What is Standard ACL?
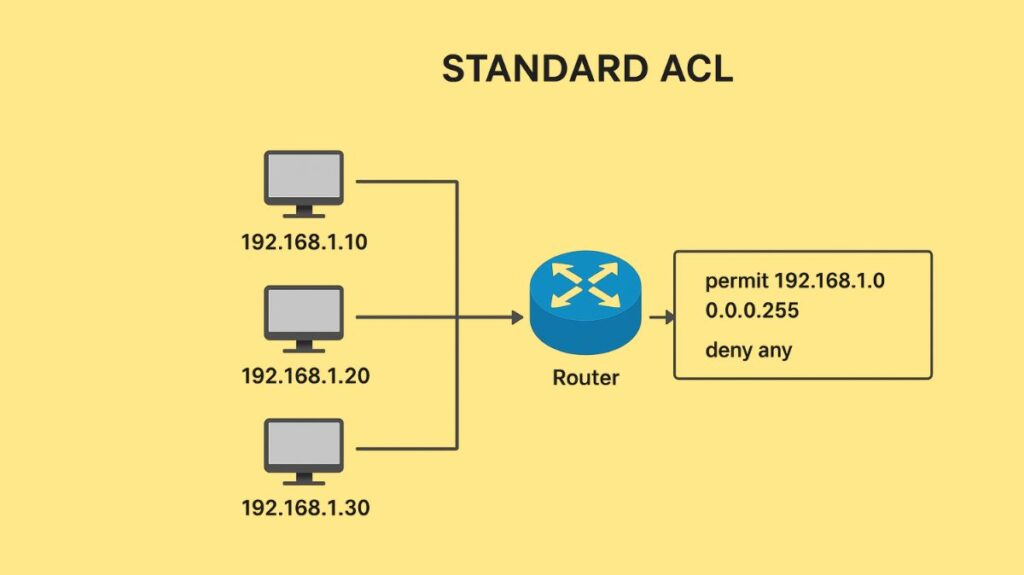
One essential and popular part of network security is a Standard Access Control List (ACL). In networking, it is the most basic kind of access control list. It is mostly utilized in routers to allow or reject packets according to specific standards.
Essential Features and Filtering Standards
Which traffic is permitted to move across a network is determined by standard ACLs. its filtering premise is its primary differentiator:
- Source IP Address Only: Conventional ACLs only use the packet’s source IP address to filter traffic. This criterion is the only one they look at.
- All or Nothing Filtering: They produce a “all or nothing” approach since they only take the source IP into account. All traffic (including all protocols and ports, like TCP, UDP, or ICMP) from a given source to all destinations is banned if a packet coming from that source is rejected.
- Lack of Granularity: Because Standard ACLs are unable to filter traffic according to the destination IP, protocols (such as TCP or UDP), or particular port numbers, they are less adaptable than Extended ACLs.
- Traffic Scope: They can filter traffic from a single host, a group of hosts within a subnet, or many subnets on the basis of a host IP address or a network IP address.
Also Read About Advantages And Disadvantages Of Discretionary Access Control
Types and Numbering
There are two methods to configure standard ACLs: naming or numbering:
Numbered ACLs
These make use of a particular range of numbers. Both the enlarged range of 1300 through 1999 and the common range of 1 through 99 are used. The inability to add or remove rules separately without deleting and recreating the complete list is a drawback of numbered standard ACLs.
Named ACLs
The administrator may give these any name they like. Individual rules can be deleted with flexibility when using a named ACL.
Placement and Flow of Traffic
A standard ACL’s wide range of filtering criteria makes its location essential:
- Suggested Location: Generally speaking, standard ACLs should be positioned as near to the target as feasible.
- Reasoning: By positioning them near the destination, the blanket filter’s effect which blocks all traffic from a source IP is lessened, avoiding the unintentional blockage of valid traffic that is meant for other areas of the network.
- Application: Both incoming and outgoing traffic can be subject to a standard ACL that is set up on an interface. In order to apply the ACL, the traffic’s direction (inbound or outbound) must be specified. For instance, the ip access-group 5 command applies access list 5 to the interface’s incoming traffic.
