passwords for authentication, which is how password attacks work. An attacker can get in if these credentials are weak or not well secured.
Usually, the mechanisms include:
Password guessing: In this technique, attackers merely try to figure out a user’s password several times. They frequently begin by using default or popular passwords like “password,” “password123,” or “123456” or by attempting to use “admin” as both the username and the password.
Online Attacks: When the system asks for user credentials, the attacker enters each password guess directly.
Also Read About What Is A Network Security Threat? History, And How It Works
Offline Attacks: The attacker first obtains hashed or encrypted passwords from the system in order to launch an offline attack. After that, they move them offline to a different computer, which repeatedly tries to decrypt or crack the real passwords using specialised software without having to communicate with the target system. Because there are so many possible combinations, offline attacks usually take a lot of time and sophisticated computational resources.
Dictionary Attacks: Often called a dictionary or word list, this technique involves software that automatically tries to log in using passwords derived from a pre-compiled list of words, names, or popular phrases. Thousands or millions of attempts may be required for this. Dictionary attacks, which attempt to guess the pre-shared key by recording the four-way handshake, are another known vulnerability against WPA-Personal and WPA2-Personal wireless networks.
Brute-Force Attacks: In order to find a password match, software systematically tries every possible combination of letters, numbers, and symbols in a technique known as a brute-force attack. Brute-force attacks need a significant amount of time and extremely powerful computational resources, just like offline dictionary attacks. To obtain privileged access, an attacker may employ a brute-force attack against the “enable secret” password on a router.
Assistance from Other Attacks:
- Eavesdropping/Packet Sniffing: Certain programs provide private data over a network in cleartext, or unencrypted, including usernames and passwords. These messages can be intercepted by tools such as packet sniffers, which then disclose the credentials.
- Because Telnet, for example, transmits all data in cleartext, its password exchanges are susceptible to Man-in-the-Middle (MitM) attacks, in which a hacker intercepts traffic and may readily read the password. Password attacks can also be facilitated by MitM attacks using keyloggers or packet sniffers.
- Malware: Trojan horse programs have the ability to pose as trustworthy software in order to track login attempts and record user account and password details. Password attacks can potentially be made easier by malware in general.
Why it is Important?
Because password attacks directly jeopardise the security of network systems and data, it is imperative to comprehend and mitigate them.
- Privilege Escalation and Unauthorised Access: Attackers can obtain unauthorised access by using passwords that are simple to figure out. An attacker can obtain elevated rights by compromising the login and password of an administrator account, which might do serious harm or even take over the entire network. Access attacks are specifically used to increase privileges, obtain access, or recover data.
- Data Theft and Business Disruption: By using strategies like eavesdropping, successful password attacks can result in the theft of private information, including financial and personal data. Costly network disruptions, lost productivity, and damage to valuable assets are possible outcomes of this.
- Basis for Additional Attacks: Password compromises can give hackers the first foothold they need to initiate more complex attacks, open backdoors for ongoing access, or compromise more systems.
- Pervasive Vulnerability: Since most system access attempts involve usernames and passwords, password vulnerabilities are a continual target.
Also Read About What Are The Common Network Security Vulnerabilities?
Types of Password Attacks
Password attacks come in a variety of forms:
Online Password Attacks
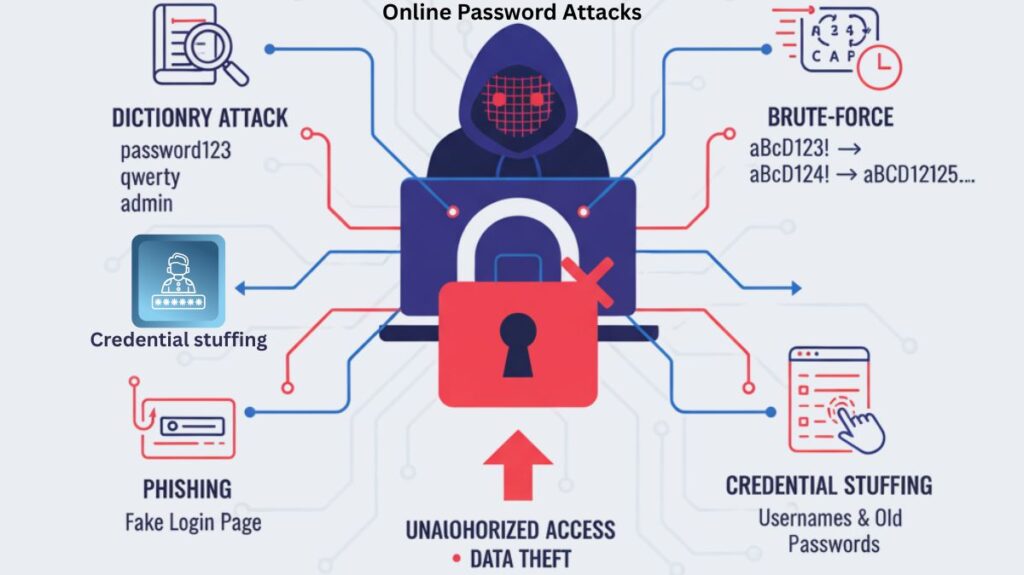
These attacks, which usually target the account’s authentication system, are launched directly against the login page of a service.
- In a brute-force attacks, the attacker methodically attempts each password combination until they discover the one that works. Attackers frequently utilise automated systems to test millions of variations per second because this is an extremely time-consuming strategy.
- Dictionary Attack: A brute-force attack that is more effective. The attacker employs a precompiled list (a “dictionary”) of frequently used words, phrases, and passwords rather than attempting every possible combination. Frequently used versions such as “password123” or “P@$$w0rd” are added to these lists.
- Using a few popular passwords (like “password123”) against numerous users at once is known as “password spraying.” Avoiding account lockouts, which usually happen after too many unsuccessful attempts on a single account and make the attack more difficult to identify, is the aim.
- Credential stuffing is the practice of attackers attempting to access other websites by using username and password pairs that have been obtained via a data breach on one site. Because so many people use the same login credentials for several services, this attack is very successful.
Offline Password Attacks
The login page of a live service is not immediately impacted by these attacks. Rather, attackers attempt to crack hashed passwords on their own computers after obtaining a database of them.
Attackers employ precomputed “rainbow tables,” which are enormous databases containing passwords that have already been hashed, in the rainbow table attack. To determine the original plaintext password, they use a stolen password hash and search the table for it. Password salting is an essential defence because it is significantly faster than hashing each password separately. Salting prevents the use of pre-computed tables by adding a distinct random string to each password prior to hashing.
Also Read About How Is The IEFT Related To The IRTF, History & Types Of IETF
Social and Non-Technical Attacks
Instead than taking advantage of technical flaws, these attacks take advantage of human behaviour.
- The most prevalent type of password assault is phishing. An attacker poses as a reputable source (such as a bank or social networking platform) in order to send phoney emails, texts, or instant messaging. When the user clicks on a link in the message, they are taken to a phoney login page where they unintentionally submit their credentials, which are subsequently stolen.
- Installing an application or a physical device (a keylogger) on a user’s computer in order to record their keystrokes is known as keylogging. Passwords and usernames can then be found by the attacker by looking through the logged data.
- Shoulder surfing is a low-tech technique in which a hacker watches a person type their password up close, usually in a public setting like an airport or cafe.
