Explore the various types of routing protocols, from distance-vector to link-state. Understand how these protocols are categorized and their unique roles in directing data across different network topologies.
Networking Routing Protocols
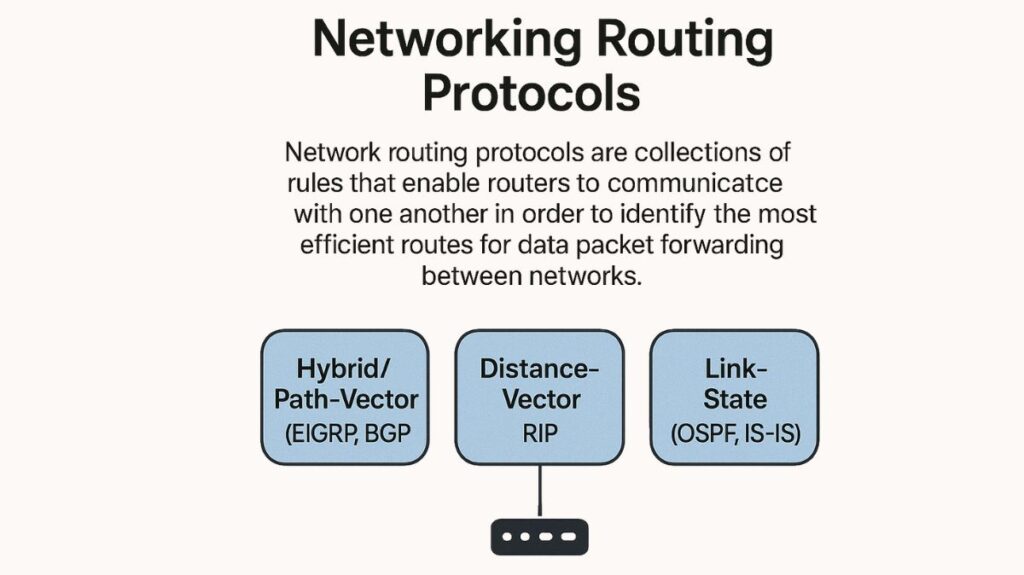
Network routing protocols are collections of rules that enable routers to communicate with one another in order to identify the most efficient routes for data packet forwarding between networks. They are divided into three types: hybrid/path-vector (like EIGRP, BGP), distance-vector (like RIP), and link-state (like OSPF, IS-IS). Each kind uses a different method to determine routes based on metrics like bandwidth, hop count, or topology. These protocols are crucial for dynamic network management because they recalculate routes in response to changing network circumstances, allowing fault tolerance and effective data delivery.
Core Functions and Purpose
Enabling efficient and successful communication between computer networks is the main goal of routing protocols. They make it possible for routers to:
- Use nearby routers to find and learn about distant networks.
- Communicate routing details with other routers.
- Identify the optimal route to each destination network by creating and maintaining a routing table.
- Based on a number of parameters, including bandwidth, latency, and hop count, determine and select the optimal path to each subnet.
- Adjust and update routes dynamically in the event that the network topology changes (for example, a link fails). The fault tolerance and high availability of the Internet are a result of this capability.
Although dynamic routing methods offer scalability and require less administrative overhead than static routing, they do use some of the CPU time and network link capacity of a router.
