Network Device Monitoring
In order to guarantee optimal performance, availability, and security, network devices must be continuously observed and analyzed. This is known as network device monitoring, and it is an essential component of operational network management. Predicting future expansion requirements and identifying unforeseen changes in network condition are its goals.
Network device monitoring is the methodical process of gathering, following, and evaluating data from different network elements, including servers, routers, switches, and endpoints. Gaining insight into the operational state, performance, and health of the network is the aim. This procedure falls under the larger management plane of network designs, which is concerned with controlling protocols used for device administration and safeguarding access.
How Network Device Monitoring Works
Dedicated protocols and tools are the main ways that network device monitoring collects information and notifies administrators:
Data Collection Protocols
Simple Network Management Protocol (SNMP): For gathering and modifying network data, SNMP is a popular application layer protocol. It makes it possible for a Network Management Station (NMS) to get warnings and query devices for different parameters. When an SNMP agent (software module) is installed on managed devices (such as servers, routers, and switches), it gathers information about the resources and activities of the device. Variables and their Object IDs (OIDs) are stored in a Management Information Base (MIB), which defines this data.
- SNMP GET requests: The NMS polls agents on a regular basis to obtain certain data.
- SNMP SET messages: SNMP is another tool that the NMS can utilise to set agent parameters.
- SNMP TRAP messages: The NMS receives unsolicited alerts (traps) from agents when important events or thresholds are reached.
Syslog: System messages, or logs, that document events such as interface status changes (up/down), can be produced by network devices. For storage and analysis, these messages can be broadcast to terminal lines (using the terminal monitor command), displayed on the console line (by default), kept in a local buffer, or routed to a centralized Syslog server. In order to correlate events across many devices, timestamps are frequently included in syslog entries.
Network Time Protocol (NTP): Guarantees that the clocks of all network devices are in sync. This is essential for precise timestamping of events and log messages, which allows for appropriate correlation during troubleshooting.
Cisco Discovery Protocol (CDP) and Link Layer Discovery Protocol (LLDP): These Layer 2 protocols assist in locating directly connected network devices and collecting data, including IP addresses, port IDs, device IDs, platform, software version, and router/switch capabilities. They are essential for troubleshooting and documenting networks.
Internet Control Message Protocol (ICMP): To check for delays, path dependability, and basic network connectivity, use the ping and traceroute commands.
Cisco IOS NetFlow: An effective maintenance and monitoring tool that supplements SNMP’s device statistics by reporting on traffic statistics (packets and bytes), consumption, and applications. Denial of Service (DoS) monitoring, network planning, usage-based charging, network traffic accounting, and security are among its applications.
Management Tools and Platforms
Network Management System (NMS): An application that runs on a centralized server regularly polls network devices using SNMP in order to identify devices that are failing, monitor performance metrics (such as CPU load, memory usage, packet loss, and ICMP response times), and graph data over time. Email, SMS, or dashboard alerts (e.g., green for healthy, yellow for difficulties, and red for unreachable) can all be sent by NMS solutions.
Network Configuration Manager (NCM): NCMs, which are frequently combined with an NMS, manage network configurations by regularly backing them up, enabling comparisons, and alerting administrators to modifications. They can even automatically reconfigure devices to enforce optimal setups.
Cisco DNA Center / APIC-EM: Controller-based, contemporary solutions that provide sophisticated network administration and monitoring. They offer plug-and-play installation, QoS setting, application visibility, path tracing, topology mapping, and convergent wired/wireless management apps. For up to a week, DNA Center can take a full network snapshot and provides AI/Big Data insights for troubleshooting.
IT Automation Tools (Ansible, Puppet, Chef): These technologies, which frequently make use of REST APIs and JSON, can automate configuration management, which includes enforcing changes and keeping an eye out for configurations that “drift” from an ideal state.
Firewalls and Intrusion Prevention/Detection Systems (IPS/IDS): To identify whether traffic is authentic or a component of an exploit, these security appliances keep an eye on it while it’s in route. In order to stop assaults, firewalls can filter traffic, while intrusion prevention systems (IPS) can remove harmful messages inline. IDS devices examine traffic copies to identify attacks. They use Syslog and SNMP protocols to provide alarms to monitoring systems.
Wireless AP Monitor Mode: Access points can be set up as specialized sensors to identify rogue access points, monitor for Intrusion Detection System (IDS) events, and use location-based services to pinpoint the locations of stations.
Packet Sniffers/Network Analyzers: Network traffic is captured and thoroughly examined by tools like Wireshark (which is frequently used in AP sniffer mode) in order to identify issues.
CLI Commands: Basic monitoring is often performed directly on devices using show commands (e.g., show ip interface brief, show interfaces, show cdp neighbors, show lldp neighbors, show mac address-table dynamic) for static status information. debug commands provide a “live video camera” feed of router operations and traffic but are high-overhead and meant for short-term troubleshooting.
