Wi-Fi Protected Access 3 (WPA3), WPA3 History, Security Improvements, WPA3 Operational Modes, WPA3 and New Wi-Fi Standards, Compatibility and Migration, and WPA2 or WPA3 were all covered in this blog.
What is WPA3?

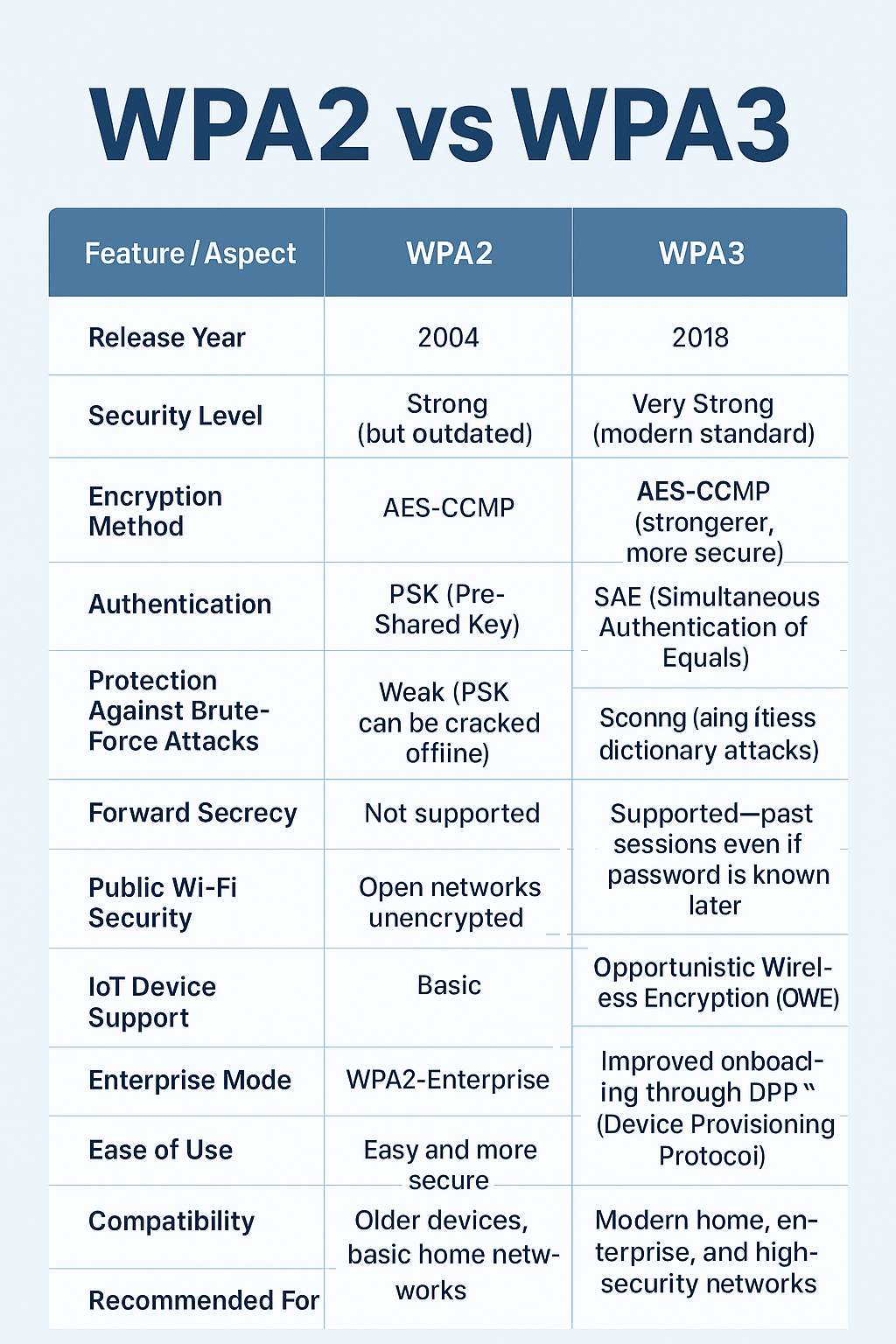
The Wi-Fi Alliance created the most recent Wi-Fi security standard, WPA3 (Wi-Fi Protected Access 3), to offer more robust security than (Wi-Fi Protected Access 2) WPA2. Through stronger authentication procedures, more secure encryption, and more defence against frequent assaults like brute-force guessing particularly on public networks it improves cybersecurity. Important innovations include a new standard for open networks that encrypts user traffic and Simultaneous Authentication of Equals (SAE), which substitutes the WPA2 pre-shared key to improve security against weak passwords.