How Networking Routing Protocols Work
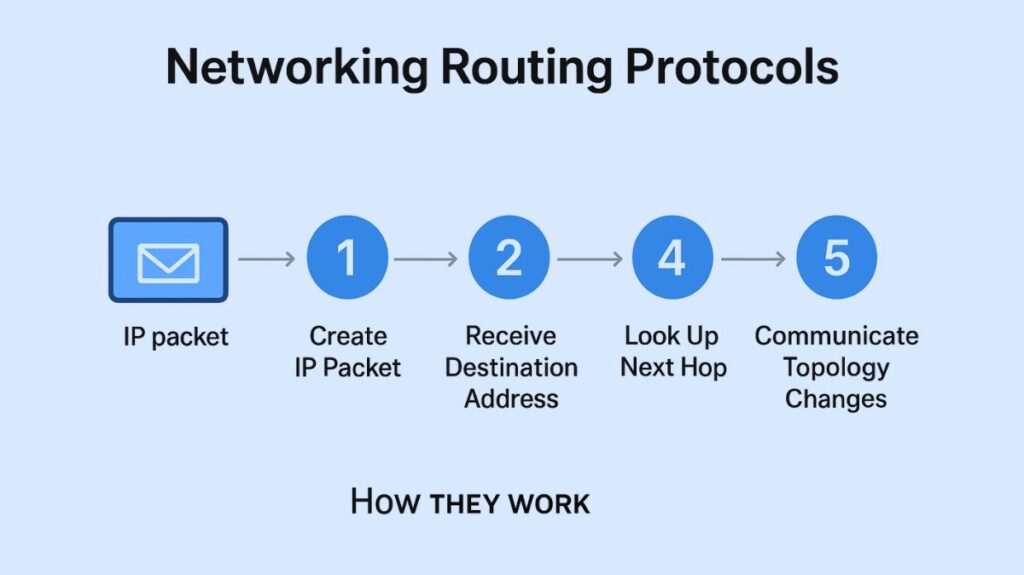
An IP packet is created and transmitted from a source to a destination, where it must travel via several routers. In order to identify the optimal path, routers employ routing protocols by:
- The packet’s destination address being received.
- Looking up the information, price, and other relevant characteristics about the next router in their routing table.
- Choose which router the packet should be forwarded to next by using routing algorithms.
- Learning about remote networks by exchanging data and routing messages with other routers that use the same protocol.
- Communicating to other routers about changes in the topology.
Although various packets may follow different routes, they will all arrive at their destination.
Routing Protocols vs. Routed Protocols
Making a distinction between these two words is crucial:
Routed Protocol: Enables routers to forward packets from one host to another by defining logical addressing and packet formats. AppleTalk, IPX, and IP (IPv4 and IPv6) are a few examples. These protocols transport user information.
Routing Protocol: Enables routers to update their tables, exchange routing data, and eventually allow routed protocol forwarding. They specify guidelines for when, how, and what information should be included in updates as well as how to identify receivers. Routing protocols’ function is to identify the optimal path for data packets, not to transmit them over the network.
Types of Routing Protocols
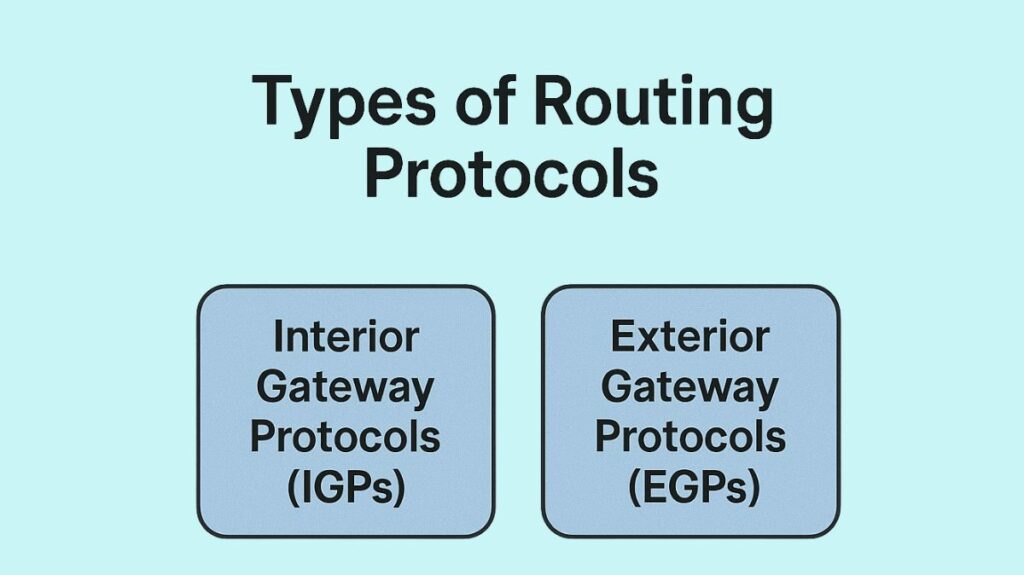
According to their function and method of operation, routing protocols may be generally divided into:
Interior Gateway Protocols (IGPs)
An Autonomous System (AS) is a group of networks under a single administrative domain, and IGPs are used for routing inside an AS. OSPF, IS-IS, RIP, IGRP, and EIGRP are a few examples. IGPs can be further separated into:
Distance Vector Protocols:
- Operation: Based on hop counts the number of routers a packet travels through routers determine the most efficient way to get a packet to its destination in a certain direction. Their neighbours who are directly linked are the only ones with whom they share routing information. Every router keeps track of the shortest path between itself and other routers in a routing table.
