Amplification Attack
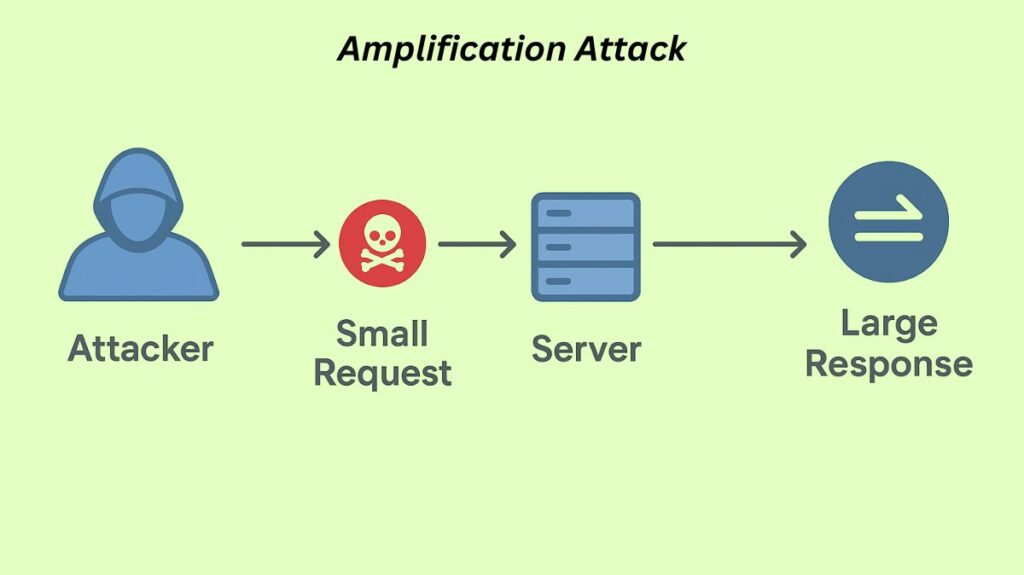
A distributed denial-of-service (DDoS) attack, known as an amplification attack, occurs when a hacker uses flaws in network protocols to submit a small, fake request that gets a significantly bigger response, overwhelming a victim’s network with traffic. DNS, NTP, and Memcached attacks are examples of common amplification attacks in which the attacker uses the victim’s spoof IP address to make a short query to open DNS, NTP, or Memcached servers, causing the servers to respond to the victim with abnormally large responses.
Using susceptible third-party servers (sometimes referred to as “reflectors”) to greatly increase their original malicious traffic is the attack’s main characteristic. This implies that the attacker needs relatively little bandwidth of their own to start a potent, high-volume attack.
You can also read What Is Smurf Attack Meaning? How It Works, And Prevention
How Amplification Attack Works
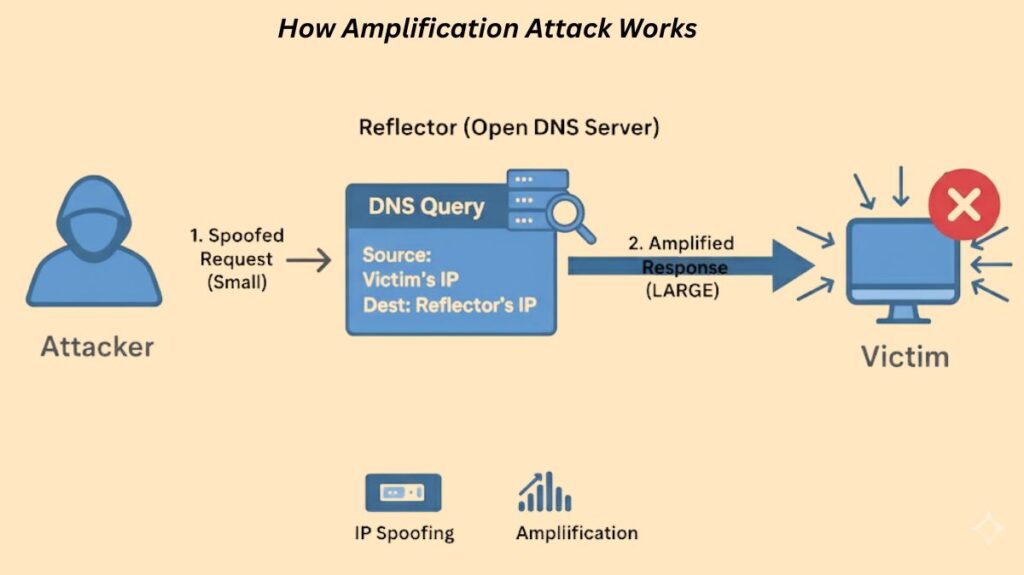
Using IP spoofing and a difference in response size, the amplification attack is a three-party procedure that involves the attacker, the reflector, and the victim.