Network Device Monitoring History
The idea of network monitoring changed as networks became more complicated. The 1988 publication of the first RFCs for the Simple Network Management Protocol (SNMP) marked a significant advancement. Because SNMP breaks down device information into a database of variables (MIBs), it offers a standardised method for managing and monitoring IP-based networks. Later iterations, SNMPv2 and SNMPv3, provide enhanced security and performance. Vendors like Cisco developed proprietary protocols like Cisco Discovery Protocol (CDP) to aid in network discovery; these were eventually supplemented by open standards like LLDP. Monitoring has been revolutionised in more recent years by controller-based networking and network automation technologies, which centralise data and control and allow programmatic interaction with network devices.
Why Network Device Monitoring is Important (Advantages)
There are many advantages to network device monitoring:
Proactive Problem Detection and Troubleshooting: It helps managers to identify issues such as malfunctioning devices, broken communication links, or security risks before they become more serious and affect users. Maintaining a positive user experience and reducing downtime require this skill.
Performance Baselining and Analysis: Administrators can identify bottlenecks (such as excessive CPU load, memory utilization, or packet loss), analyse trends, and set baselines for typical functioning by collecting information over time.
Capacity Planning: In order to handle network growth without requiring significant redesigns, performance data helps forecast future resource requirements and guides network design decisions.
Security: Through traffic and log analysis, monitoring aids in the detection of potential exploits, IDS/IPS events, and unauthorised access attempts. IPS and firewalls are examples of tools that actively check traffic for validity.
Configuration Management and Enforcement: Device settings can be monitored for “drift” (differences from an ideal state) by automated technologies, which can also automatically reconfigure equipment to ensure consistency and alert workers.
Network Discovery and Documentation: In order to create and update network topology maps, protocols like CDP and LLDP, as well as network management tools like DNA Center, help automatically discover devices, their capabilities, and their connections. This is especially important when there is little or missing documentation.
Lifecycle Management: It supports every stage of a network device’s lifecycle, from initial installation (Day 0) to continuous monitoring and modifications (Day N).
Automation: By formalizing data models, centralised controllers increase management efficiency by providing network data to automation scripts through APIs.
Network Device Monitoring Disadvantages
Network monitoring might have disadvantages despite its many benefits.
Security Vulnerabilities: Older versions of SNMP (v1 and v2c) are vulnerable to sniffing attacks since they send community strings (passwords) in clear text. Authentication and encryption are provided by SNMPv3 to lessen this.
Resource Consumption:
- Debug Commands: Cisco IOS debug commands are only appropriate for short-term troubleshooting and can use a lot of router CPU resources. They are not appropriate for continuous monitoring.
- IPS Latency and Single Point of Failure: Traffic forwarding may be slightly delayed by Inline Intrusion Prevention Systems (IPS) because of thorough packet inspection. Additionally, a single point of failure might bring down an entire network section if an inline IPS sensor malfunctions without a backup route.
Cost and Licensing: Selective monitoring of only important components might result from the high cost of comprehensive NMS and NCM solutions, particularly those that charge per monitored element (such as interface).
Complexity: It can be difficult and require specialised staff to implement and maintain advanced monitoring systems, especially in multi-vendor setups or big, complicated networks.
Alert Fatigue: Low-quality monitoring systems may produce a lot of notifications, which might cause “alert fatigue” in which important warnings are lost in the shuffle.
Network Device Monitoring Applications
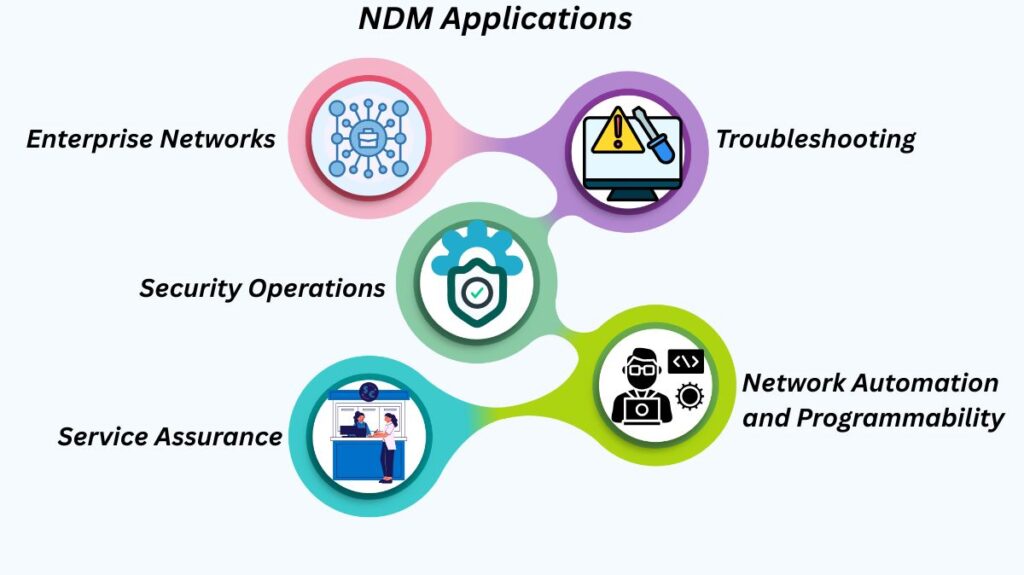
Network device monitoring is used on networks of all sizes:
Enterprise Networks: From major campus and data center networks to small office/home office (SOHO) networks, monitoring guarantees the availability and performance of vital services.