Also Read About How ABACs Work & Attribute Based Access Control Components
Processing Rules
Standard ACLs and all other ACL types adhere to certain processing guidelines:
- Sequential Processing: Beginning with the first line and working down, the router examines each entry in the access list one after the other.
- First Match Wins: The router takes action and halts ACL processing for a packet when it matches an entry (either a permit or a deny statement).
- Implicit Deny: At the conclusion of any ACL, regardless of type, is an implicit deny all statement. A packet is automatically banned (denied) if it does not match any expressly specified permit or refuse instructions. You must so include at least one explicit permit statement in order to permit any traffic.
Configuration Summary of Standard ACL
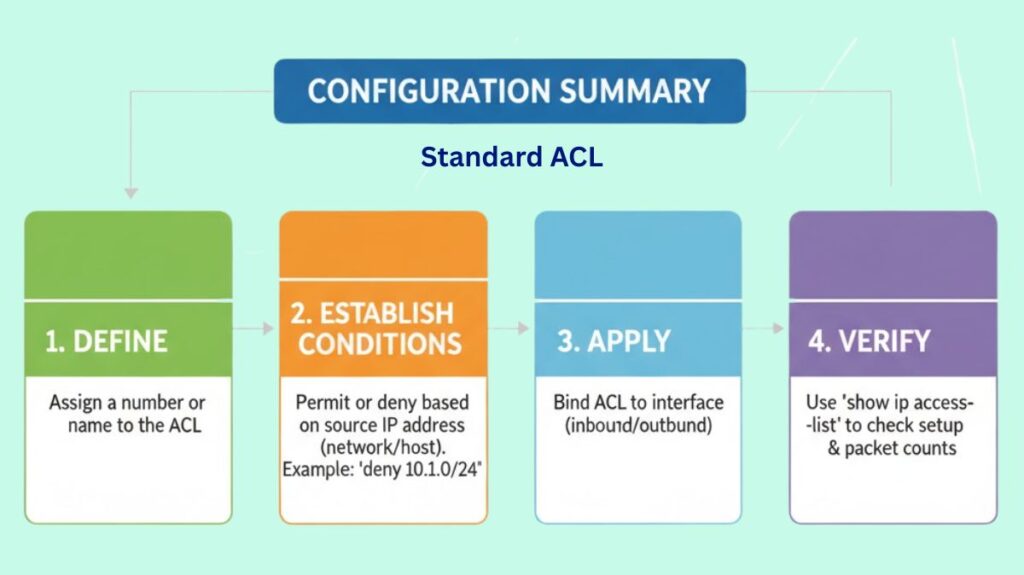
Setting up a Standard ACL entails applying the list and specifying the filtering conditions:
- Define: Give the ACL a special number or name.
- Establish Conditions: Determine whether to grant or refuse access based on a range of IP addresses, which can be either a network address or a single host. 5 deny 10.1.1.0/24 is an example entry that blocks all traffic from that network.
- Apply: In the incoming or outbound direction, connect the ACL to a particular network interface.
- Verify: To check the setup and track the number of packets that match the rules, use commands like show ip access-list or show access-list.
Use Cases and Advantages
Standard ACLs are frequently used for traffic monitoring and control. Among their applications are:
- By permitting or prohibiting communication from particular IP addresses, you can manage which devices have access to a network.
- Putting in place fundamental security procedures to limit access to sensitive resources and block undesirable traffic.
- Limiting FTP traffic to specific IP addresses or email traffic to specific networks.
- Their effectiveness in filtering based solely on the source IP improves network performance.
- They need no processing overhead on the router and are easy to set up.
Cisco ASA Specific Context
It is crucial to remember that Standard ACLs have a specific purpose within the Cisco ASA and cannot be used to directly manage traffic on interfaces. Rather, OSPF routes’ target IP addresses are identified on the ASA using Standard ACLs, which can also be used in a route map for OSPF redistribution. In this case, the deny keyword will prevent a packet from passing through the ASA.
Also Read About Advantages And Disadvantages Of Discretionary Access Control
