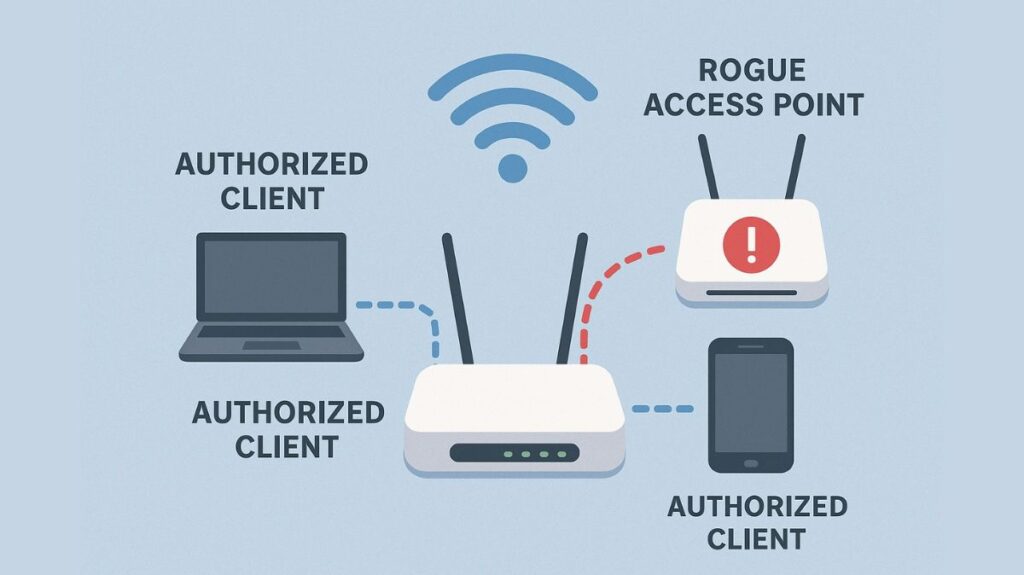
What is a Rogue AP?
Unauthorized wireless access devices that have been installed and linked to a private network without the network administrator’s knowledge or consent are known as rogue access points, or APs. Rogue APs create an unprotected “back door” into the wired and wireless business network by getting over existing security measures.
Rogue APs provide serious security threats, such as data breaches, network compromise, and regulatory compliance infractions, regardless of whether they are purposefully installed by attackers or unintentionally brought about by staff members.
You can also read Identity Services Engine Cisco Core Functions and Benefits
Origins and Types of Rogue APs
Rogue APs can come from a variety of sources and are frequently classified according to their goal and connection status:
- Unauthorized/Accidental APs (Internal Rogue APs):
- This is frequently the most common kind. In order to acquire a stronger signal or get over business security measures, they are usually set up by a well-meaning but ignorant employee, such as plugging in a personal Wi-Fi router or installing a “soft AP” on their laptop.
- Because it offers direct network access, an Internal Rogue AP that is physically connected to the company’s wired network is regarded as a high-priority danger.
- To share a wired network connection with wireless clients, a Soft Access Point (soft AP) can be formed on a Wi-Fi adapter (e.g., using Windows’ virtual Wi-Fi); if this is done without IT collaboration, it becomes a rogue AP.
- Malicious APs (Impersonating APs):
- Attackers purposefully place them in order to intercept data or initiate cyberattacks.
- Evil Twin Rogue APs: The purpose of evil twin rogue access points (APs) is to trick users into connecting by imitating the network name or Service Set Identifier (SSID) of a genuine corporate Wi-Fi network, giving the impression that the network is reliable. The term “rogue access point of the second kind” is occasionally used to describe the Evil Twin.
- External APs: Unauthorized APs that are found close by (such as a local coffee shop or parking lot) but are not a part of the company’s internal wired network are known as external APs. Users can still be tricked into connecting by them.
Key Security Threats and Dangers
The basic integrity of a secure network perimeter is compromised by rogue access points.
- Data Interception and Theft: An attacker can readily connect, intercept traffic (sniffing), and steal sensitive data, including login credentials, personally identifiable information, and financial information, because the rogue AP is unmonitored and probably lacks adequate security (such as robust encryption).
- Man-in-the-Middle (MitM) Attacks: Attackers intercept and alter user-network communication by using rogue APs, particularly Evil Twins. The attacker connects the victim to the desired network in a Pass-Through MitM AP scenario, but first skims sensitive data.
- Malware Propagation: Propagation of Malware: After gaining access through the rogue AP, an attacker might initiate attacks to infect corporate devices with ransomware, malware, or other harmful code.
- Bypassing Security Controls: Rogue access points (APs) allow unauthorized users to access the internal network by evading firewalls, security checks (such as posture assessment), and Network Access Control (NAC) solutions.
- Compliance Violations: Serious regulatory non-compliance with standards like as HIPAA, PCI DSS, and GDPR can result from the existence of unauthorized access points.
You can also read What is Simultaneous Authentication of Equals Explained
Detection and Mitigation Strategies
Strict policy enforcement and automated technology are necessary for an effective defence.
Detection Technologies
- Wireless Intrusion Detection/Prevention Systems (WIDS/WIPS): The main instruments for continuously searching the radio spectrum for unauthorized APs are Wireless Intrusion Detection/Prevention Systems (WIDS/WIPS). Real-time threat neutralization is possible with WIPS.
- Wired/Wireless Correlation: The system looks for authorized APs on a list and matches them with detected wireless MAC addresses (BSSIDs). Most importantly, it needs to determine whether the internal network switches have the wired MAC address of the unauthorized AP (On-Wire detection). Using this method, a suspected rogue is indicated by a green up-arrow on the On-Wire column.
- Dedicated AP Modes: There are certain detecting modes in which access points can function.
- By comparing MAC addresses detected over the air with those visible on the wired network, the AP’s Rogue Detector Mode focuses on identifying rogue devices.
- The AP can function as a dedicated sensor in Monitor Mode, looking for Intrusion Detection System (IDS) events and identifying rogue APs.
- Classification: To arrange found APs, network controllers enable classification rules. The initial state of an AP is Unclassified. After that, it can be noted as:
- Rogue/Malicious: Unauthorized APs that are connected to the wired network or pose a risk are considered rogue or malicious.
- Accepted/Friendly: For nearby APs that pose no security risks or for APs that are an approved component of the network.
Mitigation Actions
- Suppression/Containment: To stop users from connecting, the controller sends deauthentication messages to the rogue AP’s clients (who are pretending as the rogue AP) and to the rogue AP (who is posing as its clients) when suppression is enabled.
- Physical Isolation: Should a Wired Rogue AP be verified, the system may automatically allocate the device to a quarantined VLAN or command the switch port to shut down (port disable).
- Network Access Control (NAC): By ensuring that only authorized devices can connect, NAC keeps the AP from ever getting a wired connection.
- Policy and Education: Enforce a stringent, zero-tolerance policy against unapproved wireless devices and mandate that staff members receive training on the risks associated with rogue APs.
You can also read What is Split MAC Architecture, Functions, and Benefits
