Routing Loop
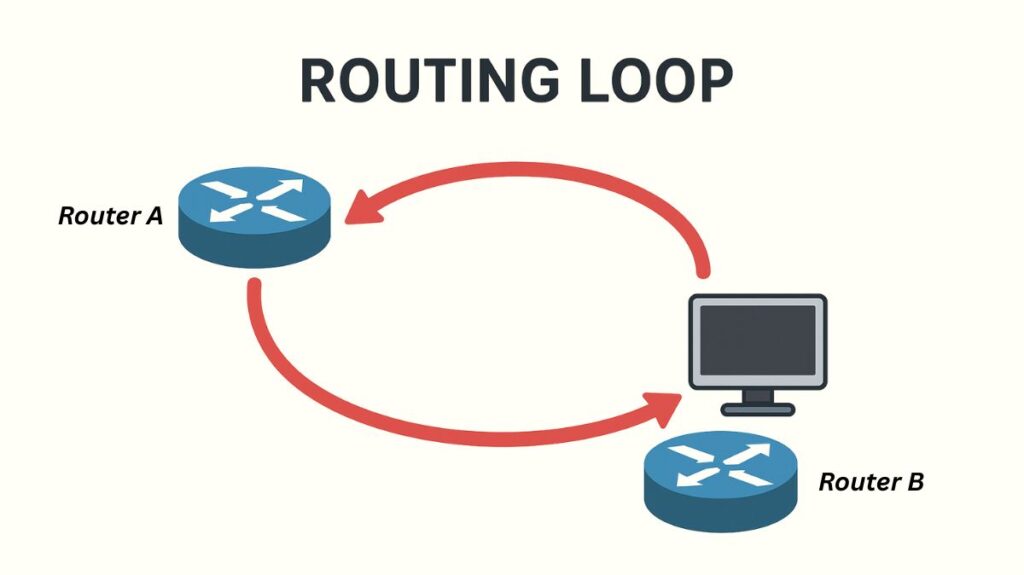
When network packets keep moving back and forth between routers without ever arriving at their destination, this is known as a routing loop. This typically occurs when routing information on routers is inaccurate or inconsistent.
For example:
- Router A believes that Router B offers the best route to a network.
- According to Router B, Router A is the best route.
- Consequently, a packet continues to bounce back and forth.
This can lead to network failures, increase latency, and waste bandwidth.
Routing Loop Prevention
The term “routing loop prevention” describes the collection of methods and procedures employed by routing protocols to halt these interminable packet circulations. In order to stop packets from continuously rotating within a network, routing loop prevention strategies include split horizon, route poisoning, hold-down timers, and counting to infinity. Routing protocols like RIP and OSPF use these techniques to make sure data packets reach their destination and networks stay stable.
You can also read Intermediate System to Intermediate System (IS-IS) Features
How Routing Loop Prevention Works
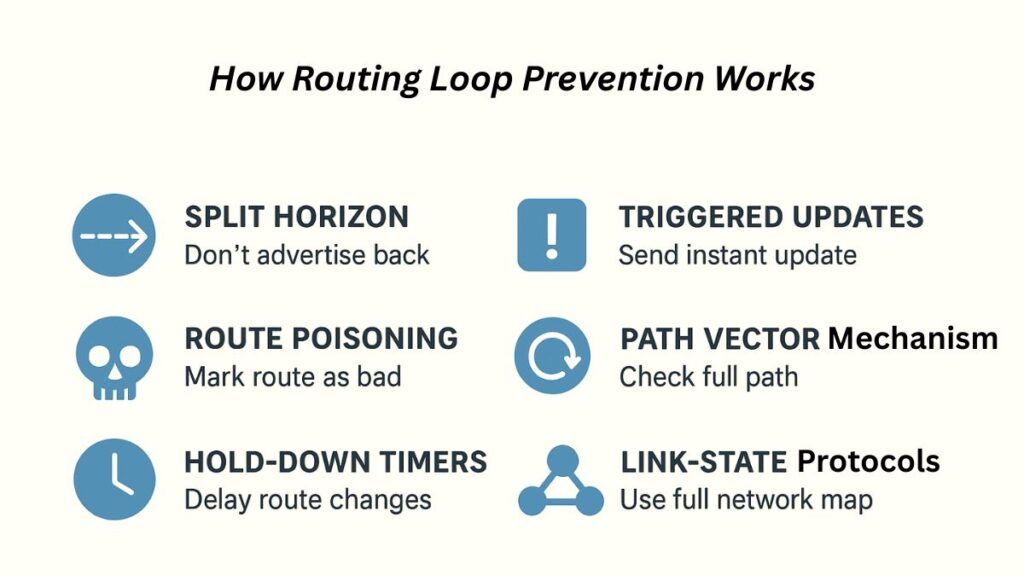
Routing protocols use procedures and guidelines to identify or steer clear of loops before they become established. Crucial methods consist of:
Split Horizon: A route that was learnt in one direction is not advertised by a router in the same direction.
Route Poisoning: An infinite metric is used by a router to broadcast a failed route, alerting all nearby neighbours that the path is no longer viable.
Hold-Down Timers: Prevents routers from accepting inaccurate information too fast by temporarily suppressing updates regarding a failed route.
Triggered Updates: Avoids loops from being caused by out-of-date information by sending instant updates whenever a network change takes place.
Path Vector Mechanism: The full path information is carried by (used in BGP), allowing routers to check for loops by determining whether their own AS number is already present in the path.
Link-State Protocols: Since every router uses the same consistent database, (such as OSPF, IS-IS) create a comprehensive map of the network topology, lowering the possibility of loops.
