Single Sign On
After successfully logging in only once with a single set of credentials, a user can access numerous separate software systems, applications, or services. Single Sign-On (SSO), a crucial authentication technique in network security. For Identity and Access Management (IAM) systems, SSO is an essential part. By consolidating all application logins into a single, safe verification point, it expedites the authentication process.
You can also read Benefits of SAML Security Assertion Markup Language
Purpose and Problems Solved
The need for users to regularly identify themselves across several locations inside a contemporary enterprise network, including databases, corporate websites, secured files, and personal folders, is the main issue that SSO attempts to solve.
Without SSO, users have to remember several passwords, which frequently results in bad security practices like writing down passwords, sharing them, or using weak credentials repeatedly a phenomenon called “password fatigue.”
SSO offers the following advantages to users and organizations by centralizing authentication:
- Increased Convenience and Productivity: By simply entering their login credentials once, users may access information more quickly and easily, which boosts productivity.
- Reduced Administrative Costs: It reduces the number of help desk password resets and the IT expenses related to keeping track of customers’ usernames and passwords.
- Enhanced Security: By encouraging users to use a single, strong password rather than recycling basic credentials, it improves security. Additionally, it offers a focal point for implementing uniform security and authentication guidelines.
How Single Sign-On Works (The Mechanism)
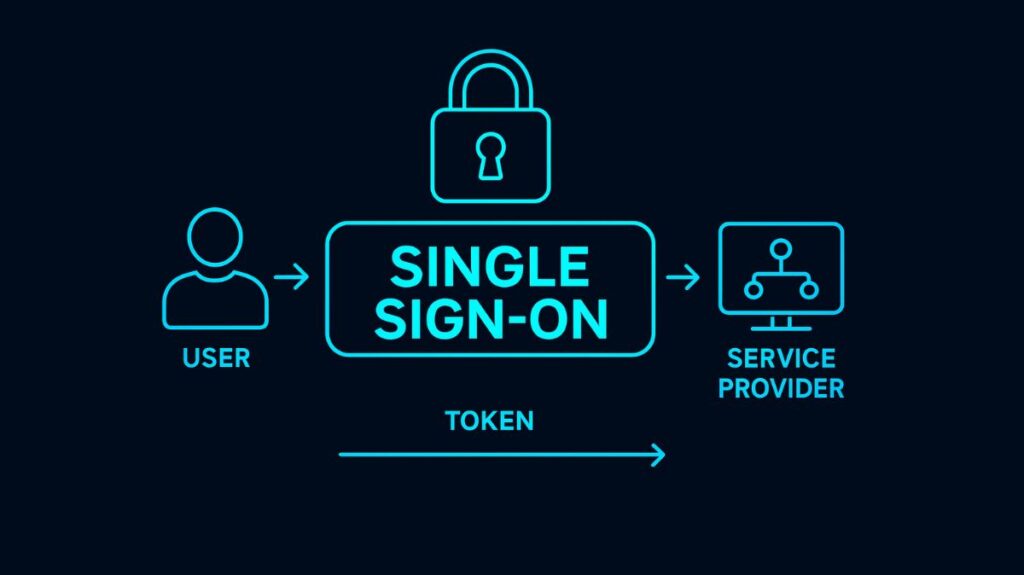
Establishing a trust connection between the Identity Provider and the Service Provider is how SSO works.
- Identity Provider (IdP) and Service Provider (SP): The program or website that the user tries to access is the SP. The centralized system in charge of establishing, maintaining, and confirming the user’s identification is called the IdP. SSO services serve as a middleman, verifying credentials against the IdP database without really controlling it.
- Initial Authentication: The SP sends the user to the IdP for authentication when they want to access the SP.
- Token Issuance: The IdP issues an access token or assertion once the user has successfully authenticated (for example, by logging into the domain).
- Token Function: This authentication token is a digital file that is kept on the servers of the SSO provider or in the user’s browser. It keeps track of every resource that the user is allowed to use. The token needs to be digitally signed in order for the receiving application to confirm its provenance.
- Access Granted: The application then verifies with the SSO service when the user tries to access any associated resource (folder, drive, website), and the SSO service provides the token to the app to authorize the request. The user is protected from having to enter several passwords by this token validation, which takes place in the background.
The domain controller in Windows NT Directory Services controls user access and keeps security account data in the Security Access Manager (SAM) database. The domain controller provides the access token when it has been validated against the SAM.
You can also read What is EAP AKA, How it Works, Advantages and Disadvantages
Common Technologies and Protocols
SSO is built upon secure standards and protocols:
| Protocol | Primary Use Case | Data Format | Purpose |
|---|---|---|---|
| SAML (Security Assertion Markup Language) | B2B/Enterprise SSO (Federation), browser-based SSO | XML (Assertions) | Exchanging authentication and authorization data |
| Kerberos | Internal Enterprise Networks, Windows Active Directory (AD) environments | Binary (Tickets) | Ticket-based authentication |
| OpenID Connect (OIDC) | Modern Web/Mobile Apps, Consumer-facing services | JSON (JWT Tokens) | Identity layer built on top of OAuth 2.0; provides authentication and authorization |
| OAuth 2.0 | API Access, Delegated Authorization | JSON (Access Tokens) | Token-based authorization |
Other related technologies that support SSO include Lightweight Extensible Authentication Protocol (LEAP) and EAP-FAST, particularly in Windows domain environments.
Key Security Risks and Mitigation
The Single Point of Failure (SPOF), also known as the “Bigger Blast Radius,” is a serious risk that SSO introduces despite its security benefits.
An attacker can access all apps associated with that account if the master login credentials are stolen or if the IdP system is hacked.
Security experts recommend requiring Multi-Factor Authentication (MFA) for SSO logins to reduce this risk. MFA significantly lowers the risks associated with compromised credentials by requiring users to give additional verification elements (such as a fingerprint or a code from a mobile phone) in addition to their password.
Other mitigation measures include:
- Risk-Based Authentication (RBA): If the login is thought to be dangerous, the IdP examines the login context (location, device) and initiates additional verification.
- Principle of Least Privilege: The least privilege principle states that users should only be granted access to programs that are absolutely required for their position.
- High Availability (HA): If the IdP fails, the system as a whole is shielded from a denial of service by deploying it with redundancy and failover.
Analogy: Single Sign-On can be compared to the digital stamp you get when you enter a special event. When you initially arrive at the entrance, you present your credentials to the Identity Provider, the main gate attendant, who confirms that you are permitted to be there. The attendant issues you a distinct, validated stamp (the authentication token) on your palm after verification. For the remainder of the night, the personnel at internal checkpoints, such as a particular VIP lounge (a service provider application), only check your stamp to verify that you were previously confirmed by the trusted attendant. They do not need your complete identification again.
You can also read What is EAP SIM, How it Works, Advantages and Disadvantages
