Web Proxy Server definition
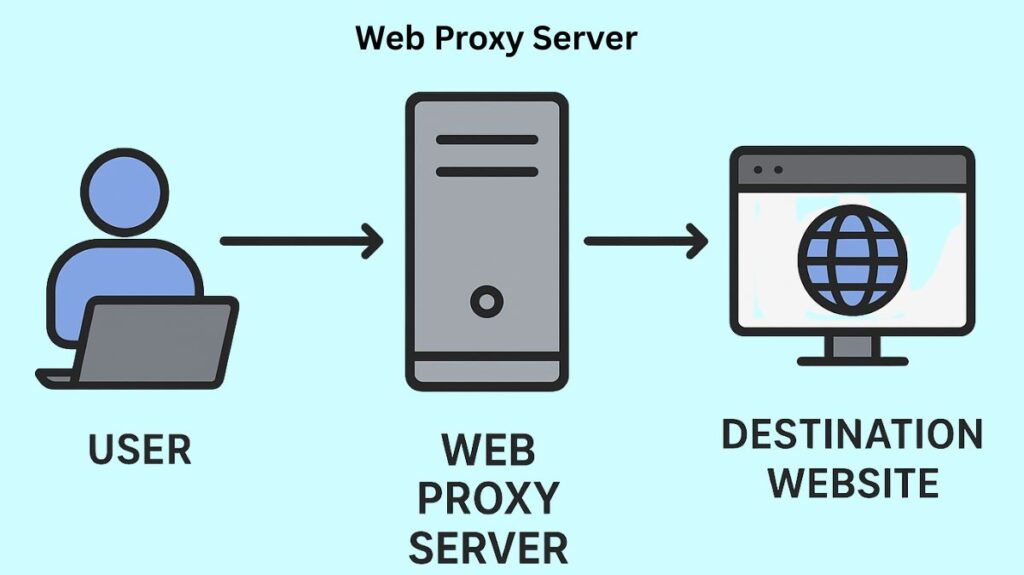
A middleman between a user’s web browser (client) and the internet is a web proxy server. Instead of connecting directly to a website, the web proxy server evaluates the client’s request and performs the necessary network activities. After receiving web server responses, the proxy sends data to the user’s browser.
How a Web Proxy Server Works
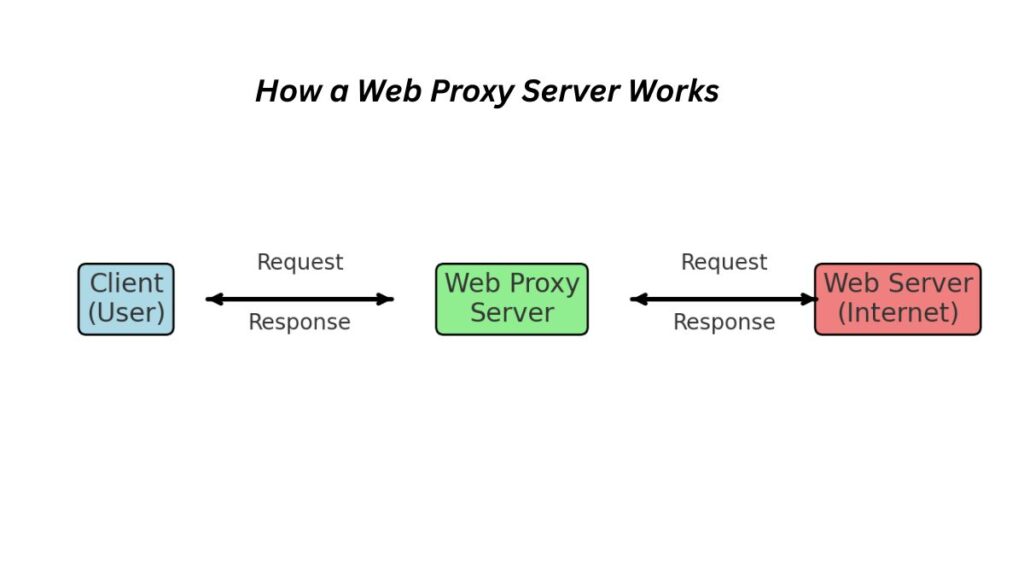
Communication with a web proxy server normally goes like this:
- Request: Your browser requests a webpage or resource from the web proxy server. In particular, web proxies relay HTTP queries that contain the entire URL.
- Forwarding: The proxy server sends the request to the destination web server after evaluation. This stage shows the proxy server’s IP address instead of yours on the website.
- Reaction: The requested data is returned to the proxy server by the target web server.
- Delivery: The proxy server may check the data for security issues before transmitting it to your browser.
Also Read About What Is DNAT Destination Network Address Translation? Uses
Since the destination server only talks to the proxy, this intermediary role protects user privacy. The original purpose of proxies was to give dispersed systems structure and encapsulation.
Example:
Each computer has an IP address to communicate with others. Your computer knows the proxy server’s IP.
