Baiting Attack

Using human instincts and needs, baiting attack is a common form of social engineering attacks that deceives a victim into jeopardizing their own security. The main objective is to trick the victim into falling into a trap that will let the attacker to access a system or network without authorization, install malware, or steal confidential data.
Baiting attacks prey on fundamental human tendencies, including the need for something free, curiosity, or avarice.Baiting attack is still a successful and popular method since it depends on psychological manipulation rather than sophisticated technology exploitation.
You can also read Clone Phishing Definition And How To Prevent Clone Phishing
How Baiting Attacks Work
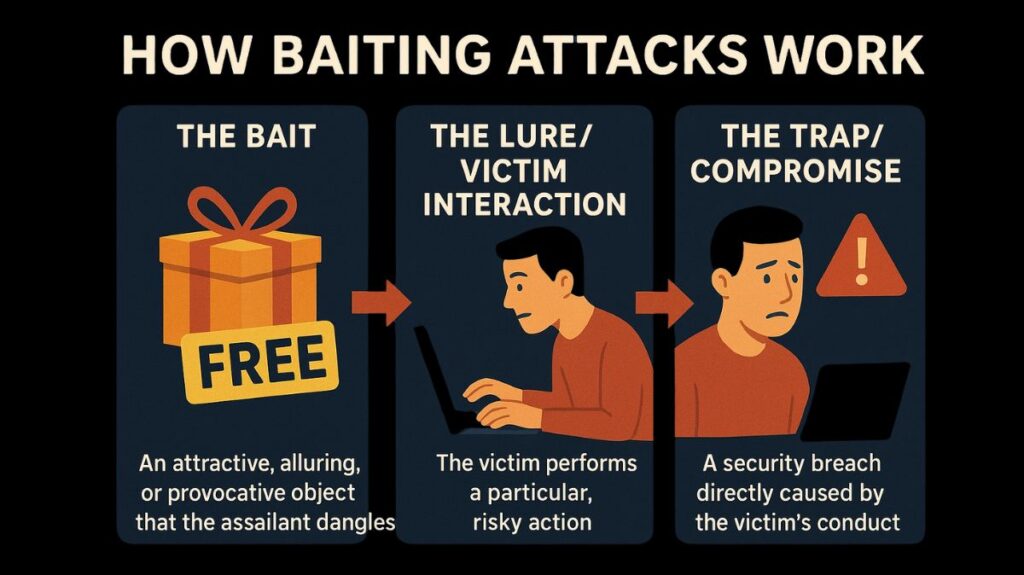
The fundamentals of a baiting attack are based on a straightforward formula intended to persuade the victim to act:
The Bait: The bait is an attractive, alluring, or provocative object that the assailant dangles to get the victim’s attention. Digital (like a free download) or physical (like a USB disc) formats are both possible.
The Lure/Victim Interaction: Attracted by the bait’s apparent worth or intrigue, the victim performs a particular, risky action, like clicking a link, downloading a file, or plugging in a gadget. In order to coerce the victim into acting hastily and ignoring warning indications, attackers frequently use urgency and scarcity.
The Trap/Compromise: A security breach is directly caused by the victim’s conduct, which may lead to the installation of malware, the gathering of login credentials, or the theft of private information. The unsuspecting prey actively facilitates the malevolent behaviour by deliberately choosing to bite the bait.
You can also read Examples of Social Engineering Attacks And How it Works
Common Forms of Baiting Attacks
Digital platforms such as the internet or physical objects can be used to disseminate baiting attack.
Digital Baiting
This type is the most prevalent and frequently appears online. Some examples are as follows:
“Free” Downloads: Attackers give out valuable goods that would typically cost money, like software, games, music, and movies. When the consumer clicks on the link, they are either taken to a fraudulent website or the download itself contains malware, such ransomware or Trojan horses that steal information.
Giveaways and Contests: An email or pop-up advertisement offers a reward (such as a free iPhone, gift card, or special offer) to the user who answers a survey, gives personal information, or “claims” the prize. Identity theft or other attacks are then carried out using this information that has been acquired.
Fake Alerts: Often masquerading as a system alert or antivirus warning, a pop-up window makes a fraudulent claim that the machine is infected. In reality, it installs malware on the system by pressuring the user to click a button that will “clean” the virus.
Clickbait: entices visitors to divulge credentials or download malware by using attention-grabbing headlines or advertisements that frequently make sensational claims or offer “one simple trick” or free information.
Physical Baiting
This technique tricks a victim by using a physical object, frequently using curiosity to make sure the victim uses the object.
Infected USB Drives/CDs: One well-known example is leaving external devices, such as USB drives infected with malware, in public places like a café, lobby, or parking lot. To lure an employee into plugging the disc into their computer, it may be labelled with an alluring title like “Confidential Employee Salaries,” “Payroll Data,” or “Customer Data Backup,” which will cause malware to be installed automatically. Sometimes, this kind of attack is called “evil maid” when the target is purposefully given physical media.
Malicious QR Codes: An attacker covers a genuine QR code sticker (such one on a menu or flyer) with a malicious one. When the victim scans the code, they are taken to a fraudulent website that is intended to steal their financial or personal data.
Targeted Baiting
Spear baiting attack is the use of baiting strategies designed for particular users or groups. Attackers personalize lures by conducting reconnaissance beforehand, which makes them incredibly realistic. The promise of financial advantage, such as a reward for finishing a work promptly, may serve as the bait in these situations.
You can also read How Does Voice Phishing Work And Common Vishing Scenarios
Prevention and Protection
Maintaining a security-conscious culture is essential for both individuals and organizations to prevent falling prey to baiting attack:
Skepticism: Offers that look too good to be true should raise suspicions, particularly if they promise free, premium, or expensive things.
Device Handling: Never connect an external device or USB drive that you are not familiar with to your computer. If anything is discovered, either leave it or provide it to the appropriate authorities.
Link Verification: To verify the destination URL, move your mouse pointer over a link in an email or advertisement before clicking on it.
Software Protection: Use robust and frequently updated antimalware and antivirus software to find and stop malicious programs.
Training and Education: Being aware is essential. In addition to conducting frequent awareness campaigns and simulated baiting attack tests (such as testing staff awareness with innocuous USBs), organizations should train staff members on baiting attack techniques.
Trusted Sources: Use only official websites or stores to download media, music, or software.
You can also read SMS Phishing Tutorial: SMS Phishing Detection And Defense
