What is Scareware Attack?
A form of malware or social engineering attack known as “scareware” tricked people into downloading harmful software, paying for fake services, or disclosing personal information by inciting fear. The purpose of scareware, which frequently takes the form of urgent pop-up alerts about viruses or system risks, is to incite fear in users so they would click on links or purchase phoney antivirus software that can infect their devices, steal data, or even install ransomware.
Core Definition and Goal
Scareware creates shock, fear, or a sense of danger by using social engineering techniques. Falsely stating that the user’s device has a serious virus, has substantial faults, or is experiencing a significant security breach plays on their sense of urgency and panic.
Scareware’s principal goal is to direct consumers into:
- Purchasing phoney or ineffective software, frequently marketed as an antivirus solution.
- Downloading several malicious software packages, some of which may be packaged as the phoney solution.
- Accessing websites that are infected by malware.
- Exposing credit card or personal data, which might result in identity theft.
You can also read Clone Phishing Definition And How To Prevent Clone Phishing
How does Scareware Work
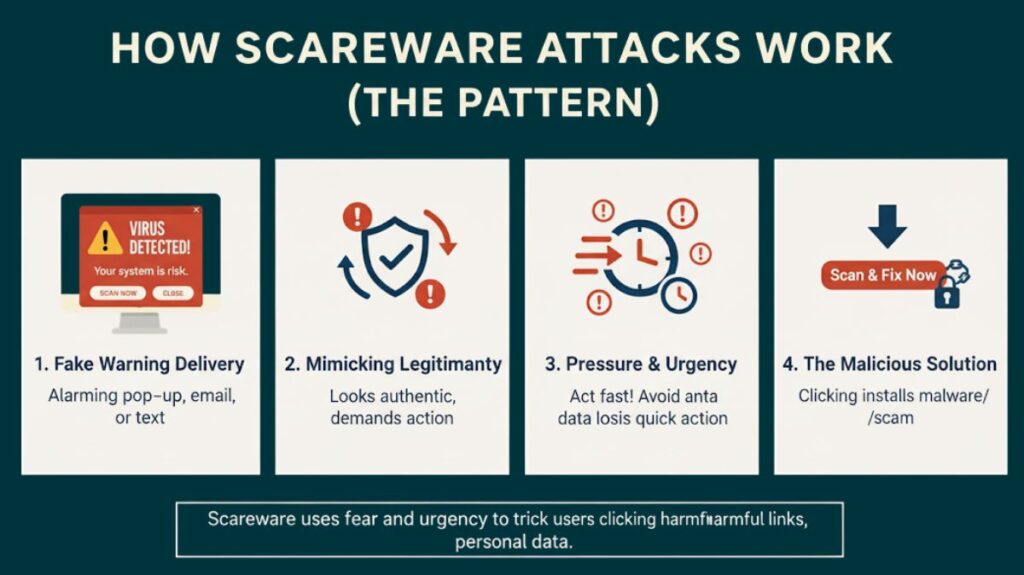
Typically, scareware attacks follow a distinct pattern that mostly uses psychological manipulation:
Fake Warning Delivery: A message, usually an unsettling pop-up warning when online, but also spam emails or spoof texts, is frequently the first indication that a fraud is underway.
Mimicking Legitimacy: The alerts are made to appear as authentic security notifications from antivirus software or the operating system of the device. Their strategies include:
- Copying the names and logos of legitimate antivirus software products.
- Displaying the PC being “scanned” or a progress bar with a screenshot of “infected” files.
- Using strong imagery, such as exclamation points, CAPS, and flashing red pictures, to elicit panic and visceral reactions.
- Using product names and URLs that seem reliable, such “Windows Fixer.”
Pressure and Urgency: The alerts exhort the user to take quick action in order to avoid identity theft, data loss, or system failure. This sense of urgency is intended to promote rash, impulsive actions.
The Malicious Solution: The user is presented with a button such as “Protect Now!” “Download,” or “remove all threats.” A number of things happen if the user complies:
- They are taken to a phoney website where they purchase phoney security software.
- They install the phoney antivirus program, which is essentially malware (a Trojan horse) designed to steal personal information.
- When they input their credit card information, identity fraud and theft may result.
Importantly, some hackers create pop-up windows in such a way that hitting the “Close” or “X” button should actually start a secret drive-by download, infecting the device regardless.
You can also read Examples of Social Engineering Attacks And How it Works
Distribution Methods and Examples
A system can become infected with scareware in a number of ways:
Pop-up Ads/Websites: In one prevalent form, a pop-up or advertisement on a scareware website which is occasionally advertised on social media passes for an antivirus warning.
Malvertising: Phoney antivirus software offered by malicious advertising that is inserted into genuine ad space, such as Facebook or Google search results.
Scareware Emails: Spoofing a sender address in an effort to fool users into providing their access information or clicking on a download link in urgent messages.
Vulnerabilities: Using unpatched vulnerabilities in operating systems, apps, or out-of-date software to download malicious code.
Applications that employ names that sound authentic and replicate user interface components from genuine programs are common instances of scareware. PC Protector, Mac Defender, SpySheriff, XPAntivirus/AntivirusXP, ErrorSafe, Antivirus360, DriveCleaner, WinFixer, and WinAntivirus are a few historical instances of phoney antivirus/anti-malware programs.
Although “scareware” is not specifically malicious software, it can also refer to tech support scams in which the perpetrator cold calls or uses a pop-up to get the victim to call, then convinces them to authorize remote access by saying that suspicious behaviour was linked to their computer.
You can also read How Does Voice Phishing Work And Common Vishing Scenarios
Connection to Ransomware
These days, ransomware and other more serious cyberthreats use scareware tactics as a vector. Hackers obtain an easier path to network compromise than breaking in by tricking users into downloading phoney antivirus software. As ransomware, certain scareware programs either make the device unusable by flooding the screen with incessant warnings that won’t stop unless the user pays to “upgrade” the software, or they hold the contents of the hard drive hostage until a ransom is paid.
Identifying and Preventing Scareware
Signs that a virus alert is fake (i.e., scareware) include:
- All-caps text and exclamation marks are frequently used in the numerous, constant notifications or banners that display on the screen.
- Unforeseen problems with the computer, such as freezing, crashing, or slowing down.
- Unfamiliar apps, toolbars, desktop icons, or a new browser homepage that appears out of the blue.
- Unexpected error messages caused by the inability to access specific applications or files.
- Since trustworthy antivirus software providers don’t employ scare tactics to collect data or force downloads, the warning’s dramatic, malevolent, or threatening tone and need for quick action are concerning.
Protection against scareware involves practicing good cyber hygiene, such as:
- Avoid Clicking Notifications: Avoid clicking on any dubious pop-up, banner, or window that alerts you to a computer infection and requests a download.
- Closing the Window Safely: To terminate a scareware pop-up, close the entire browser window instead of trying to click the “Close” or “X” buttons. On Windows, users can use Ctrl + Alt + Delete to open the Task Manager, find the program under the Applications tab, and click End Task.
- Use Security Tools: Turn on firewalls, pop-up blockers, URL filters, and reliable, current antivirus software.
- Verify Software: Install programs and software only from reliable or official websites. Do a web search to confirm the name of any new program before downloading or buying it.
- Updates: Update all security software, operating systems, and web browsers to fix vulnerabilities.
You can also read SMS Phishing Tutorial: SMS Phishing Detection And Defense
