What is EAP FAST?
A key EAP technique called EAP-FAST (EAP Flexible Authentication via Secure Tunneling) was created mainly by Cisco Systems to replace the outdated, less secure Lightweight EAP (LEAP). The serious security vulnerabilities in its predecessor were addressed by the design of EAP-FAST.
The main objective of EAP-FAST’s design was to offer the robust security and mutual authentication advantages of certificate-based techniques, such as EAP-TLS, without the difficult administrative burden of maintaining a complete Public Key Infrastructure (PKI) for each client device. The IETF standardized EAP-FAST.
You can also read What is EAP-TTLS, Characteristics, Advantages and Use cases
How it Works: The Protected Access Credential (PAC)
EAP-FAST uses a symmetric secret key technique known as a Protected Access Credential (PAC) to accomplish safe, certificate-free tunnel authentication.
- PAC as a Shared Secret: The PAC is a type of shared secret that is put on the client (supplicant) and created by the Authentication Server (AS).
- PAC Components: A PAC consists of up to three components:
- PAC-Key: During the initial stage of authentication, this pre-shared secret key is utilized to create the secure tunnel.
- PAC-Opaque: When establishing a tunnel, the authentication server is presented with a variable-length parameter called PAC-Opaque. In order to verify the client’s identity and authentication, the server interprets this.
- PAC-Info: Information of variable length that at least includes the PAC issuer’s authority identify. Additionally, it could include helpful but optional information, such as the PAC-Key lifespan.
- Security and Storage: PACs are client-distributed credentials for enhanced network authentication. Because persistent PACs are encrypted, kept in the registry, and linked to the host computer via the Microsoft Crypto API (CryptoProtectData), they cannot be duplicated and utilized on different computers.
The Three Authentication Phases
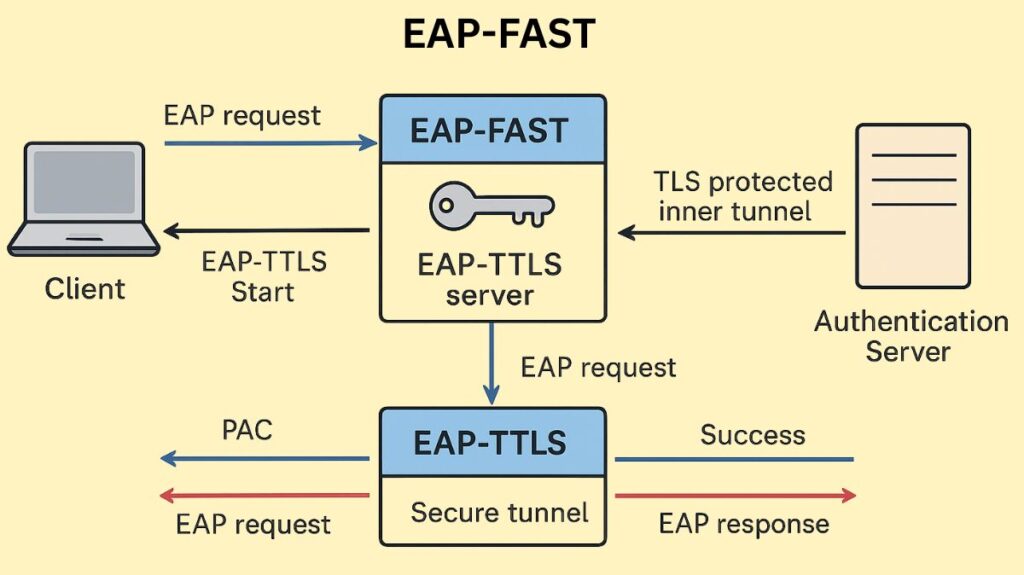
An initial setup phase comes before the two-phase tunneled authentication process used by EAP-FAST:
Phase 0: PAC Provisioning (Initial Setup)
The authentication server and the client must agree on a shared secret (the PAC) before the initial secure connection. The administrative overhead specific to EAP-FAST is as follows:
- The PAC: The PAC includes a server identity and a secret key specific to the client/server combination. The client safely stores the PAC after receiving it.
- Manual or Automatic: During the initial connection attempt, the PAC may be provisioned automatically (referred to as in-band provisioning) or manually. Automatic provisioning is frequently turned off and therefore less secure.
You can also read What is PEAP Protected Extensible Authentication Protocol?
Phase 1: Tunnel Establishment (Outer Authentication)
Every time the pre-shared PAC is used to establish a connection, this phase takes place.
- Mutual Authentication: A fast, cryptographic mutual authentication is carried out by the client and server using the PAC secret key.
- TLS Tunnel Creation: A secure TLS tunnel is immediately created between the client and the authentication server following a successful PAC authentication. The term “outer authentication” refers to this first procedure. During this stage, the TLS negotiation also includes server certificate validation.
Phase 2: Client Authentication (Inner Authentication)
The client’s real identity credentials are safely transmitted inside the encrypted tunnel after the protected tunnel has been created.
- Inner Method: The client authenticates inside this secure tunnel using a conventional mechanism, commonly EAP-GTC (Generic Token Card), which normally contains a one-time password or token along with the username and password. The term “inner authentication” refers to this secondary authentication that uses the user’s credentials.
- Protection: The credentials are shielded from man-in-the-middle (MitM) attacks and eavesdropping since they are transmitted over an encrypted tunnel.
Advantages of EAP-FAST
EAP-FAST is highly secure and offers several advantages:
- High Security: It effectively addressed LEAP’s serious security vulnerabilities. Because the protocol is immune to MitM attacks and the communication of weak credentials (such as a password) is impervious to eavesdropping, it is not susceptible to dictionary assaults.
- Certificate-Free Tunnel: Compared to EAP-TLS, it simplifies deployment by achieving strong mutual authentication and a secure TLS tunnel without requiring an X.509 certificate for each client device.
- Speed: The initial TLS handshake in Phase 1 is substantially quicker on future connections after the PAC is provisioned than the complete certificate exchange needed by EAP-TLS. The TLS extension (RFC 4507) is also supported by EAP-FAST, enabling quick re-establishment without preserving the server’s per-session state.
- Flexibility: MS-CHAP, LDAP, and One-Time Password (OTP) are just a few of the password authentication interfaces that it can handle within the tunnel.
Disadvantages of EAP-FAST
- PAC Management: Although certificates are made simpler, this creates a new administrative task: overseeing the PACs’ provisioning, storage, and lifetime.
- Vulnerability in Provisioning: The automatic (in-band) provisioning approach is frequently turned off since it is thought to be susceptible to specific attacks, which makes the manual rollout more difficult.
- Vendor Lock-in (Historically): Despite being a non-proprietary standard now, vendor lock-in was once closely linked to Cisco infrastructure, which resulted in less native support on older non-Cisco devices than PEAP or EAP-TLS.
Like other EAP-based techniques, EAP-FAST is based on the Extensible Authentication Protocol (EAP) framework and needs a RADIUS server that can operate as an EAP-FAST server in order to create the required PACs. The Wi-Fi Alliance has acknowledged its compatibility with 802.1X-based WPA/WPA2/WPA3 enterprise authentication options.
You can also read What is MSCHAPv2, How it Works & MSCHAPv2 Key Features
