In this article, we learn about what Secure Socket Layer Protocol is, the Key Functions of SSL, how Does SSL Protocol works, SSL Certificates, Components, and Protocols
What is Secure Socket Layer Protocol?
A security protocol called Secure Sockets Layer (SSL) establishes an encrypted connection between a client and a server to guarantee the safe and secret transfer of data, including credit card numbers and login credentials. SSL has been replaced by Transport Layer Security (TLS), which offers data integrity, privacy, and authentication for online communication, even though the name is still often used. This secure connection, which is made possible by an SSL certificate installed on a website, is visible to users through a “https://” URL and a padlock icon in their browser.
Netscape Communications Corporation is the developer of the Secure Sockets Layer (SSL) technology, which was made public in 1995 as SSL 2.0. SSL was created to create a secure, encrypted connection and guarantee safe network communication between two devices or apps.
The word “SSL” is still frequently used to refer to this technology or its replacement protocol, Transport Layer Security (TLS), even though SSL was superseded by the updated version.
You can also read What is the Cisco AnyConnect Secure Mobility Client in CCNA
Key Functions of SSL
Through three crucial methods, the SSL protocol’s main function is to guarantee safe communication over the internet:
- Encryption (Confidentiality): SSL jumbles data sent between a client (such as a web browser) and a server via encryption. By doing this, the material is protected from prying eyes and rendered unintelligible to those who intercept it. This safeguards private data, including credit card numbers, financial transactions, login credentials, and personal information.
- Authentication (Trust): Digital certificates (SSL certificates) are used by the protocol to verify the legitimacy of websites. By confirming the identity of the server this makes sure the client is connected to the authentic website and not a fake one.
- Data Integrity: To identify any manipulation or alteration during transit, SSL digitally signs transmitted data, frequently incorporating a Message Authentication Code (MAC).
How Does SSL Protocol Work: The Handshake
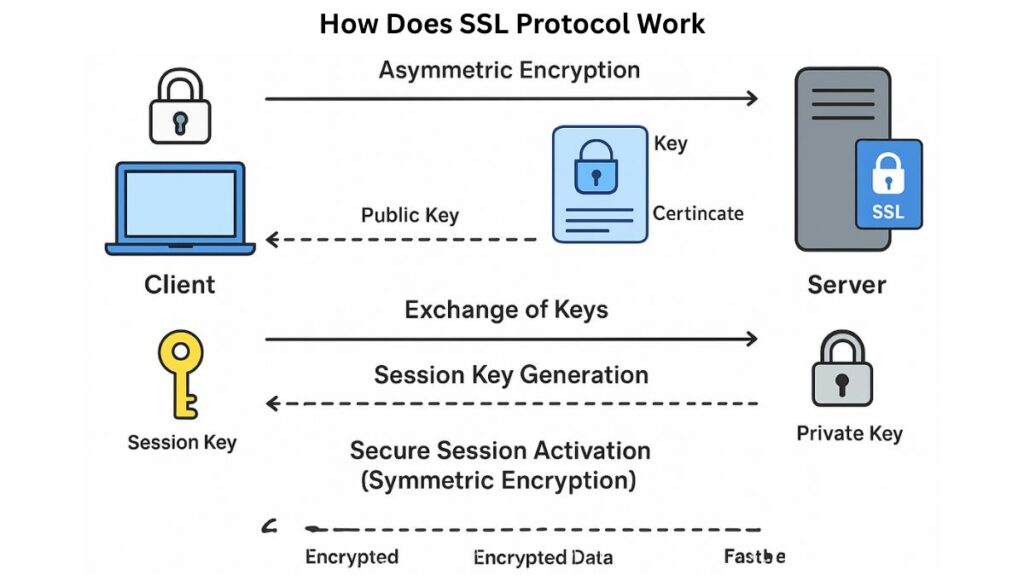
An SSL/TLS secure connection starts with a procedure known as the Handshake Protocol. The client and server exchange information and decide on the security keys and algorithms to be used for the session during this “security handshake.”
Asymmetric and symmetric encryption are both used in the handshake process:
- Asymmetric Encryption: Public key cryptography is initially used by the client and server. The server has two keys: a hidden private key and a public key that is made public by the SSL certificate.
- Exchange of Keys: The server sends its public key and SSL certificate in response to the client’s request for a secure connection. The customer checks the authenticity of the certificate with reputable Certificate Authorities (CAs).
- Session Key Generation: The client creates the session key, which is a special, one-time-use key. The client transmits this session key to the server after encrypting it with the public key of the server.
- Secure Session Activation (Symmetric Encryption): The server decrypts the message and retrieves the session key using its private key. Now that all parties have the same Session Key, all upcoming data is encrypted and decrypted using a symmetric encryption technique that is significantly faster. When the session ends, these session keys are discarded because they are just temporary.
You can also read Cisco WLC GUI Security Settings And Advanced WLAN Settings
Components and Protocols
The SSL protocol is composed of several sub-protocols:
- SSL Record Protocol: This ensures communication integrity and confidentiality. It breaks up application data, adds a MAC, compresses it if necessary, and then encrypts it with an SSL header before sending it.
- Handshake Protocol: The SSL session is established, and the client and server are authenticated via the Handshake Protocol.
- Change-Cipher Spec Protocol: By using the Change-Cipher Spec Protocol, the cryptographic parameters that were agreed upon during the handshake should be activated.
- Alert Protocol: This conveys problems or warnings pertaining to SSL. SSL employs two alert message types: fatal (serious faults necessitating connection termination) and warning (non-critical concerns). Interestingly, SSL alerts are not encrypted.
SSL Certificates and HTTPS
A website must install an SSL certificate, a data file that contains the public key and website identity, on the origin server after obtaining one from a Certificate Authority (CA) to deploy SSL/TLS.
When SSL/TLS is used to secure client-server communications, the resulting connection is referred to as HTTPS (Hypertext Transfer Protocol Secure). The “S” stands for secure. A website using HTTPS has an address starting with https:// instead of http://, indicating that communications are authenticated and encrypted.
Status and Replacement by TLS
SSL is an obsolete protocol that has been deprecated and has known security vulnerabilities.
- SSL was superseded by the more recent and improved TLS (Transport Layer Security) standard. In 1999, TLS 1.0 was developed as SSL 3.0’s replacement.
- SSL is no longer supported in any version. TLS versions 1.2 and 1.3 are the ones that are in use right now.
- “SSL” and “SSL/TLS” commonly refer to the current TLS protocol and TLS certificates because the last version of SSL (3.0) and the initial version of TLS (1.0) were closely related, and SSL had a strong name recognition.
You can also read WPA2 or WPA3: Wi-Fi Protected Access 3 security improvements
