Authentication Header In Network Security
In the IP Security (IPsec) suite, the Authentication Header (AH) and the Encapsulating Security Payload (ESP) are the two primary protocols. The primary function of AH is to offer strong security services that are exclusively concerned with guaranteeing the integrity and authenticity of data for IP packets that are transferred between two systems.
IP Protocol Number 51 is used to identify AH.
Core Functions of AH
Several essential security services are provided by the AH protocol:
- Data Integrity: This guarantees that the packet’s contents haven’t been altered or tampered with during transmission. A message digest (also known as a cryptographic checksum) produced by an algorithm such as HMAC-SHA or HMAC-MD5 is used to guarantee integrity. The packet is rejected upon receipt if the computed hash values do not match.
- Data Origin Authentication: This confirms that the packet’s sender is who they say they are. By creating the message digest with a shared secret key, data origin authentication is guaranteed.
- Optional Anti-Replay Protection: This service guards against a packet being intercepted by an attacker and then retransmitted. A sequence number field in the AH header is used to offer replay prevention. Each packet delivered causes this unsigned 32-bit counter to rise by one, preventing duplicate messages from being accepted.
Alos Read About IPsec VTI: What is IPsec Virtual Tunnel Interface & Benefits
How AH Works
By computing and appending a cryptographic checksum, sometimes referred to as the Integrity Check Value (ICV) or Authentication Data, inside the IP packet header, AH accomplishes its security objectives.
- Calculation: By applying a cryptographic hashing technique (such HMAC-MD5, HMAC-SHA, or HMAC-SHA256) on the packet, the sender determines the ICV. Data origin authentication is ensured by this procedure, which generates the message digest using a shared secret key.
- Coverage: The entire IP packet, including the payload and outer IP header, is usually authenticated by AH.
- Exclusions: It specifically leaves out IP header information like the Time To Live (TTL) field and hop count that are allowed to be altered by intermediary network devices while in transit.
- Verification: Using the shared key and agreed-upon algorithm, the recipient carries out the identical computation. The packet is acknowledged as authentic if the newly calculated ICV matches the ICV in the received AH header; if not, it is rejected.
AH Operation Modes
Two modes that specify which portions of the packet are authenticated are supported by AH:
- Tunnel Mode: AH examines the complete packet, which is enclosed in a fresh IP packet.
- Transport Mode: Only the payload is checked by AH. The transport-layer protocol header (such as TCP or UDP) and the original IP header are separated by the AH header.
Important Restrictions and Status
What distinguishes AH is what it does not offer in particular:
- Lack of Confidentiality: The AH protocol does not offer packet encryption or data confidentiality. It is thought that using AH by itself offers insufficient protection.
- In general, AH and Network Address Translation (NAT) devices are incompatible. By changing the IP header (most especially, the IP address) to remap addresses, a NAT device renders the AH hash (ICV) invalid when it reaches the recipient, discarding the packet.
- Status Obsolete: AH is regarded as an outdated technique and its use is discouraged. According to NIST guidelines, AH is no longer advised and its usage is discouraged. Since ESP may perform the same integrity functions as AH, deployments are advised to switch to the ESP protocol utilising null encryption (ESP-NULL) or AES-GMAC when encryption is not desired.
Also Read About Advantages And Disadvantages Of Packet Filtering Firewall
Comparison with ESP
AH differs from Encapsulating Security Payload (ESP), the other primary IPsec protocol:
| Feature | Authentication Header (AH) | Encapsulating Security Payload (ESP) |
|---|---|---|
| Confidentiality (Encryption) | No | Yes (Primary Feature) |
| Data Integrity/Authentication | Yes | Yes (Optional) |
| Header Coverage | Authenticates most of the IP header and payload. Authenticates the outer IP header. | Authenticates only the IP datagram portion (inner packet) when configured for authentication. |
| NAT Compatibility | Incompatible | Compatible |
IKEv2 does not support AH+ESP, which is a mix of the ESP protocol for encryption and the AH protocol for authentication. This mode is no longer advised because it provides no benefit above standard ESP with authentication.
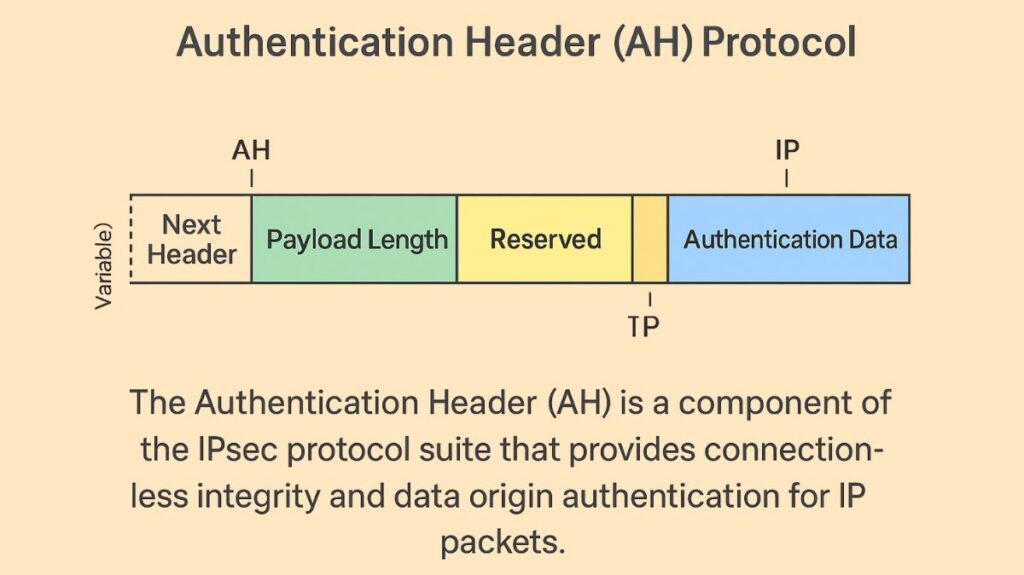
AH Header Components
The following fields are essential to the AH packet structure’s operation:
- A 32-bit feature called the Security Parameter Index (SPI) allows each packet associated with the current connection to be uniquely identified (Security Association).
- Sequence Number: Replay attacks are prevented using a 32-bit counter.
- Next Header: An 8-bit field that indicates the kind of header (such as TCP or IPv4) that comes after the AH.
- Authentication Data (ICV): A variable-length field used to confirm the integrity of transmission that contains the Integrity Check Value produced by the hashing algorithm and secret key.
- Payload Length: The length of the AH is represented by an 8-bit field.
Data integrity is protected by methods like HMAC-SHA and HMAC-MD5. Various HMAC-SHA2 variations (256, 384, and 512), HMAC-SHA1, and HMAC-MD5 are examples of potential authentication techniques.
Also Read About What Is iBGP? Features, Advantages & How To Configure iBGP
