Wireless principles
The CCNA’s wireless principles course covers basic ideas such as radio frequencies (RF), the 802.11 standard, and the behavior of wireless transmissions. Wireless frequency bands (e.g., 2.4 GHz and 5 GHz), channels, and SSIDs (network names) are important subjects. Security procedures and interference reduction are also covered. The use of radio frequencies (RF) for data transmission, the established standards that regulate this transmission, the specialized components that construct the network, and the essential security measures required to protect data transmitted over the open air are all central to the fundamentals of wireless networks and security.
You can also read What is Wireless Wide Area Network WWAN Key Components
Radio Frequency (RF) Fundamentals and Standards
Radio Frequency (RF) transmissions are electromagnetic waves that move through free space and are used in wireless communication. Antennas are used by devices to transform electrical signals into radio frequency (RF) signals for transmission and vice versa.
Standards and Frequency Bands
IEEE 802.11 is a family of standards that defines Wireless Local-Area Networks (WLANs), or Wi-Fi. Products are certified by the Wi-Fi Alliance to comply with the 802.11 standard.
WLANs primarily operate in two frequency bands, both part of the microwave category of the RF spectrum:
| Frequency Band | Characteristics | Usage |
|---|---|---|
| 2.4 GHz Band | Provides greater range. More susceptible to interference because it is unregulated and shared with other appliances (like Bluetooth and microwaves). | Used by older standards (e.g., 802.11b and 802.11g). |
| 5 GHz Band | Offers less interference and higher throughput/speed. Has a shorter range than 2.4 GHz. | Used by standards like 802.11a. |
Nonoverlapping Wi-Fi channels
These frequency bands are separated into distinct channels (particular frequency ranges) in order to reduce interference.
Wi-Fi channels that don’t interfere with one another are known as non-overlapping channels, which enable several networks to function concurrently. The three non-overlapping channels in the 2.4 GHz frequency are 1, 6, and 11. Because the 5 GHz and 6 GHz bands are substantially wider, there are more non-overlapping channels available, increasing network construction flexibility and lowering congestion.
2.4 GHz band
- In most countries, the 2.4 GHz band has 11 viable channels, albeit they all partially overlap.
- Only channels 1, 6, and 11 are sufficiently enough apart to prevent interference with one another.
- To reduce interference with nearby networks, it is recommended to select one of these three channels if you must use the 2.4 GHz spectrum.
Since 1, 6, and 11 skip four channels between one another, their frequencies do not overlap, enabling them to function concurrently without tainting one another’s signals.
5 GHz and 6 GHz bands
- Compared to the 2.4 GHz band, the 5 GHz and 6 GHz bands are substantially wider, offering more channels that are sufficiently far apart in frequency to avoid overlap.
- Finding a clear channel is made easier by the abundance of non-overlapping channels in the 5 GHz and 6 GHz bands.
- These bands are less crowded than the 2.4 GHz range and are typically suitable for high-speed data.
The Importance of Non-Overlapping Channels
Using non-overlapping channels is crucial for mitigating Adjacent-Channel Interference (ACI), which is far more harmful than Co-Channel Interference (CCI).
| Interference Type | Description | Impact on Performance |
| Adjacent-Channel Interference (ACI) | Networks are using overlapping channels (e.g., Channels 1 and 2). Devices on one network cannot properly detect the transmission of a device on a partially overlapping channel. | Leads to corrupted data, constant retransmissions, and major performance degradation. This is the worst type of interference. |
| Co-Channel Interference (CCI) | Networks are using the same non-overlapping channel (e.g., Channels 1 and 1). Devices can “hear” each other and use a mechanism called CSMA/CA to politely take turns transmitting. | Reduces available airtime, causing slower performance, but the network remains functional and data is not corrupted. |
You can also read How Data Encryption Standard Works and Key Characteristics
Signal Propagation and RF Effects
Wireless signals don’t always travel in a straight line and are influenced by external influences. Signal quality can be affected by the following factors:
- Attenuation: The decline of signal strength with distance.
- Reflection: Reflection is the bouncing of signals off of hard surfaces like glass or metal.
- Absorption: When signals travel through surfaces like walls or ceilings, they diminish (be absorbed).
- Scattering: Signal dispersion that happens when a signal strikes uneven or rough surfaces, such dust or carpets, is known as scattering.
- Diffraction: Signals that bend around sharp edges or objects are known as diffraction.
- Refraction: Refraction is the bending of a signal as it travels through various materials, such water or glass.
Wireless Network Components and Operation
Core Components
- Access Points (APs): Devices that link wireless clients to the wired network backbone are known as access points, or APs. Within its coverage area, referred to as the Basic Service Area (BSA) or Cell, an AP serves as a bridge to the wired network and offers wireless service.
- SSID (Service Set Identifier): Clients utilize the human-readable network name known as the Service Set Identifier (SSID) to locate and establish a connection to the wireless network. In order to provide services like a distinct Corporate Network and Guest Network, APs can handle multiple SSIDs (MBSSID).
