Virtual Private LAN Service VPLS
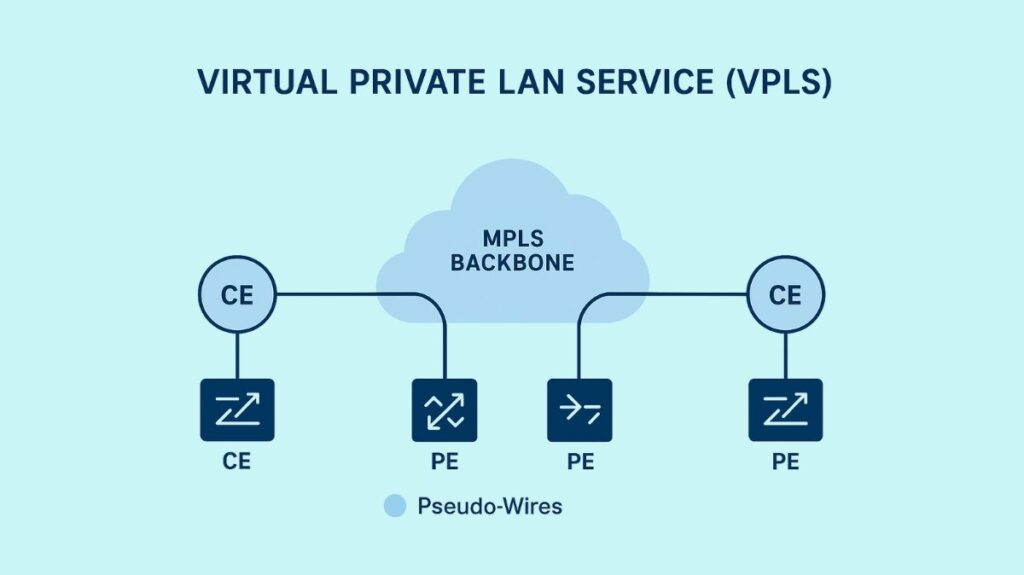
Geographically separated locations can connect and operate as though they were all connected to a single Ethernet Local Area Network (LAN) switch or sharing a single bridged Ethernet LAN to the Virtual Private LAN Service (VPLS), a Layer 2 Virtual Private Network (VPN) technology.
Ethernet-based multipoint-to-multipoint communication via underlying IP or MPLS networks is made possible by VPLS. In essence, the technique connects locations (such as servers and clients) via pseudowires so that they can share a single Ethernet broadcast domain.
Important Features and Synopsis
- VPN Type: VPLS falls under the Layer 2 VPN (L2VPN) category. It functions at Layer 2, or the Data Link Layer.
- Connectivity Model: Unlike L2TPv3, which normally only permits point-to-point Layer 2 tunnels, it facilitates any-to-any (multipoint) connectivity.
- Emulation: The service creates a single bridging LAN by using the provider network to join all of the customer LANs in a manner similar to a switch or bridge. PEs participating in VPLS are required to show up as an Ethernet bridge to Customer Edge (CE) devices that are connected.
- By extending Ethernet services over an MPLS or IP network, encapsulation gives distant locations the appearance of being linked to the same switch.
Architecture and Operation
VPLS mimics how an Ethernet switch or bridge would behave over a wide area network (WAN).
Core Components
- Customer Edge (CE) Equipment: Usually Ethernet, these are the routers or switches that link the customer’s local area network (LAN) to the service provider’s network.
- The routers at the network’s edge that belong to the service provider are known as Provider Edge (PE) routers. The “VPN intelligence” is stored on PE devices.
- Every VPLS customer has a Virtual Switch Instance (VSI) running on each PE router. including a local switch, the VSI controls common Ethernet features, including forwarding and MAC address learning.
- Provider (P) Network: Typically built on an MPLS backbone, this is the central component of the service provider’s network.
- Data Plane/Pseudowires (PWs): To transport Ethernet frames between sites, all participating PE routers create a logical full mesh of point-to-point tunnels, or pseudowires. The data plane is made up of PWs. Technologies such as Ethernet over MPLS, L2TPv3, or GRE can function as pseudowires.
Also Read About What Is Inter VLAN Routing And How Inter VLAN Routing Works
Frame Handling and Loop Avoidance
- MAC Learning: PEs pick up the Media Access Control (MAC) addresses of CE devices from incoming frames, just like a conventional switch would. This MAC address and related LSP routing data are stored by the PE.
