In order to make data, resources, and services easier to share, computer networking entails connecting two or more computing devices. Through the support of programs like email, file sharing, and web browsing, it functions as a system that facilitates the effective interchange of data.
Here is an overview of the foundations of networking:
What is a Network?

A collection of linked devices that exchange data and resources is the basic definition of a network. These gadgets may consist of hardware such as printers, servers, and PCs. Moving data between devices is a network’s main function, allowing for local or remote communication and resource sharing.
What Are Benefits Of Networking
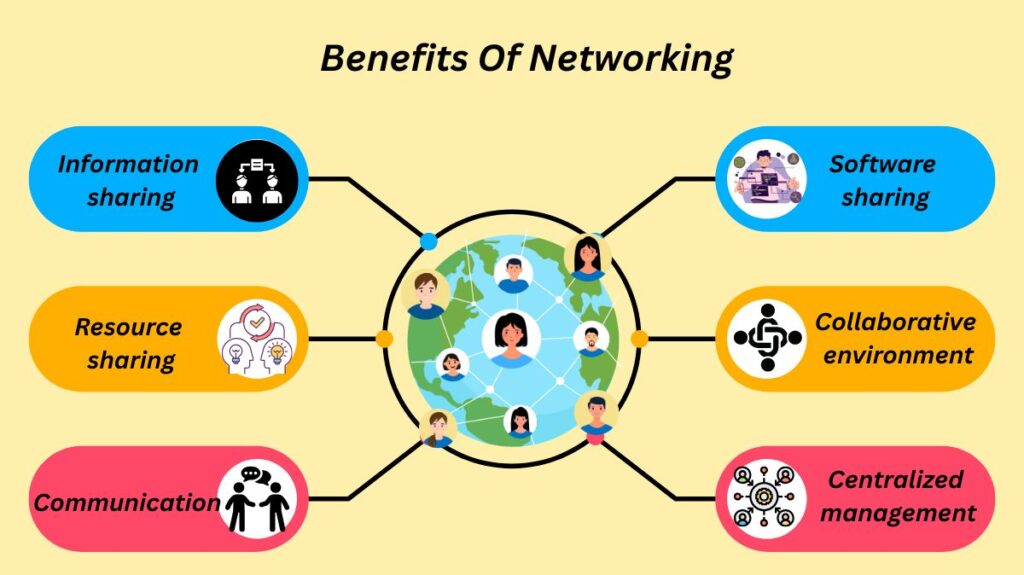
Information sharing: Data and information, including databases and group projects, can be accessed and shared via the network by authorised users.
Resource sharing: It is possible for numerous users to share devices such as printers, scanners, internet connections, and storage.
Communication: Numerous communication channels, including video calls, instant messaging, and email, are made possible by networks.
Software sharing: Installing software on a central server enables numerous people to access it from one place.
Collaborative environment: Through the integration of various equipment capabilities, users can collaborate on projects.
Centralized management: From a single central place, systems may be managed and observed.
Basic Terminologies of Computer Networks
Network: A collection of networked computers and gadgets that can exchange information and talk.
Node: Anything that can transmit, receive, or forward data over a network. This covers devices such as servers, printers, earphones, computers, and cell phones.
Link: The communication medium between nodes might be wireless (such as Wi-Fi signals) or physical (such as Ethernet cables).
IP Address (Internet Protocol address): For the purpose of identification and proper data routing, each device on a network is given a unique number label, or logical address. IPv6 addresses are 128 bits in size, whereas IPv4 addresses are 32 bits.
MAC Address (Media Access Control address): A distinct physical address (hardware identity) linked to a device’s Network Interface Card (NIC), given at the time of manufacture.
Port: A logical channel is a 16-bit integer that is used to send and receive data to an application. The port number of each program on a host is used to identify it. As well-known (0–1023), registered (1024–49151), and ephemeral (49152–65535), there are 65,536 ports available.
Socket: An IP address and port number are a unique combination.
Hostname: Every device in a network has a distinct device name.
How Does a Computer Network Work?
The fundamental components of a computer network are links and nodes.
Equipment for data communication, such as a modem, router, etc., or data terminal equipment, such as linking two or more computers, can be seen as a network node.
Wires, cables, or open space in wireless networks are examples of links in computer networks.
The simplest way to describe how computer networks operate is as rules or protocols that facilitate data transmission and reception along the links that enable communication between computer networks.
To aid in device identification, every device has an IP address.
All incoming and outgoing traffic is monitored by a firewall, which is a hardware or software-based network security device that admits, rejects, or drops certain data according to a predetermined set of security rules.
Types of Computer Network Architecture
The following general categories apply to computer networks:
Client-Server Architecture: Computer networks that use client-server architecture allow their nodes to be either clients or servers. Here, the behaviour of the client node can be controlled by the server node.
Peer-to-Peer Architecture: Peer-to-Peer (P2P) architecture does not include the idea of a central server. Every device is free to operate as a client or server.
Network Devices
A variety of hardware components are used to build networks in order to support and manage networking functions.
Routers: Data packets are forwarded between networks by Layer 3 devices, which use IP addresses to choose the most efficient route. They maintain routing tables and divide broadcast domains.
Switches: Contemporary Layer 2 devices use MAC addresses to forward data to the correct location and link devices within a single network. By separating collision domains, they divide networks into segments, resulting in more effective capacity and traffic flow.