- Features: Only nearby nodes are given access to the updates, which are provided on a periodic basis. Only the distance vector is provided in updates; complete routing tables are not. Routers rely on neighbouring routing information, or “routing rumours.”
- Algorithm: They frequently calculate distance using the Bellman-Ford technique.
- Advantages: They are easy to use and configure, consume little CPU and memory, adapt to changes in the network automatically, and function effectively in small networks.
- Disadvantages: Restricted scalability for big networks, slow convergence (it takes time to update routes after a network change), the potential for increased bandwidth consumption owing to frequent updates, and the possibility that routes are not always the best. The “count-to-infinity” issue and routing loops are likely to occur.
Examples:
- Routing Information Protocol (RIP): Has a limit of 15 hops and uses hop count as its measure, which makes it appropriate for smaller networks. RIPv1 is classful, but RIPv2 is classless and compatible with CIDR and VLSM. IPv6 is known as RIPng. RIP uses User Datagram Protocol (UDP) to function.
- Interior Gateway Routing Protocol (IGRP): For big, heterogeneous networks, Cisco created a proprietary protocol that uses several routing characteristics, including bandwidth, latency, dependability, and load. Hold-downs, split horizons, and poison-reverse updates are some of the features it provides to increase stability and avoid routing loops.
Link-State Protocols:
- Operation: Routers exchange information about every network link to create a comprehensive map (topology) of the whole network. All nodes receive information from each router on the cost of accessing its neighbours.
- Features: Use “Hello messages” to find and recover neighbours. Instead of doing full table updates on a regular basis, updates are only performed when the topology changes (triggered updates). We only exchange requested updates.
- Algorithm: The Dijkstra Shortest Path First (SPF) method is used to determine the least expensive routes.
- Tables Used: Keep a table with information about your neighbours, a table with information about the topology as a whole, including backup and best routes, and a table with all of your best routes.
- Advantages: More accurate and optimum routes with a comprehensive network perspective are provided by faster updates and quick adaptability to network changes. These features make them suited for big and complex networks, less likely to experience routing loops, and more dependable.
- Disadvantages: Excessive memory and processing power use, complicated setup and maintenance, and the potential for increased bandwidth utilisation for network updates. Overhead makes this network unsuitable for small networks.
Examples:
- Open Shortest Path First (OSPF): Used in medium- to large-sized networks, this link-state routing protocol is the most widely employed. Both IPv6 and IPv4 are supported by OSPFv3, while OSPFv2 is for IPv4. Hello packets are used to create and preserve neighbour connections. allows for ECMP routing.
- Intermediate System-to-Intermediate System (IS-IS): Integrated IS-IS, also known as Dual IS-IS, was first created for the OSI protocol suite and then later integrated for IP networks. It makes use of an altered Dijkstra algorithm.
Hybrid Protocols:
- Operation: To balance accuracy and efficiency, combine aspects of link-state and distance-vector techniques.
