Site-to-Site VPNs are also known as
Site-to-Site VPNs are also known as router-to-router VPNs, network-to-network VPNs, and in some contexts, extranet-based VPNs or intranet-based VPNs. These names reflect their function of securely connecting entire networks at different locations, such as branch offices, rather than individual remote users.
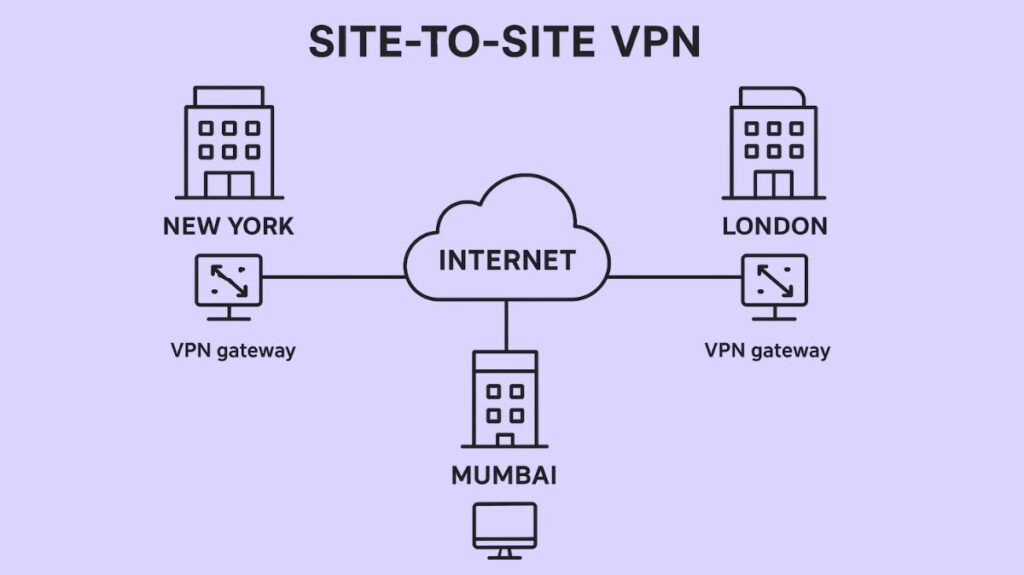
The technology known as a Site-to-Site Virtual Private Network (VPN) is intended to safely link two or more separate networks, sometimes called “sites,” over an unprotected public network like the internet. Site-to-Site VPNs can also be referred to as intranet VPNs or router-to-router VPNs.
Allowing devices on one private network to connect with devices on another remote private network as though they were on the same local network is the main purpose of a site-to-site virtual private network (VPN). This offers a more affordable option than pricey dedicated Wide Area Network (WAN) connections like Frame Relay or leased lines.
How Site-to-Site VPNs Work?
Site-to-Site VPNs use an encrypted tunnel to create a constant, secure connection between networks.
Key Components and Process:
VPN Gateways: A VPN gateway is required at the edge of every network that has to be linked. Usually, a network device like a router, firewall, or VPN concentrator serves as this gateway.
Encrypted Tunnelling (Encapsulation): A safe, encrypted tunnel is established over the public internet via the VPN gateways. The local VPN gateway does two things when data is transferred from a source site to a destination site:
- Encryption: To prevent unwanted access, the data is coded using a secret key into an unreadable format.
- Encapsulation (Tunnelling): Before being transmitted over the public internet, the encrypted original packet is encapsulated (added new headers) inside a new IP packet.
Decryption: The receiving Virtual private network (VPN) gateway decrypts the data and sends it to the designated resource within its local network once the encrypted traffic has arrived at its destination.
Always-On Connection: The Site-to-Site VPN tunnel endpoints continuously maintain the tunnel, in contrast to connections started by individual users. Once set up, this connection is “always-on” and users within the connected sites can communicate transparently; they don’t have to actively start the VPN.
Cloud Integration: Site-to-Site VPN offers an IPSec connection between an on-premises network and a Virtual Cloud Network (VCN) in cloud settings like Oracle Cloud Infrastructure. A Dynamic Routing Gateway (DRG) at the Oracle Cloud end, which serves as the virtual router into the VCN, and a Customer-Premises Equipment (CPE) object a virtual version of the on-premises device are needed for this configuration.
Also Read About Virtual Private Network Advantages And Disadvantages Of VPN
Protocols and Routing
Strong security mechanisms are necessary for Site-to-Site VPNs to guarantee data integrity, secrecy, and authentication.
- The most popular and standard security protocol for site-to-site virtual private networks is IPsec (Internet Protocol Security). Operating at Layer 3 of the OSI model, IPsec is a set of protocols that manages peer authentication (using digital signatures or pre-shared keys), encryption, and data integrity (using hashing/HMAC).