WPA3 History
The Wi-Fi Alliance created the most recent version of the Wi-Fi security protocol, known as WPA3 (Wi-Fi Protected Access 3), with the goal of replacing and improving WPA2. WPA3 was introduced in 2018 with the goal of strengthening and enhancing security, addressing identified flaws in WPA2, and making safe communication easier for consumers.
By shielding users from typical threats like brute-force password guessing, passive spying, and session hijacking, WPA3 dramatically improves the security baseline of Wi-Fi networks. WPA3 capability has been required for devices bearing the “Wi-Fi CERTIFIED” logo from July 2020. Additionally, it is a necessity for security for any devices using the 6 GHz band (Wi-Fi 6E and Wi-Fi 7).
Also Read About What Is Wi-Fi Eavesdropping, The Threat Of Network Snooping?
Security Improvements
Compared to its predecessors, WPA3 offers a number of significant cryptographic advancements and security measures.
Simultaneous Authentication of Equals (SAE)
The Simultaneous Authentication of Equals (SAE) protocol is used in WPA3-Personal to replace the outdated Pre-Shared Key (PSK) authentication scheme and the weak 4-way handshake of WPA2-Personal.
Protection from attacks: By requiring network interaction upon login, SAE, also referred to as the Dragonfly handshake, fortifies the key exchange and stops hackers from downloading a cryptographic hash and using offline cracking software (offline dictionary and brute-force attacks), even when weak passwords are used. The PSK is never revealed while using SAE.
SAE Methods: Hunting and Pecking (HnP) and Hash-to-Element (H2E) are the two sub-methods used by WPA3-Personal to derive the Password Element. Due to HnP’s vulnerability to dictionary attacks, H2E is required for Wi-Fi 6E (6 GHz) and Wi-Fi 7.
Forward Secrecy
Forward secrecy is provided by WPA3. This crucial feature protects historical data by guaranteeing that previously encrypted messages cannot be decoded, even in the event that a session key or password is later compromised.
Stronger Cryptography and PMF
WPA3 often requires the use of contemporary encryption techniques. Based on Advanced Encryption Standard (AES) counter mode encryption, WPA3 employs the Galois/Counter Mode Protocol (GCMP), which incorporates the Galois Message Authentication Code (GMAC) for integrity verification. WPA3 does not permit TKIP.
Protected Management Frames (PMF): Required in WPA3 connections, PMF is defined in the IEEE 802.11w amendment. By securing important 802.11 management frames between clients and Access Points (APs), PMF helps stop unwanted activity including spoofing and network operation manipulation.
WPA3 Operational Modes
WPA3 functions in multiple modes that are specific to various network environments:
WPA3-Personal
In order to fix vulnerabilities in WPA2-Personal, particularly the possibility of dictionary attacks against the pre-shared key (PSK), WPA3-Personal includes key upgrades.
Authentication Method: Simultaneous Authentication of Equals (SAE) is used in place of PSK authentication.
- The Dragonfly handshake is another name for SAE.
- In the IEEE 802.11-2016 standard, SAE is described.
- By requiring network contact during login, SAE fortifies the key exchange and stops hackers from downloading a cryptographic hash and using offline cracking software (dictionary assaults).
- Since the PSK is never revealed with SAE, a threat actor cannot predict.
