NAT table explained
A crucial data structure kept up to date by a NAT-enabled device (usually a router or firewall) to monitor current connections and their address and port translations is the Network Address Translation (NAT) table, sometimes referred to as the translation table or NAT binding table.
The central component of the entire NAT function is thought to be the NAT table. Storing the dynamic or static mappings required to convert secret, nonroutable internal addresses into routable public addresses is its main purpose.
NAT translation table example
| Inside Local (Private) | Inside Global (Public) | Outside Global (Destination) | Protocol | Port Mapping |
|---|---|---|---|---|
| 192.168.1.10:1030 | 203.0.113.5:50001 | 142.250.190.78:80 (Google) | TCP | 1030 ↔ 50001 |
| 192.168.1.11:1040 | 203.0.113.5:50002 | 151.101.1.69:443 (GitHub) | TCP | 1040 ↔ 50002 |
| 192.168.1.12:1050 | 203.0.113.5:50003 | 172.217.3.110:80 (YouTube) | TCP | 1050 ↔ 50003 |
Purpose of Network Address Translation (NAT) table
The NAT Table is required for the following main NAT functions:
- The first and most important goal was IP address conservation. One globally unique public IPv4 address can be shared by numerous devices (each with a non-routable, private IP address, such as 192.168.1.x) thanks to NAT. The limited IPv4 address space was considerably slowed down as a result.
- Security/Privacy (IP Masquerading): The structure of the internal network is concealed from the public by translating the private IP address. Attackers on the internet cannot target individual devices on the private network directly since external systems only see the router’s public IP address.
- Removing Renumbering: When a network switches Internet Service Providers (ISPs), which may provide a new public IP address, it eliminates the requirement to renumber all internal hosts, making network administration easier.
How NAT Table Works
Every packet that crosses the line separating the public (Outside) and private (Inside) networks is subjected to a continuous, two-way procedure that is the NAT Table’s functioning mechanism. Port Address Translation (PAT), often known as NAT Overload, is the most popular type of NAT that makes use of the table.
Outgoing Traffic (Private → Public)
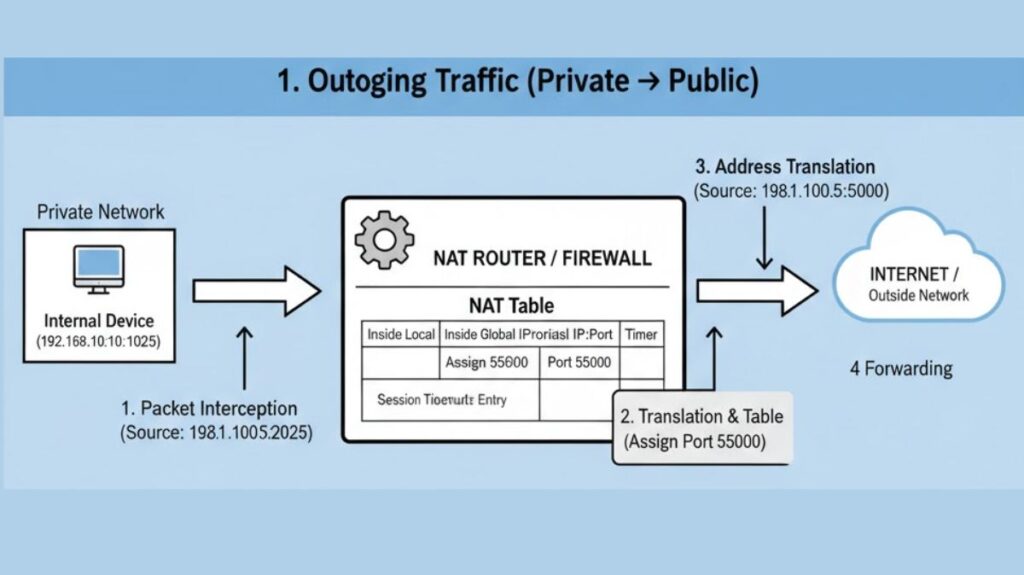
Packet Interception: Packet interception occurs when a packet intended for a public server (e.g., 203.0.113.2) is sent by an internal device (e.g., 192.168.1.10). The packet is intercepted by the router.
Translation Creation: The NAT Table is checked by the router. Given that this is a fresh relationship, it
- Captures the initial port and Inside Local address (e.g., 192.168.1.10:1025).