Troubleshooting: It offers crucial information for diagnosing and fixing network issues, ranging from straightforward connectivity difficulties (using ping) to intricate routing or application performance issues (using NetFlow, NMS graphs, and DNA Center Path Trace).
Security Operations: The detection and mitigation of security risks such as malware or unauthorised access depend heavily on firewalls, intrusion prevention systems, and log monitoring using Syslog or SNMP traps.
Network Automation and Programmability: For a variety of automated operations, such as dynamic configuration deployment and Day 0 installation assistance (Plug and Play) for new devices, controllers such as Cisco DNA Centre employ monitoring data. Configuration drift is identified and corrected by configuration management technologies using monitoring.
Service Assurance: Monitoring tracks measures such as availability, throughput, and reaction time to help ensure that the network is fulfilling its service level agreements (SLAs).
Traditional vs. Controller-Based Monitoring
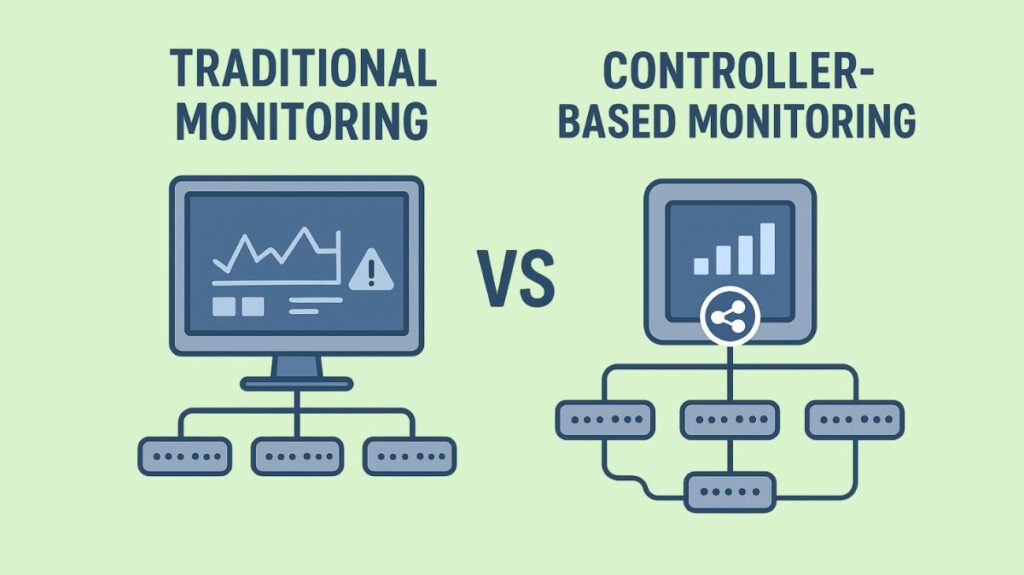
Individual device setups and polling protocols like SNMP are key components of traditional monitoring. With the use of sophisticated features like “network time travel” (which displays historical client performance) and AI-driven troubleshooting guidance, modern controller-based networks (like Cisco DNA Centre) centralise a large portion of monitoring, data collection, and analysis.
| Feature | Traditional Monitoring | Controller-Based Monitoring |
| Architecture | Decentralized; each device is managed individually. | Centralized; a single controller manages multiple devices. |
| Configuration | Manual and device-by-device. This can be time-consuming and prone to errors. | Automated and policy-driven. The controller pushes configurations to devices, ensuring consistency. |
| Scalability | Challenging; adding new devices often requires manual configuration and significant infrastructure upgrades. | Highly scalable; the controller can easily onboard and configure new devices automatically. |
| Data Collection | Often relies on periodic polling (e.g., using protocols like SNMP) which can be slow and result in delayed insights. | Real-time and comprehensive. The controller provides a global view of the network’s state. |
| Problem Resolution | Slow and reactive. Troubleshooting requires manually checking logs and connecting to individual devices. | Fast and proactive. The controller provides real-time alerts and a unified dashboard for quick diagnostics. |
| Security | Security policies are managed individually on each device, which can lead to inconsistencies. | Policies are enforced centrally by the controller, ensuring uniform security across the network. |
| Operational Costs | High due to the need for a large team of network engineers with deep CLI experience. | Lower due to automation and a GUI-first approach, allowing a smaller team to manage the network. |
| Example | Using Telnet/SSH to manually configure each router and switch. | Using a Software-Defined Networking (SDN) controller to manage network policies and configurations from a single interface. |