Hubs: Outdated Layer 1 devices that merely connect cables and broadcast data to every device in the network. In half-duplex mode, they represent a single broadcast domain and collision domain.
Access Points (APs): Gadgets that make it possible for wireless devices to join a conventional wire network.
Network Interface Card (NIC): Hardware with a hard-coded MAC address and the ability to communicate physically.
Firewalls: Devices that monitor and regulate incoming and outgoing network traffic according to predetermined security rules might be either hardware or software-based.
Repeaters (Amplifiers): Signal deterioration over distance is compensated for by electronic equipment that receive, amplify, and retransmit signals.
Modems (Modulator-Demodulator): Devices that change digital data into analogue signals so that they can be sent via telephone lines and other voice communication networks, for example.
Gateways: Devices that convert protocols so that different networks can communicate with each other. While “gateway” refers to special-purpose devices for application layer protocol conversions, “router” is a term frequently used in the context of TCP/IP to describe routing devices.
Types of Computer Networks
Networks are divided into groups according to their purpose or geographic reach:
LAN (Local Area Network): Links devices in a certain location, like a house, workplace, or school campus. Generally speaking, they are fast and governed by a single organisation.
WAN (Wide Area Network): Connects devices over great distances, frequently using infrastructure that is leased from service providers, and covers a wide geographic area. The largest example of a wide area network is the Internet.
MAN (Metropolitan Area Network): Spans a city, joining clusters of local area networks (LANs) throughout the metropolis.
PAN (Personal Area Network): Connects items in close proximity, usually for a single individual, like Bluetooth connections.
Intranet: A private LAN, frequently protected by a firewall, that is intended for use by all employees in a company.
Extranet: A network that securely links authorized external parties with employees of a corporation, available from any location.
SOHO (Small Office/Home Office) Networks: Smaller networks, usually consisting of a router, switches, and a firewall, that are utilized for business applications.
Enterprise Networks: Large networks that companies have set up for employee communication.
Network Topology
Network topology describes how various devices are arranged within a network:
Bus Topology: A single central cable known as a bus connects all of the gadgets. Every station in an Ethernet LAN can be connected to a single long cable using a bus topology.
Star Topology: A hub or switch serves as the core node to which all devices are connected.
Ring Topology: Every gadget is connected to two other devices in a circular pattern. Data usually only moves in one way.
Mesh Topology: High redundancy is provided by each device in the network being connected to every other device.
Tree Topology: A star-bus topology combo that works well for setting up big networks and making expansion simple.
Hybrid Topology: A blend of two or more distinct topologies.
Point-to-point topology: A network configuration in which two devices are linked directly together via a single dedicated link.
Networking Models
Comprehensive sets of documents known as networking models outline the structure and tiers for standards and protocols that should be present in a computer network.
OSI Model (Open Systems Interconnection): To standardize data networking protocols, the International Organization for Standardization (ISO) created a seven-layer reference model. Its nomenclature is frequently used and useful for debugging, even though it is not always employed for full protocol implementation. Layers are Physical, Data Link, Network, Transport, Session, Presentation, and Application.
TCP/IP Model: The most common networking model currently in use, which the CCNA test focusses a lot on. In general, it divides functions into four or five layers: Network (or Internet Layer), Application, Transport, and Network Access (which combines Physical and Data Link).
Network Protocols
A protocol is a collection of guidelines or methods that specify how two parties can interact via a network.
TCP/IP (Transmission Control Protocol/Internet Protocol): The core set of protocols that make up the internet. IP uses IP addresses to route data packets, whereas TCP guarantees dependable data delivery and order.
HTTP (Hypertext Transfer Protocol) and HTTPS: Protocols that are used to send web pages. HTTPS offers safe communication with SSL/TLS encryption, whereas HTTP is insecure.
SMTP (Simple Mail Transfer Protocol): Used to transmit emails; frequently, POP3 and IMAP are used for retrieval.
FTP (File Transfer Protocol): Utilized for file management on a distant server, uploading, downloading, and file transfers between PCs.
DHCP (Dynamic Host Configuration Protocol): Automatically allocates IP addresses to networked devices, eliminating the need for human configuration and conflicts.
DNS (Domain Name System): Converts easily navigable domain names (like www.google.com) into numeric IP addresses, guaranteeing smooth internet access.
ARP (Address Resolution Protocol): Used to translate an IP address into the MAC address that goes with it.
RARP (Reverse Address Resolution Protocol): Although it is no longer in use due to DHCP, it gives a device’s IP address when it is given a physical address.
Network Security
Maintaining network security is essential to shielding resources and data against intrusions and illegal access. Important features include of:
Firewalls: Devices or software that use security rules to monitor and regulate network traffic.
Encryption: Encoding data to avoid unwanted access is a widespread practice in encrypted email, HTTPS, and VPNs.
Intrusion Detection Systems (IDS): Instruments for keeping an eye on network traffic for unusual activities.
Access Control: Systems that limit access to network resources according to the role and identity of the user.
Regular Updates and Patching: Maintaining hardware and software updates to guard against vulnerabilities.
Strong Passwords: Enabling secure network and device passwords.
Anyone learning to become a network expert or working with computer systems and communication must comprehend these basic ideas.
Cisco’s Role
With a strong emphasis on Cisco products and technologies, the CCNA certification equips candidates to install, operate, and manage small-scale networks, such as LANs and WANs. Cisco systems are widely used in networking.
You can also read What Is A CISCO Company? Check Cisco Certification Levels