- Gives its own public IP address a distinct Inside Global port number, such as 198.51.100.5:55000.
Address Translation: The packet’s source address is changed from Inside Local (192.168.1.10:1025) to Inside Global (198.51.100.5:55000) by the router.
Forwarding: The internet receives the packet. The request appears to be coming from the router’s public IP (198.51.100.5) on the designated port (55000) to the external server.
Incoming Traffic (Public → Private)
Response Receipt: The router receives the response packet from the public server. The public IP address of the router and the particular translated port (for example, Destination: 198.51.100.5:55000) make up the destination address.
NAT Table Lookup: The router searches for a match on the Inside Global IP:Port by consulting its NAT Table. It discovers the entry that matches: 198.51.100.5:55000, which is the private host 192.168.1.10:1025.
Reverse Translation: The packet’s destination address is rewritten by the router from the Inside Global address to the original Inside Local address (192.168.1.10:1025) due to reverse translation.
Forwarding: The appropriate internal device receives the packet.
Session Management
Timeout: Each NAT Table entry contains a timeout value, sometimes known as a “session timer.” The record is automatically deleted from the table if there is no traffic for that particular connection within the timeout period. This controls memory and guarantees that there are only active links in the table.
Connection Closure: The router usually removes the item right away when a TCP connection is formally closed (using FIN/RST flags).
| Field Name | Example Value (Private Host) | Example Value (Translated/Public) |
| Protocol | TCP | TCP |
| Inside Local Address | 192.168.1.10 | N/A |
| Inside Local Port | 1025 | N/A |
| Inside Global Address | N/A | 203.0.113.5 |
| Inside Global Port | N/A | 50000 |
Key Components and Terminology
The show ip nat translations command is frequently used to see the four crucial address combinations that a full NAT table entry normally tracks:
| Term | Description | Address Type |
|---|---|---|
| Inside Local Address | The private IP address of a host on the internal network, used before translation. | Private (e.g., RFC 1918). |
| Inside Global Address | The valid public IP address used to represent the inside host when the packet exits the NAT device (the source address after translation). | Public/Globally Routable. |
| Outside Global Address | The actual destination IP address of the external host on the internet. | Public/Real Internet address. |
| Outside Local Address | The destination IP address as it appears to the internal network. This is often identical to the Outside Global address. | Varies. |
Additionally, the Protocol (such as TCP) and Port Numbers are typically included in entries. Because port numbers are mapped to distinguish distinct sessions from numerous internal hosts having the same Inside Global IP address, they are essential for Port Address Translation (PAT).
Also Read About What is IP Routing, How IP Routing Works, and Types
Entry Creation and Types
There are two primary categories of entries in the NAT table:
Static Entries:
- An inside local address and an inside global address have a permanent, one-to-one relationship defined by these explicitly established mappings.
- Without requiring any traffic to flow through the router, they are added to the translation table.
- For hosts that offer application services (such as mail or web servers), they are helpful since they make a permanent entry that shouldn’t ever be deleted because of a timeout.
Dynamic Entries:
- When a host on the inner network starts a conversation with the outside network, these entries are generated dynamically.
- When using dynamic NAT, the translation table is initially empty and is filled in as soon as the router receives traffic that has to be translated.
- In order to distinguish traffic from several internal hosts utilising the same internal global IP address, the NAT table stores the IP address mapping together with distinct port numbers for Port Address Translation (PAT) or Overloading.
Lifespan and Management
- Lifespan: As long as there is sporadic traffic, dynamic entries stay alive in the table.
- Timeout: The dynamically assigned address is returned to the pool and the dynamic item is removed from the NAT table after a defined time without translations. Cisco’s translation timeout averages 86,400 seconds, or 24 hours.
- Size and management of the NAT table influence performance. The device’s memory capacity determines the NAT session limit; most routing systems have adequate memory to accommodate thousands of translations. Smaller routers may encounter significant issues like ping reply delays and increased packet loss if the table is too large.
Management and Verification Commands
Network experts manage and check the NAT table using a variety of commands:
show ip nat translations: Displays the current active translations in the NAT table.clear ip nat translation *: Clears all dynamic entries from the NAT table (but does not remove static entries).show ip nat statistics: Lists counters for packets and NAT table entries, as well as basic configuration information.debug ip nat: Issues a log message describing each packet whose IP address is translated with NAT, allowing real-time monitoring.
Also Read About Cisco Basic Switch Configuration Commands step by step guide
