Role-based access control (RBAC) was discussed in detail, including how RBAC works, the fundamental principle of least privilege, types of RBAC models, advantages and disadvantages of RBAC.
Role-based access control(RBAC)
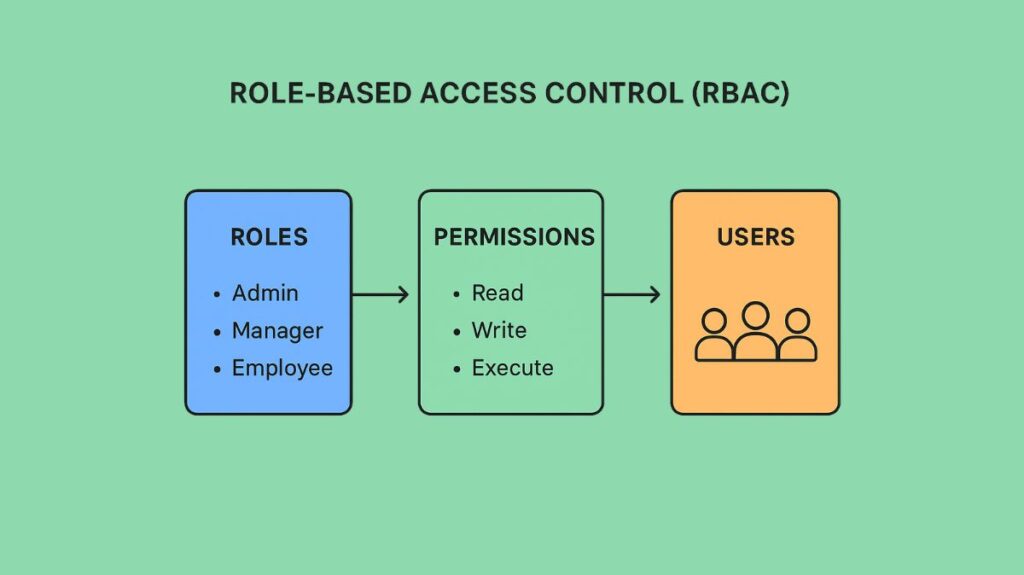
A security technique called role-based access control, or RBAC, limits system access and permissions to authorised users according to their predetermined organisational roles rather than their personal identities. By giving roles rights that users then inherit, it makes security administration easier and guarantees that people only access resources and carry out tasks required for their particular occupations. Improved data protection, easier user administration, and lower security risks through adherence to the least privilege principle are some of the main advantages. Another name for it is role-based security.
Also Read About How ABACs Work & Attribute Based Access Control Components
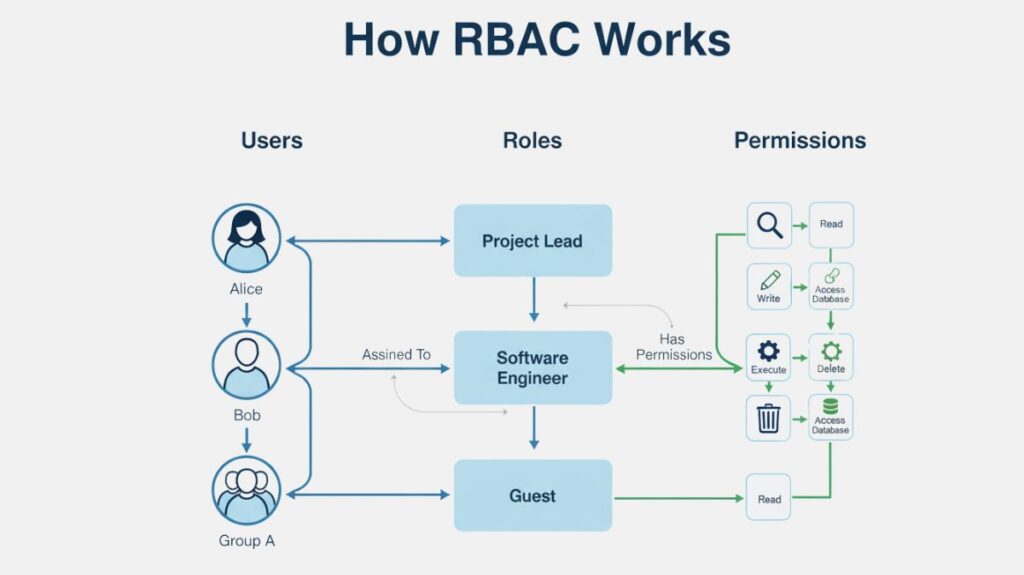
How RBAC Works
RBAC’s core idea is to define roles and then associate people with those roles, which in turn inherit a set of certain rights.
Key Building Blocks of RBAC
- In essence, a role is a group of permissions that correspond to a job function, title, or general set of duties within the company (e.g., Admin, HR Manager, Software Engineer). Adding, removing, and modifying permissions is simpler with roles than when done separately. For instance, a “reader” position may simply be able to read articles, whereas a “marketing” role may be able to edit them.
- Specific rights or approvals to carry out an action on a resource, such reading, writing, editing, or removing data or files (e.g., distribute:newsletters, ViewEmployeeSalaries), are known as permissions.
- Users: Depending on their necessary job functions, people, services, or automated agents are assigned to one or more roles.
- The files, databases, programs, or system elements that are being accessed are referred to as resources or objects.
- Input, processing, output, storage, and control (such as altering system configurations) are all included in operations.
- Sessions: These are recorded for auditing purposes and specify the period of time a user accesses a resource.
Also Read About Types Of Access Control In Network Security: DAC, MAC & More
Model Relationship
These components usually have a many-to-many relationship:
- A user may be allocated to more than one role; for example, Jane is both a project lead and a software engineer.