- Distribution System (DS): The cable infrastructure that links access points (APs) to the larger network, such as Ethernet.
Network Topologies
- Basic Service Set (BSS): A collection of wireless clients served by a single access point is known as a basic service set (BSS). The BSSID, which is the MAC address of the AP, is what gives the BSS its unique identity.
- Extended Service Set (ESS): A network made up of two or more APs (BSSs) connected via a wired Distribution System (DS) is known as an Extended Service Set (ESS). Because all of the APs in an ESS have the same SSID, clients can move freely between AP coverage regions (cells) without losing connectivity.
- Independent Basic Service Set (IBSS): Also referred to as Ad Hoc Mode, this architecture enables direct communication between wireless clients without the need for an AP. IBSS networks don’t scale well and are typically insecure.
Contention Management
Only one device can communicate on the channel at a time when WLANs are in half duplex mode. Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) is a technology used by wireless devices to control access to shared media and avoid simultaneous transmissions.
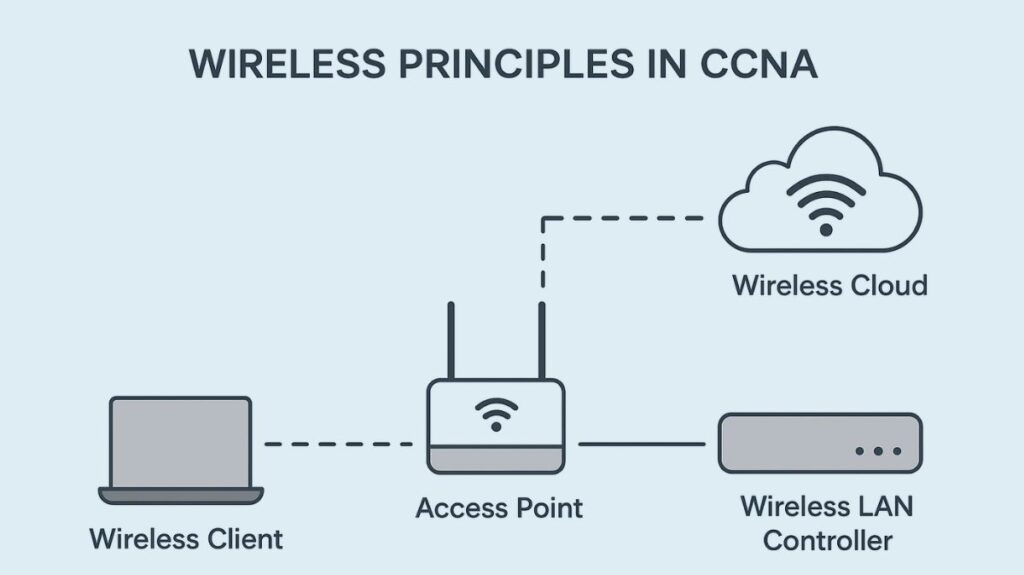
Cisco Wireless Architecture
Networks in big enterprise settings frequently use a Wireless LAN Controller (WLC) as part of a centralized management system.
- Lightweight APs (LWAPs), which are under the supervision of the WLC, use the CAPWAP tunneling protocol to connect to the controller.
- Management features like dynamic channel assignment, RF monitoring, and flexible client roaming are centralized by the WLC. This method is referred to as a split-MAC architecture since AP functions are split between the AP and the WLC.
Wireless Security Principles
Since data is sent over the air, it is possible for anyone in the vicinity to intercept transmissions, making wireless networks intrinsically susceptible. Strong security is therefore required, with an emphasis on encryption (preserving the confidentiality and integrity of data) and authentication (identifying people and devices).
Wireless Security Protocols
Wireless data is now better protected because to evolving security protocols:
- WEP (Wired Equivalent Privacy): The antiquated and unsafe WEP (Wired Equivalent Privacy) protocol is no longer advised.
- WPA (Wi-Fi Protected Access): Although it is currently regarded as fragile, WPA (Wi-Fi Protected Access) is an upgrade over WEP and frequently uses TKIP.
- WPA2: Based on the 802.11i standard, WPA2 is a popular and safe standard. WPA2 supports two modes: 802.1x (Enterprise mode) and PSK (Pre-Shared Key/Personal mode), and it typically employs AES encryption (via CCMP). One fundamental skill is the ability to set up a WLAN utilizing WPA2 PSK.
- WPA3: The most recent standard, which was unveiled in 2018, offers improved security features. For password-based authentication, WPA3 employs the Simultaneous Authentication of Equals (SAE) technique and stronger encryption (GCMP), which offers superior defense against brute-force assaults. Additionally, WPA3 improves user privacy on open public Wi-Fi hotspots.
Advanced security methods include centralized administration platforms like Cisco Identity Services Engine (ISE) and 802.1X authentication, which offers port-based authentication frequently using a RADIUS server. To protect the network, Wireless Intrusion Prevention Systems (WIPS) and rogue AP detection are also used.
You can also read Define Secure Socket Layer and How Does SSL Protocol Work