- Your browser opens a webpage.
- Your request first reaches the proxy server rather than the website itself.
- On your behalf, the proxy reads your request and forwards it to the website.
- Instead of sending the response straight to you, the website relays it back to the proxy.
- The proxy looks for security flaws in the answer, such as malware.
- The data is sent to your browser via the proxy if everything appears to be in order.
In addition to concealing your real IP address, this procedure occasionally improves the speed or security of your connection.
Types and Applications of Web Proxies
The main purpose of web proxy servers is to forward HTTP requests. Typical implementations and associated kinds include:
General Web Proxy Servers
Forward HTTP requests by providing the complete URL rather than simply the route. HTTP CONNECT, used for HTTPS on port 443, can forward any data. Examples include HAProxy, IIS, Nginx, Privoxy, Squid, WinGate, Ziproxy, Tinyproxy, RabbIT, Polipo, and Apache (mod_proxy or Traffic Server.
Forward Proxy
The most used proxy, this one lets clients connect to servers across the internet. It filters unknown traffic within an internal network, masks client IP addresses, maintains security, and controls traffic according to policies.
Transparent Proxy
Often referred to as an intercepting proxy, this tool intercepts standard application layer communications without the need for additional client setup. Most clients don’t even know it exists. Businesses frequently employ transparent proxies for caching in order to enforce permissible use guidelines and enhance network speed. They could, however, lead to problems with HTTP authentication and caching and be vulnerable to security risks like SYN-flood attacks.
CGI Proxy
This type of proxy server was created to increase website accessibility. Using a web form, it receives requests to target URLs, processes them, and then returns the results to the web browser. Although some privacy rules, such as virtual private networks (VPNs), have made it less popular, it still gets a lot of requests. Its usage decreased because of the potential for excessive traffic to reach the website after it has passed local filters, which could harm the organisation.
Suffix Proxy
In essence, a suffix proxy server adds the proxy’s name to the URL. There is no greater degree of anonymity maintained by this kind of proxy. It is employed to get around web censors. Although it is simple to use and install, its greater number of web filters makes it less popular. (e.g., “en.wikipedia.org.SuffixProxy.com” ). Although they are simple to use, they are mostly used to get around site filters and provide less anonymity.
Anonymous Proxy
It conceals all communications at several levels using encryption. I2P is a completely distributed proxy since this encrypted data is then sent via multiple network routers situated at various locations. This program is open-source and free to use. It is censorship-resistant as well.
High Anonymity Proxy
The High Anonymity Proxy hides your IP address and identity as a proxy server for maximum anonymity.
Also Read About IPv4 Address Exhaustion: Simple Guide To IP Address Shortage
Distorting Proxy
This type of proxy conceals its identity while posing as a website proxy. It accomplishes this by switching to an incorrect IP address.
For those who wish to conceal their location when using the internet, distorting proxies are a useful option. This kind of proxy can provide the impression that you are surfing from a particular nation and offers the benefit of concealing both your identity and the proxy’s. This implies that your identity is safe even if you are linked to the proxy. However, certain websites may prevent end users from accessing necessary websites by automatically blocking distorting proxies.
Residential Proxy: Residential proxy
You can get an IP address associated with a particular physical device by using a residential proxy. That device is then used to channel all requests.
Users that need to confirm the advertisements that appear on their website can use residential proxies to block cookies and unwanted or questionable ads from competitors or malicious actors. Compared to other proxy choices, residential proxies are more reliable. Users should carefully consider if the advantages outweigh the additional cost, though, as they are frequently more expensive to use.
Rotating Proxy
Every user connecting to a rotating proxy is given a unique IP address. Users are assigned a unique address as they connect, which differs from the address of the device that joined first.
For users who must perform a lot of continuous, high-volume web scraping, rotating proxies are perfect. They enable you to visit the same website repeatedly without revealing your identity. You must exercise caution, nevertheless, while selecting rotating proxy services. Some of them have shared or public proxies that might make your information public.
SSL Proxy
Between the client and the server, a secure sockets layer (SSL) proxy facilitates decryption. The proxy conceals its existence from both the client and the server since the data is encrypted in both directions.
Organisations that want further security against attacks that the SSL protocol identifies and neutralises are the greatest candidates for these proxies. When used in conjunction with a website, an SSL proxy may improve its search engine position because Google favours servers that use SSL. The drawback of using an SSL proxy is that it prevents content from being cached, which can result in poorer performance when you visit a website more than once.
Tor Onion Proxy
The goal of this server is to protect users’ personal information when they are online. In order to make it more difficult to track a user’s address and guard against attacks on anonymous activity, it is used to route traffic over a variety of global networks. Anyone attempting to locate the original address finds it challenging. The data is encrypted in a multi-layer layer in this kind of routing. To keep the data from jumbling and to preserve the original content, each layer is decrypted individually at the destination. This program is available for free and is open-source.