- Sending:
- Unicast: Only the particular pseudowire that leads to the target PE is used to send frames that are intended for a known MAC address.
- Broadcast/Multicast/Unknown Unicast (BUM): The PE floods all other PEs in the mesh across all pseudowires in that VPLS instance if a frame is a broadcast or if its destination MAC address is unknown.
- Loop Avoidance: A PE never sends a frame received from another PE to another PE since Ethernet transmissions do not contain a Time To Live (TTL) field. A broadcast domain free of loops is guaranteed by the combination of split horizon forwarding with a full mesh structure.
Control Plane and Signalling
The “control plane” specifies the communication between PE routers for signalling (setting up the pseudowires) and auto-discovery (locating other PEs in the VPLS). The complete mesh is established using two techniques:
- Border Gateway Protocol (BGP): Layer 3 MPLS VPNs are established using BGP’s identical procedures. Both auto-discovery and signalling are capabilities of BGP; PEs set up for a VPLS simultaneously find every other PE and create a complete mesh of pseudowires. VPN IDs and VPN-specific reachability data can be distributed via BGP4 Multi-Protocol extensions.
- Label Distribution Protocol (LDP): LDP requires that the addresses of other PEs taking part in the same VPLS be manually provided to each PE router. An analogous mesh of pseudowires (virtual circuit IDs) is created using LDP after a complete mesh of LDP sessions has been constructed.
Also Read About What Is VLAN Hopping Attack? How Does VLAN Hopping Work
Enhancements and Scalability
Scalability issues arise from VPLS’s requirement for a complete mesh in both the control and data planes.
Hierarchical VPLS (HVPLS): This technique was created to split a VPLS VPN into two or three tiers of hierarchical networks, and it is frequently used with LDP. In order to reduce the amount of Label Switched Paths (LSPs) and LDP sessions required in the core network, HVPLS adds the multi-tenant unit (MTU) switch, which combines several customers into a single PE. It is also possible to combine two different VPLS mesh architectures using HVPLS.
MAC Address Scalability: Each PE must keep track of all related MAC addresses since VPLS generates a very large broadcast domain, which can use a lot of memory.
Solutions include installing Content-Addressable Memory (CAM) on PEs or employing a router as the CE device to conceal site MAC addresses behind the CE’s MAC address.
Advantages and Drawbacks
Advantages of VPLS
LAN-like connectivity between locations
- Enables the extension of a single Ethernet LAN to several geographically disparate locations.
- Gives the impression that distant workplaces are connected to the same local network.
Layer 2 Transparency
Functions at Layer 2, allowing users to use their own IP addresses and routing without interference from the provider.
Any-to-Any Interaction
Latency can be decreased by allowing all linked sites to communicate directly without directing traffic via a single hub.
Simplified Network Management
Only Ethernet connectivity is needed; complicated Layer 3 setups on the customer’s end are not necessary.
Supports Broadcast, Multicast, and Unicast Traffic
Permits the use of programs like ARP and dynamic routing techniques that depend on Ethernet broadcast domains.
Flexibility and Scalability
Sites can be added or removed with ease without affecting the network’s overall configuration.
Secure Data Transport
Provides each customer with traffic isolation through MPLS label-based segmentation.
Perfect for Interconnecting Data Centres (DCI)
Enables smooth communication between several data centres for redundancy and load balancing.
Also Read About What is MPLS Layer 3 VPN? Key Components and Benefits
Drawbacks of VPLS
Scalability of MAC Addresses
Scalability is restricted because every Provider Edge (PE) device needs to keep a whole MAC address database for every customer.
Flooding of Broadcast and Multicast
Performance might be impacted by excessive broadcast or multicast traffic using up bandwidth.
Ineffective for Networks of a Large Scale
As the number of sites increases, managing MAC tables and pseudo-wires gets more difficult.
No Traffic Prioritisation or Native QoS
Quality of Service is not built into VPLS; it must be provided at the MPLS or IP layer.
Greater Overhead Compared to VPNs Using MPLS Layer 3
Because VPLS simulates Layer 2 switching, it may need additional bandwidth and processing power.
Challenging Troubleshooting
Its flat Layer 2 architecture makes fault and loop isolation more difficult.
Latency in Vast Geographic Areas
Physical distance still causes propagation delay between locations even when it lessens hub dependence.
Also Read About CISCO LLDP Link Layer Discovery Protocol Advantages, Types