- It is possible to assign a role more than one permission. For example, the SoftwareEngineer role has the ReadCode, WriteCode, and AccessTestServer permissions.
- A role can have more than one user assigned to it.
The system verifies the permissions linked to each user’s given role whenever they try to perform an action. Access is provided if any of their positions have the necessary authorization.
Example
| Component | Example | Permission Granted |
| User | Alice | Access to both |
| Role 1 | HR Specialist | ViewEmployeeSalaries |
| Role 2 | Payroll Processor | UpdateEmployeeBankInfo |
| Permission | ViewEmployeeSalaries | Alice can view salaries because she has the HR Specialist role. |
| Permission | UpdateEmployeeBankInfo | Alice can update bank info because she has the Payroll Processor role. |
Access Determination
The system verifies the roles that users have been assigned and gives them the appropriate rights when they log in. Since RBAC is an additive model, a user’s effective permissions are the sum of the permissions for all of their overlapping roles.
Three checks are made during the authorisation process to make sure access is linked to designated roles:
- Verify if the subject has chosen or been given a role by using role assignment.
- Role Authorisation: Confirms that the subject is permitted to play an active role.
- Permission Authorisation: Verifies that the subject’s active role is permitted with the necessary permission.
Foundational Principle of Least Privilege
The Principle of Least Privilege (POLP) is inherently enforced by RBAC. According to POLP, users should only be given the minimal amount of access required to carry out their particular job duties in order to reduce the possibility of abuse or error.
For instance, HR managers may be able to change employee information in an HR application, while other employees may only be able to view their own information.
Types of RBAC
Three RBAC levels are recognised by the NIST/ANSI/INCITS RBAC standard:
- Core RBAC: The basic approach that just considers roles, permissions, and users.
- Roles can inherit rights from other roles under hierarchical RBAC, which frequently reflects an organisational structure in which senior roles take over subordinate roles’ permissions.
- Restricted Separation of Duties (SoD) enforcement is one of the constraints added by RBAC. This stops one person from having two responsibilities that are mutually exclusive and that, when combined, could enable fraud or illegal activity (e.g., preventing one person from being both a Check Creator and a Check Signer).
- The goal of the fourth type, symmetrical RBAC, is to avoid the buildup of unnecessary access rights by routinely evaluating role permissions.
Advantages of RBAC
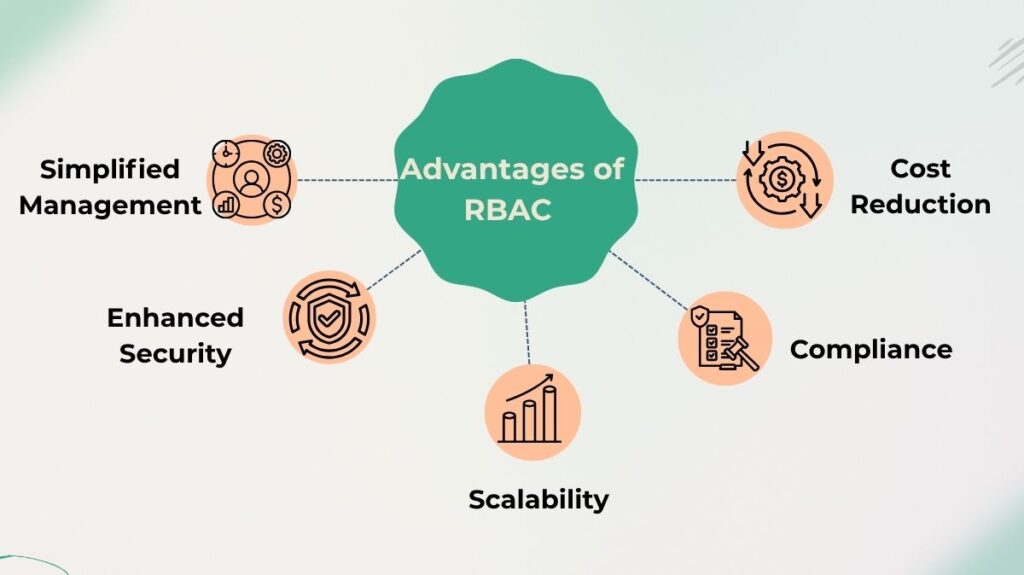
RBAC is commonly acknowledged by organisations as a best practice for controlling user privileges in an application or system. Important advantages include:
Simplified Management: When a user joins, switches departments, or departs, administrators can quickly update all of their access rights by assigning or modifying their role. This reduces the possibility of making a mistake while granting user rights.
Enhanced Security: RBAC reduces the risk of data breaches, malicious attacks, and insider threats by tightly matching permissions with job duties.
Scalability: Because administrators oversee fewer roles rather than thousands of individual user permissions, RBAC is very successful in large organisations and can be readily modified as access requirements change.
Compliance: RBAC facilitates auditing and proving adherence to legal and regulatory obligations for privacy and confidentiality (such as GDPR or HIPAA).
Cost Reduction: Organisations can save money on storage, memory, and network traffic by blocking unauthorised user access.
Also Read About Mandatory Access Control Advantages And Disadvantages
Disadavnatges of RBAC
Despite its effectiveness, RBAC has certain disadavnatges:
- Initial Complexity: To properly define all required roles and permissions, RBAC setup necessitates careful planning.
- Role Explosion: When too many distinct positions are defined in large, complex organisations, it can cause “role explosion,” which makes administration more difficult and undermines the goal of the system.
- RBAC may not always be adaptable if a user requires access outside of their designated function for a brief period of time (for example, a salesperson may require temporary billing permissions).