IP Spoofing
The attacker initiates the attack by sending a brief, carefully constructed request to a server that is open to the public and serves as the reflector. IP spoofing is a crucial phase in this process, when the attacker substitutes the targeted victim’s IP address for the source IP address in their request.
Amplification
The purpose of the request made to the reflector is to elicit a considerably more extensive response. This is the attack’s “amplification” stage. In order to get the biggest response, attackers frequently format their requests (for example, requesting “ANY” DNS records).
Reflection
After receiving the spoof request, the reflector server sends the huge answer back to the victim, assuming it came from the victim’s IP address. The attacker can create a massive flood of data aimed at the victim by repeating this procedure over multiple reflector servers, which will result in a denial-of-service attack.
Attack traffic is frequently hard to identify and stop since it comes from trustworthy, high-bandwidth sources.
The Amplification Factor
The efficacy of an amplification attack depends heavily on the amplification factor.
- The ratio of the size of the reflector’s answer to the size of the attacker’s original request is known as the amplification factor.
- For example, the amplification ratio is roughly 67x (or 66.7) if an attacker sends a 60-byte request that results in a 4,000-byte response. This indicates that the attacker causes roughly 67 bytes of traffic to the victim for every byte they send. Amplification factors of thousands of times can be attained by certain methods.
Common Protocols Used
Because UDP is a connectionless protocol without a three-way handshake, which makes it simpler to spoof IP addresses, amplification attacks commonly target protocols that depend on it.
Common protocols abused as amplification vectors include:
- DNS (Domain Name System) Amplification: DNS (Domain Name System) amplification is a common technique that targets open DNS resolvers that are available to the general public. Attackers send a brief DNS query that generates a massive, detailed response, frequently with an amplification factor of up to 70x (for example, a request for “ANY” records, which provides all known zone information).
- NTP (Network Time Protocol) Amplification: Attackers typically use commands like monlist, which can provide a list of the last 600 hosts that connected to the server, to take advantage of NTP (Network Time Protocol) servers. This results in a response that is hundreds of times larger than the request.
- Memcached Amplification: Reflects and amplifies high UDP traffic volumes by abusing insecure Memcached servers (key-value stores used for caching).
- SSDP (Simple Service Discovery Protocol): Internet of Things devices use the Simple Service Discovery Protocol (SSDP), which can be used to leverage a tiny discovery query to provide a significant answer.
- Other Services: Other services that might return larger replies than the request include CLDAP, Chargen, SNMP, RIP, and LDAP.
Mitigation and Prevention Strategies
Defending against these attacks requires a multi-layered approach involving ISPs, network operators, and potential victims.
- Source IP Verification (Egress Filtering): Internet service providers (ISPs) and network operators should use egress filtering. By taking this crucial precaution, their clients are stopped from sending out packets that contain forged source IP addresses. By putting Best Current Practice (BCP) 38/84 into practice, the likelihood of most DDoS assaults that use IP source address spoofing is significantly decreased.
- Restricting Reflectors: Recursion should be disabled for external queries or restricted to authorized clients only on servers that are susceptible to being used as reflectors, such as DNS servers. A DNS resolver is a poor vehicle for amplification attacks if it only uses reliable sources.
- Response Rate Limiting (RRL): Services can be set up to transmit a maximum of one response to a client per second. By limiting the volume of traffic originating from any one server, this feature lessens the potency of amplification assaults.
- DDoS Protection Services: Before the vast amount of bad data reaches the target’s network architecture, potential victims might make use of cloud-based DDoS mitigation or scrubbing services, which are made to absorb and filter it.
You can also read What is IP Spoofing Attack and How IP Spoofing Works