Forward Secrecy: This feature is introduced by WPA3-Personal. By using this key exchange technique, attackers are unable to decrypt data that has already been sent over the air using a compromised password or key.
Also Read About What Is The Wired Equivalent Privacy WEP And How It Works
WPA3-Enterprise
WPA3-Enterprise is intended for networks that need to be extremely secure.
Authentication Method: 802.1X/EAP authentication is still used.
Cryptographic Suite: It forbids combining security protocols from earlier standards and necessitates the deployment of a 192-bit cryptographic suite.
- In high-security Wi-Fi networks, this complies with the Commercial National Security Algorithm (CNSA) suite.
- WPA3-Enterprise uses a 192-bit security mode and the appropriate set of cryptographic techniques to guarantee a constant baseline of security.
- Particular cryptographic techniques include 256-bit BIP-GMAC-256 for strong management frame protection, 384-bit HMAC-SHA384 for key derivation, and 256-bit GCMP-256 for authenticated encryption.
Open Networks (Public Wi-Fi)
Public Wi-Fi networks that usually use open authentication, in which user traffic is sent as unauthenticated plaintext, present security issues that WPA3 attempts to mitigate.
- WPA3 utilizes Opportunistic Wireless Encryption (OWE) to encrypt all wireless traffic on public or open Wi-Fi networks that do not employ authentication systems.
- By assigning each device on the network a unique key, OWE offers Individualized Data Protection (IDP), which prevents an attacker from accessing other encrypted data even if they manage to get the network password (assuming one exists).
Alos Read About Cisco SNMPv3 Configuration, SNMPv3 security and components
WPA3 and New Wi-Fi Standards
Newer Wi-Fi protocols require WPA3:
- Wi-Fi 6E (6 GHz): WPA2 is expressly prohibited, and WPA3 is required for any Wi-Fi 6E devices using the 6 GHz band. For 6 GHz operation, PMF is required.
- Wi-Fi 7: In order to support features like Multi Link Operation and 802.11be data speeds, all Wi-Fi 7 devices must support WPA3. Certain high-security cyphers, such as GCMP256, are necessary for Wi-Fi 7.
Compatibility and Migration
Despite its many benefits, WPA3 is not widely adopted.
Backward Compatibility: Hardware or firmware modifications may be necessary for older devices that do not support WPA3.
Transition Mode: Networks may support both contemporary WPA3 clients and legacy WPA2 devices thanks to the WPA2/WPA3 Transition Mode.
Transition prohibit: By instructing WPA3 Stations (STAs) to prohibit specific transition modes for upcoming connections, APs can prevent downgrade attempts by requiring the STA to use WPA3 exclusively. For big networks with a single SSID covering areas with different security settings (e.g., WPA2 only vs. WPA3 transition mode), this feature is generally not advised.
IoT Provisioning: Wi-Fi Easy Connect, which is based on Device Provisioning Protocol, or DPP, is supported by WPA3 and will eventually replace the vulnerable Wi-Fi Protected Setup (WPS). It makes it easier to join headless IoT devices to a network via QR codes or NFC tags.
Also Read About What is Encapsulating Security Payload and How ESP Works
WPA2 or WPA3
WPA3 offers a substantial and crucial security improvement for contemporary Wi-Fi networks, making it unquestionably superior to WPA2. One of WPA3’s main enhancements is the substitution of the more reliable Simultaneous Authentication of Equals (SAE) handshake for the weaker WPA2 Pre-Shared Key (PSK) handshake.
SAE offers powerful defence against offline dictionary attacks, or brute-force password guessing. Furthermore, in order to improve privacy and prevent eavesdropping, WPA3 addresses known security flaws like the KRACK attack that impacted WPA2 by requiring stronger 192-bit encryption in its Enterprise mode and offering customised data encryption for users on public Wi-Fi networks (through Opportunistic Wireless Encryption, or OWE). WPA3 is the most secure protocol and ought to be used anytime all of your network equipment supports it, even if WPA2 is still extensively used and works with older devices.