Attribute-based access controls (ABACs)
The authorization paradigm known as attribute-based access control (ABAC) bases access control policies on attributes such as resource, object, environment, and user attributes. ABAC creates access rules with if-then statements that specify the user, request, resource, and action using Boolean logic. Give the requester read-write access to financial data, for instance, if they are an accountant.
The more conventional Role-Based Access Control (RBAC) approach is thought to have evolved into ABAC. It offers real-time access control decisions that are dynamic, context-aware, and extremely fine-grained.
The US Federal Government has designated the adoption of ABAC as a Priority Objective, and the National Institute of Standards and Technology (NIST) has released standard guidelines outlining how to do so in an enterprise setting. Another name for ABAC is policy-based access control (PBAC).
Also Read About What Is A Baiting Attack And How Does Baiting Attacks Work
Key Components: The Four Categories of Attributes
By cleverly analysing how characteristics interact in a given environment and developing policies based on certain circumstances being met, ABAC security systems make judgements about access. Four primary categories of attributes are used in the creation of access policies:
- Subject/User Attributes: These characterise the person or thing making the attempt to obtain access. Among the examples are:
- Role, department, organisation, and job title.
- Location, age, user ID, and security clearance.
- Resource/Object Attributes: These specify the particular information, file, program, or system that is being sought. Among the examples are:
- Data sensitivity or categorization level (e.g., “confidential”), ownership, file type, and creation date.
- Action Attributes: These specify the precise action the user want to do on the asset. Among the examples are:
- Read, write, edit, remove, copy, view, transfer, or approve.
- Environmental/Contextual Attributes: These give the control a dynamic element by capturing the situation or environment in which the access request is being performed. Among the examples are:
- Date and time of day.
- Location (physical location, IP address).
- Device security status or device used.
How ABAC Security Works
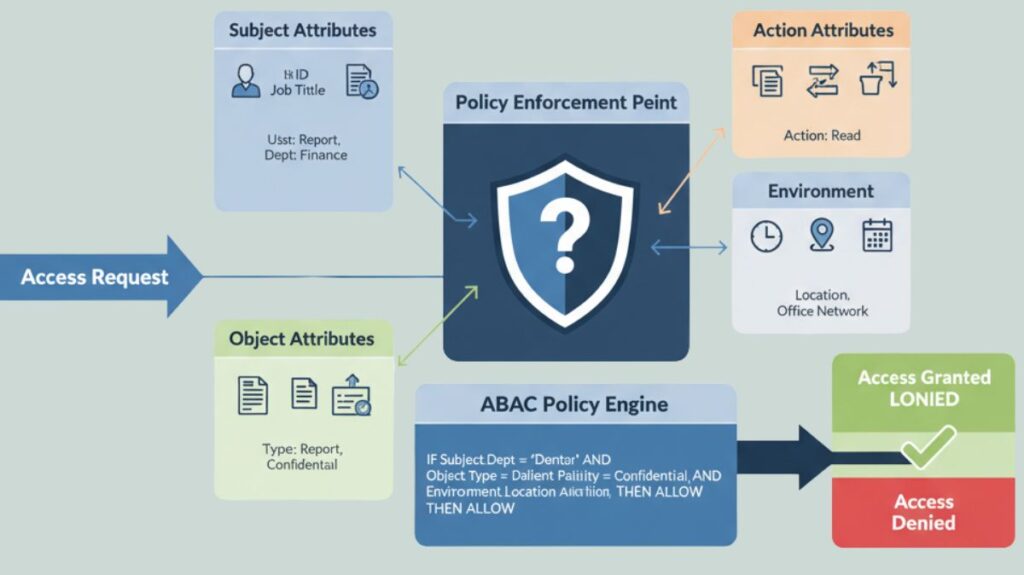
ABAC systems generate access rules that specify the requirements for the user, resource, and activity using Boolean logic, or if-then statements.
Usually, the procedure goes like this:
Access Request: An access request is made when a user (subject) tries to take action on a particular resource (object).
Attribute Collection: All pertinent attributes pertaining to the subject, object, action, and environment are gathered by the ABAC system. characteristics of the resource being accessed, including sensitivity, creation date, classification level, and file type.
Policy Evaluation: To determine which combination of attributes is necessary for a given action, the ABAC policy engine compares the gathered attributes to pre-established policies. The type of operation being requested, such as read, write, edit, delete, copy, etc. (e.g., “IF Subject.Department = ‘Finance’ AND Object.Sensitivity = ‘Confidential’ AND Environment.Time is ‘Business_Hours’ THEN ALLOW Action=’Read'”).
Access Decision: Access is either given or refused based on whether the qualities meet the policy requirements.
A policy might say, for instance, “permit read-write access to financial data if the requester is an accountant.” Or to put it another way: “A doctor may have access to a patient’s medical records only during their shift and only if they are in the hospital premises” .
Also Read About What Is DHCP Starvation Attack And DHCP Spoofing Attack
Advantages and Challenges
Advantages of ABAC
- Granular Control: ABAC evaluates several attributes under exact conditions to produce extremely specific access controls.
- Flexibility and Scalability: Without necessitating frequent revisions or reconfigurations, policies can be effectively scaled with organisational changes and dynamically adjusted.
- Context-Awareness: By making judgements based on context, taking into account environmental factors like time, place, and device improves security.
- Better Compliance: By establishing strict access controls and audit trails for sensitive data, ABAC makes compliance easier.
Implementation Challenges of ABAC
- Complex Policy Management: Because there are so many characteristics and requirements involved, creating and sustaining ABAC policies can be challenging, which raises the possibility of rules that contradict.
- Attribute Management: To guarantee the correctness and integrity of user, resource, action, and environmental characteristics, strong management is necessary.
- Performance Overheads: In high-volume settings, evaluating several attributes for each access request may cause performance problems.
- Integration: It might be difficult and resource-intensive to integrate ABAC with current infrastructure and achieve compatibility.
Notwithstanding the difficulties, ABAC is best suited for settings that are expanding quickly, big businesses with a large number of dispersed users, or institutions with complicated access requirements and strict security/compliance requirements (such as the government, healthcare, and financial sectors). Prominent cloud providers have included ABAC models into their identity and access management solutions, including Microsoft Azure and Amazon Web Services (AWS).
Also Read About How To Prevent Watering Hole Attack, Examples And Risks