- IKE Phase 1 (for secure management between gateways) and IKE Phase 2 (the IPsec tunnel that secures user packets) are the two phases that typically comprise IPsec VPNs.
- Tunnel mode for IPSec, which encrypts and authenticates the entire data packet before encapsulating it into a new IP packet, is especially supported by Oracle Cloud Infrastructure.
- Further Protocols: GRE (Generic Routing Encapsulation) and SSL are further options for site-to-site VPNs. Because GRE is insecure, IPsec is frequently used to encrypt the GRE tunnel when it is utilised. Because of its efficiency and security, AES (Advanced Encryption Standard) is frequently suggested as the encryption standard.
- Routing: Two redundant IPSec tunnels are typically established while establishing a connection. Site-to-Site VPN routing can be set up with:
- BGP dynamic routing: The Border Gateway Protocol learns routes on the fly.
- Static routing: When setting up an on-premises network, specific routes are manually configured.
Types and Use Cases
Site-to-Site VPNs are divided into groups according to the companies they link to:
- Intranet-based Site-to-Site VPN: Creates a Wide Area Network (WAN) by joining many local networks (LANs) within the same company. This is frequently used to connect different regional or branch offices to a central headquarters.
- A corporation can safely connect its network with a partner or supplier to share particular resources while protecting the privacy of proprietary data by using an extranet-based site-to-site virtual private network (VPN).
Use Cases of Site-to-Site VPNs
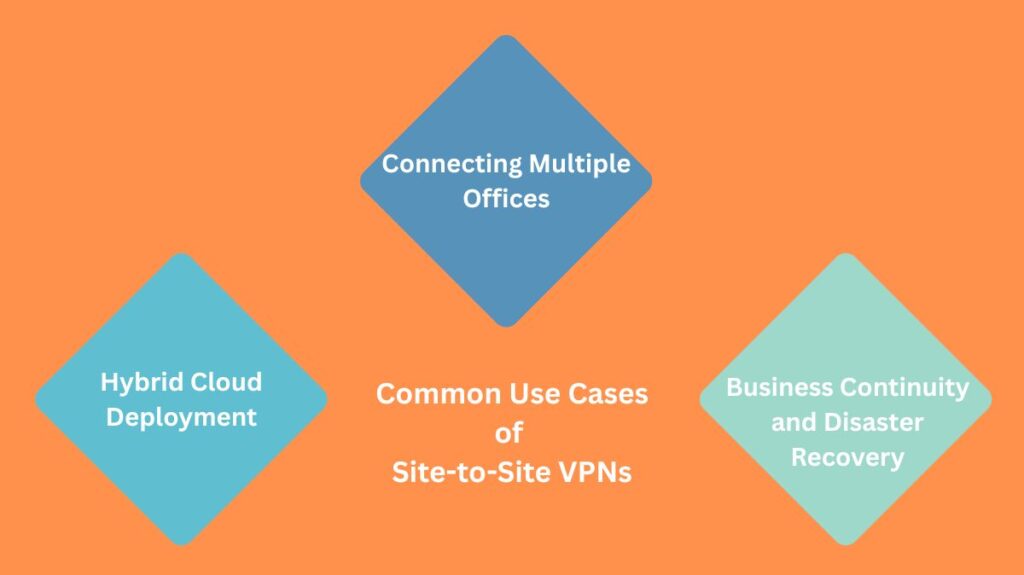
- Connecting Multiple Offices: Businesses connect their main office and branch offices so that staff members may safely access databases, servers, email systems, and shared resources from any place.
- Hybrid Cloud Deployment: Connecting an on-premises data centre to a virtual network in a cloud environment (such as Oracle, Azure, or AWS) is known as hybrid cloud deployment.
- Business Continuity and Disaster Recovery: Used as a backup connection for a primary private line or to facilitate safe data replication between primary data centres and disaster recovery locations.
Benefits and Drawbacks
Although site-to-site VPNs provide many organisational benefits, they can present certain operational drawbacks.
| Benefits | Drawbacks |
|---|---|
| Cost Savings Offers a cost-effective solution compared to leased lines by utilizing the public internet. | Complex Configuration Requires more complex initial configuration and ongoing management than Remote Access VPNs. |
| Enhanced Security Provides strong security through encryption, safeguarding data integrity and confidentiality over the internet. | Scalability Challenges Scaling can be complex, as adding new sites requires meticulous management of additional tunnels and may lead to performance inefficiencies. |
| Always-On Access The connection is permanent and readily available for all devices at the connected sites. | Inefficient Routing Traditional hub-and-spoke architectures can result in traffic passing through a central hub, leading to unnecessary latency. |
| Simplified Management Allows management of remote locations from a central office, facilitating security upgrades across the entire network. | Performance Dependence Performance depends heavily on the underlying internet connection stability and bandwidth. |
Also Read About Advantages And Disadvantages Of Packet Filtering Firewall