12P Anonymous Proxy
All of the communications are hidden at several levels using encryption. I2P functions as a completely distributed proxy since this encrypted data is then transmitted via multiple network routers situated at various places. This program is open-source, free, and censorship-resistant.
Web proxies offer many benefits, but incorrectly configured ones might expose networks to the internet. Free proxy services may also have poor performance, data security issues, browsing history logging, and lack of encryption that could reveal private information.
Also Read About What Are The Advantages And Disadvantages Of LAN
Advantages of Web Proxy Servers
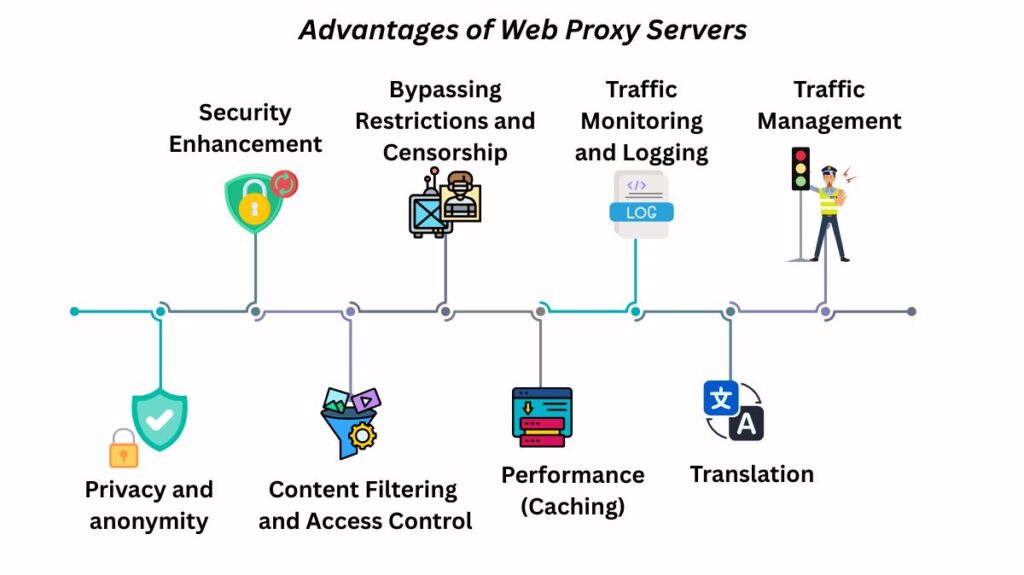
Web proxy servers have several advantages:
Privacy and anonymity: They hide your IP address and browser history against website tracking. Anonymous proxy servers provide anonymous online browsing. High-anonymity proxies hide your IP address and their proxy server identity.
Security Enhancement: Web proxies, like firewalls, protect against malware, specialized operating systems, and web-server-specific assaults. They can prevent fraudsters from targeting endpoints by hiding client IP addresses and internal network designs. Passwords and other sensitive data can be encrypted.
Content Filtering and Access Control: Companies and schools can prohibit or limit access to websites and online services that breach use standards via access control and content filtering. DNS blacklists, URL regex, MIME, and content keywords filter. Several proxies can analyze outbound traffic for malware or data loss.
Bypassing Restrictions and Censorship: Proxy servers allow users to evade network firewalls and regional content limits from corporations and governments.
Performance (Caching): Proxy servers cache popular resources and web pages. By responding faster to requests, upstream bandwidth utilisation, expenditures, and load times are reduced.
Traffic Monitoring and Logging: Proxies can log URLs visited, bandwidth consumption, and traffic trends for increased security and performance. Organisations may monitor employee traffic and prevent data leaks with this.
Translation: By substituting translated content for original language content as it travels via the proxy, a translation proxy can localize a website experience for various markets.
Traffic Management: Using a single Internet connection, a web proxy server can manage several user requests.
Disadvantages
- Processor-intensive: The majority of the work is carried out by proxy server software, which uses a lot of computing power.
- Limited application support: In reality, support may only be available for a select few applications; not all applications may be supported.
- Requirements for client software: Some programs may call for specific client software.
- Resource-intensive: May require a lot of RAM and disc space.
- Single point of failure: Possibly, in the event that fault tolerance is not set up.
As user packets join the corporate network, the SSL server proxies (Port Address Translation [PAT]) the traffic in the context of SSL VPNs, especially clientless and full AnyConnect SSL VPN clients.
The Cisco Web Security Appliance (WSA) is a solution that gives customers total control over their Internet access by combining powerful virus protection, application visibility and control, acceptable usage policy controls, and reporting. WSA is capable of carrying out tasks like:
Also Read About What Is An Email Server? How It Work, Features And Functions
- Filtering and blacklisting URLs.
- URL classification and malware detection.
- Filtering web applications.
- Web traffic encryption and decryption. For instance, the Cisco WSA will assess the URL, reject the packet, and notify the user that “access denied” if they try to connect to a known blacklisted website.