Benefits of Routing Loop Prevention
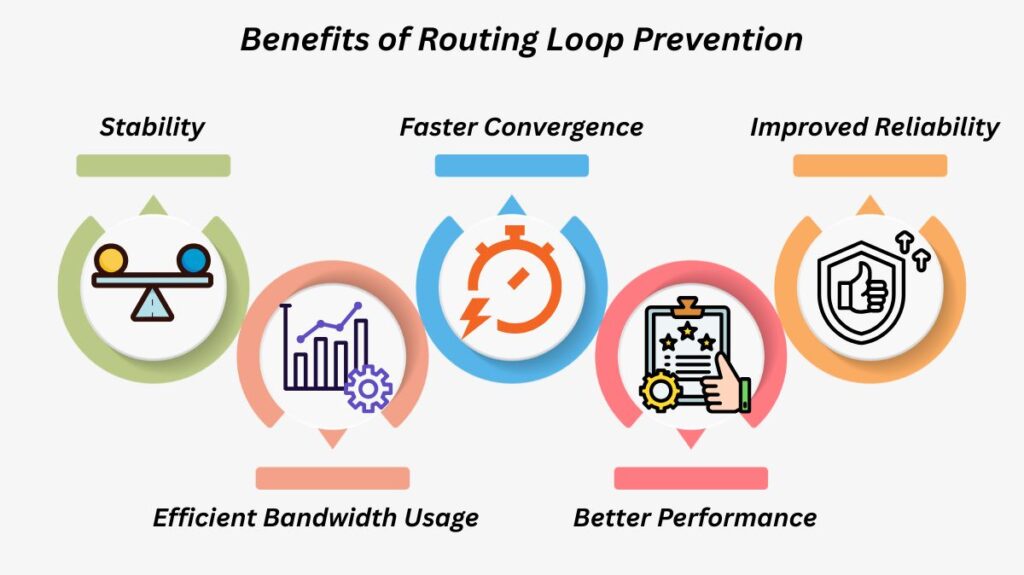
Stability: Stops the unending flow of packets that could cause the network to become unstable.
Efficient Bandwidth Usage: Eliminates bandwidth waste brought on by looping traffic.
Faster Convergence: Makes certain that routing tables are updated accurately and promptly.
Better Performance: Minimizes packet loss, jitter, and latency.
Improved Reliability: Increases the reliability of dynamic routing protocols for important networks.
You can also read Optimized Link State Routing Protocol And Applications
Drawbacks of Routing Loop Prevention
Slower Convergence in Some Cases: Lawful route re-advertising can be delayed by devices like hold-down timers.
Complexity: Some techniques (such as SPF computations or path vectors) demand additional memory and processing power.
Overhead: Additional computations, timers, and updates could use up router resources.
Not Foolproof: Even with safeguards in place, software flaws or misconfigurations can still result in loops.
Types of Routing Loop Prevention Techniques
Distance Vector Protocols (RIP, EIGRP)
- Split Horizon
- Route Poisoning
- Hold-Down Timers
- Triggered Updates
Link-State Protocols (OSPF, IS-IS)
- Topology information is consistently provided by Link-State Advertisements (LSAs).
- To cut down on loops, each router separately determines the shortest path tree.
Path Vector Protocols (BGP)
- Utilizes AS-Path to monitor past routes.
- A router rejects a route in order to prevent loops if it detects its own AS number in the path.
You can also read Static And Default Route Configuration CISCO Differences
Examples
Example 1 – RIP (Distance Vector)
- Through Router B, Router A gains knowledge of Network X.
- Due to an out-of-date entry, Router A also informs Router B about Network X.
- In the absence of split horizon or route poisoning, packets will loop to X.
Example 2 – OSPF (Link-State)
- LSAs throughout the network are inundated by OSPF routers.
- Every router has the same topology map.
- During steady state, routing loops are nearly impossible because the SPF algorithm consistently recalculates the shortest path.
Example 3 – BGP (Path Vector)
- If a route to AS 65002 is advertised by AS 65001, and 65002 forwards it to 65003, then back to 65001:
- Route → loop prevented is discarded by the router in 65001 when it detects its own AS number in the AS-Path.
Real-World Impact
- Major outages can be caused by routing loops in big company or ISP networks.
- For instance, a 2019 BGP upgrade that was improperly implemented resulted in traffic looping and blackholing, which interrupted internet connection worldwide.
- In mission-critical settings including banking, cloud data centres, and telecom networks, effective loop-prevention strategies are essential.
Comparison of Routing Loop Prevention by Protocol
| Protocol | Techniques Used | Effectiveness | Example Use Case |
|---|---|---|---|
| RIP (Distance Vector) | Split Horizon, Route Poisoning, Hold-Down Timers | Moderate – slower convergence, risk of loops during changes | Small LAN/WAN |
| EIGRP (Hybrid) | Diffusing Update Algorithm (DUAL), Split Horizon, Route Poisoning | High – very loop-free and fast | Enterprise Networks |
| OSPF (Link-State) | Link-State Advertisements, SPF Tree | Very High – loops almost eliminated | Large Enterprises, ISPs |
| BGP (Path Vector) | AS-Path Loop Checking, Route Filtering | Very High – designed for Internet-scale | Global Internet Routing |
Key Takeaways
- Loops in routing are bad because they consume bandwidth and cause disruptions.
- Different preventative methods are used in different regimens.
- There is no one ideal approach speed, stability, and overhead must all be balanced.
- As crucial to avoiding loops as protocol techniques is proper configuration.
You can also read Hot Standby Router Protocol, How HSRP Works & Applications
