Quid Pro Quo Attack
“Quid Pro Quo” indicates “something for something” in Latin. A Quid Pro Quo attack, as used in social engineering and cybersecurity, is a crafty and dishonest tactic in which the attacker offers a service, advantage, or reward in return for important data, access, or particular behaviours from the victim.
The attack’s overtly transactional character the attacker demands something of value from the victim in exchange for a promise to give them something defines it. The psychological principle of reciprocity, which states that people have a social duty to accept an offer or return a courtesy, is exploited.
You can also read What is Reconnaissance Attack, How it Works, History & Types
How Quid Pro Quo Attacks Work?
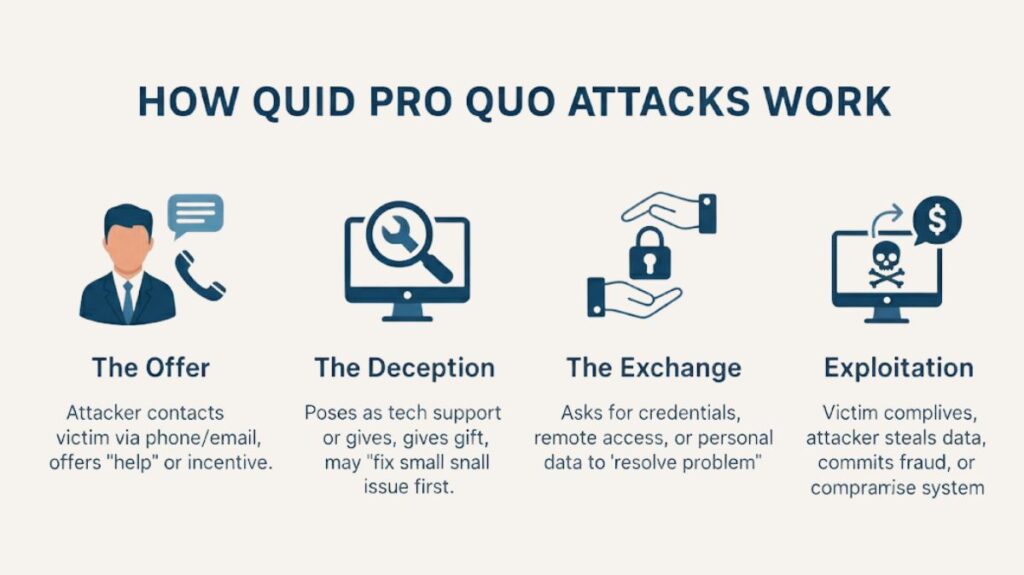
These cyberattacks take advantage of people’s confidence and need for fast repairs. There are usually multiple steps in the process:
The Offer: The attacker makes contact, usually via phone, email, social media, or even in person, and prepares an offer, such as insider benefits, discounts, or tech support.
The Deception: Typically, the attacker poses as someone who can fix a serious problem with the victim’s device or account (e.g., promise to remove malware, speed up a computer, or unlock a disabled account). As an alternative, they might give away a gift card or other incentive. To gain trust, the attacker may even fix a little issue first before requesting something more significant.
The Exchange: In order to fulfil the promise or “fix” the issue, the attacker asks for anything that is required to do the task. Typically, these include of login credentials, remote access to the victim’s device, or private data such as financial information or a Social Insurance number.
Exploitation: The victim obeys because they think they are getting a useful service. The attacker then utilises the information or access they have obtained for fraud, identity theft, more infiltration, or system compromise.
You can also read Email Phishing Attacks, Why Do Hackers Use Phishing Emails?
Common Forms of Quid Pro Quo Attacks
Quid Pro Quo Attack can take many typical forms:
Fake IT Support Calls: Among the most common examples is this one. Posing as helpdesk or IT support employees, an attacker claims that suspicious behaviour was found. They offer to “fix” the purported technical problem, but in order to do so, they need the employee’s login information in order to apply a patch. A real-life example was when a staff member gave a caller (who was pretending to be a technician) remote access to their computer in order to “fix” a problem that didn’t exist. This gave the criminal permission to install malware and steal login credentials for the bank.
Surveys with Incentives: Attackers pose as survey takers and offer participants a gift card or cash reward. The incentive requires victims to divulge a great deal of personal information, such as login credentials, Social Security numbers, or banking information.
Job Offers/Interviews: In return for private or confidential company documents, such passports, attackers offer job chances.
Discounted Services: In order to “activate” the freebie or gain access to the discounted goods, attackers pretend to be companies giving software upgrades or free trials, but they need credentials.
Consequences and Risks
The repercussions of being the target of a Quid Pro Quo attack might be dire:
Data Breach: Passwords, financial information, and private papers are among the sensitive material that attackers take.
Malware Installation: Malware can be installed to monitor behaviour, continuously steal data, or initiate further network attacks once it has control of the device.
Financial Loss: Identity theft, fraudulent transactions, and financial consequences are frequently the results of stolen credentials.
Compromised Systems: The attacker can distribute malware throughout a wider network or launch other attacks using the victim’s device.
You can also read Difference Between DoS Vs DDoS Attack, Types & Advantages
Quid Pro Quo vs. Other Social Engineering Attacks
Unlike other social engineering strategies, Quid Pro Quo Attack has a unique transactional structure.
Quid Pro Quo Attack Vs. Phishing: To put pressure on victims, phishing frequently uses creating a sense of urgency or anxiety (e.g., “Your account is locked!”). Conversely, Quid Pro Quo Attack employs a positive enticement by providing a useful service or benefit.
Quid Pro Quo Attack Vs. Baiting: Baiting frequently employs a passive lure, like a USB drive loaded with malware that is left for a victim to discover out of curiosity. More direct communication and an explicit transaction are features of Quid Pro Quo Attack (“I’ll do X for you if you give me Y”).
Quid Pro Quo Attack Vs. Pretexting: In order to obtain information, pretexting focusses on creating a thorough, credible story; it does not always provide a straightforward, transactional “something in return.”
Protection and Red Flags
Vigilance is necessary to prevent these attacks. Important red flags to look out for are:
- Unsolicited Contact: Real help won’t contact you about a problem without your permission.
- Urgency and Fear: To get victims to act without thinking, attackers frequently instill a sense of urgency.
- Request for Sensitive Information: Authentic IT help won’t request your Social Insurance number, passwords, PINs, access codes, or login credentials.
- Offers That Sound “Too Good to Be True”.
Individuals are advised never to share login details, even with those claiming to be IT staff, and to independently verify identities by hanging up and calling the official department back using a verified phone number. Enabling Multi-Factor Authentication (MFA) is also critical, as it adds a layer of defense even if an attacker obtains a password.
You can also read What Is Spear Phishing Attack? Phishing Vs Spear Phishing