- Advantages: Combines the benefits of both; it is better for bigger networks, updates quickly, uses bandwidth efficiently, and is scalable for both small and large networks.
- Disadvantages: Requires more memory and CPU, can be difficult to set up and maintain, and occasionally has slower or irregular updates.
Example:
- Enhanced Interior Gateway Routing Protocol (EIGRP): Utilizing the DUAL (Diffusing Update method) method, this Cisco-exclusive protocol facilitates route summarization and VLSM. By using the Hello protocol to find neighbours and establish adjacency, it functions as a link-state protocol. It also learns routes from neighbours who are directly linked, acting as a distance-vector protocol. IPv6 is known as EIGRPv6.
Exterior Gateway Protocols (EGPs)
EGPs are used to transmit routing data between various Autonomous Systems (AS), including Internet Service Providers (ISPs).
Path Vector Protocols:
- Operation: Saves the route details needed to get to a destination. They are dynamically updated route vectors.
- Example:
- Border Gateway Protocol (BGP): Often referred to as a path-vector protocol, this is the only EGP that is currently functional and the most widely used on the internet. In addition to providing a wide range of security features, BGP uses an optimum path selection approach for data transfers and lets administrators change routes as needed. In order to replace the outdated EGP protocol, BGP was developed. IPv6 is supported by BGPv6 and MP-BGP4 (Multiprotocol BGP-4).
Key Characteristics and Concepts
Routing Metrics: Routing protocols employ quantitative data to identify the best course of action. Generally speaking, a superior path is indicated by a lower metric value. Typical metrics include dependability (IGRP, EIGRP, OSPF), load, latency, bandwidth, and hop count (RIP).
Administrative Distance (AD): An indicator of how reliable a source of routing information is. When several sources are used to learn alternative routes to the same network, a lower AD value implies a more favoured path.
Classful vs. Classless Protocols:
- Classful: The subnet mask cannot support Variable Length Subnet Masks (VLSM) and should not be included in routing updates. Examples are IGRP and RIPv1.
- Classless: As needed by the majority of contemporary networks, implement VLSM and Classless Inter-Domain Routing (CIDR) and incorporate the subnet mask into routing updates. BGP, OSPF, IS-IS, EIGRP, and RIPv2 are a few examples.
Convergence: Putting all of the routing tables into a uniform condition so that every router in the same routing domain has correct and comprehensive network information. Since faster convergence enables quicker adaptability to network changes, it is often preferred.
Routing Loops: Problems in which packets of data keep moving around without getting to their destination. They are less likely to occur in link-state protocols.
Load Balancing: Also referred to as load sharing or Equal-Cost Multipath (ECMP) routing (e.g., OSPF), dynamic routing technologies can steer traffic along several pathways for improved performance.
Impact on Network Performance
Routing protocols have a major impact on the overall effectiveness, reliability, and user experience of a network. They help networks run more effectively by:
Avoiding excessive bandwidth consumption: In order to avoid overload, networks select routes according to the amount of available bandwidth.
Steering clear of downed devices: They guarantee minimum impact on network performance by offering backup routes to reroute data in the event that a node becomes unavailable.
Enabling quick access to data: The fastest feasible data transmission may be achieved by mapping the ideal path.
Ensuring reliability and fault tolerance: Identifying other routes automatically in the event that linkages fail.
Prioritizing traffic (QoS): Ensuring that crucial information, such as audio or video communications, functions properly.
Security of Routing Protocols
Protecting data integrity, user trust, and network infrastructure all depend on secure routing. Among the ways to protect routing systems are:
Defense Against Network Attacks: Defending against route poisoning, DDoS attacks, and route hijacking.
Prevention of Unauthorized Access: Limiting access to routing choices to authorized devices, usually by using authentication methods (e.g., RIPv2, OSPF).
Preserving Data Integrity: Preventing packets from being altered or intercepted.
Adaptation to Changing Threats: Routinely improving and updating processes.
Compliance Requirements: Complying with legal and corporate requirements.
